27.10.2022 - Git open-source software is often used by software developers for the management and version control of software source code. These version control tools make work easier and are very practical, but too careless and negligent use can pose a security risk and endanger the confidentiality of sensitive data. A look at Swiss websites shows that insufficiently protected .git folders constitute a real risk in Switzerland.

Software developers have always faced the challenge of being able to work together on a project, and not just since the COVID-19 pandemic. Ideally, such collaboration takes place simultaneously and from various locations around the world. With the help of version control tools, several developers can work on a central software code and make changes. Updates to the code are logged transparently and the different versions of the code are visible in a history. Git is probably the best-known and most widely used tool for version control and was started by the software developer Linus Torvalds as open-source software. However, there are numerous other software products for version control, such as Mercurial, Apache Subversion, CVS and BitKeeper.
The danger of poorly protected .git folders
If .git folders are incorrectly configured or insufficiently protected, data can be publicly accessed on the internet with just a few clicks. Possible causes for insufficient protection include human errors by IT administrators or developers, as well as shortcomings in the creation of a new development project. When starting a new project, an existing folder is often simply copied without paying close attention to which data sets it contains and how they are protected. For the management and tracking of versions, Git and other tools use a special data folder in the respective directory: in the case of Git, this is the .git folder. This folder contains both the complete software source code, e.g. for an application or website, and all previous versions and changes, and potentially also configuration files with sensitive system information that needs to be protected: database passwords, API keys, etc. By accessing the source code, a would-be attacker can also specifically search for vulnerabilities in the application or system and thus compromise a website.
.git folders also a security risk in Switzerland
As part of the Coordinated Vulnerability Disclosure programme, the NCSC was made aware of the problem of insufficiently protected Git directories by a journalist from the dnip.ch platform in the summer of 2022.
As part of the vulnerability disclosure programme (Coordinated Vulnerability Disclosure), a journalist from the dnip.ch platform made the NCSC aware of the problem of insufficiently protected .git folders in summer 2022. As a result, the NCSC conducted a survey of the publicly available and accessible .git folders in Switzerland. It found 1,300 affected systems where potentially sensitive data such as source code, access data and passwords were accessible via insufficiently protected .git folders.
Security reviews necessary
In order to minimise the security risk and prevent the misuse of the exposed data files, the NCSC informed the affected companies and the relevant website operators directly by email in October 2022. The 400 recipients contacted were either the contact person for technical matters or the domain holder. However, the survey and information provided by the NCSC provide only a snapshot and does not claim to be exhaustive. The internet landscape is constantly changing, which means that system managers need to carry out regular reviews. Therefore, the NCSC recommends regularly reviewing the content and configuration of .git folders.
Recommendations on what to do
The .git folder on a productive system should never be publicly accessible on the internet. If it is not possible to remove the folder at short notice, access to the folder should at least be restricted and protected accordingly (e.g. using .htaccess rules or similar technical access restrictions, depending on the technology used).
Preventive measures such as reviewing and adapting the development process are even more effective. This should ensure that only the desired and intended data (build files) is stored at all. Sensitive or secret data such as passwords, API keys, etc. should never be stored in the source code or in the application itself (hardcoded) or at least it should be ensured that it is not stored in the .git folder and ignored (gitignore file). Unfortunately, experience shows that these basic security measures and best practices are often not observed.
Example of a .git folder
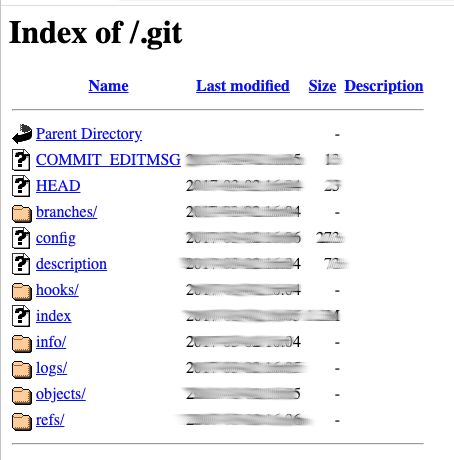
Git is only one of numerous examples. The same problem arises with unprotected .env and .DS_Store files: Some software products store their configuration in so-called environment variables, and on the Apple operating system, folder settings are stored in hidden DS_Store (Desktop Service Store) files. These files can also contain sensitive data.
Link
Last modification 27.10.2022





