15.03.2022 - The number of reports received by the NCSC was again high last week. Fake extortion emails purporting to be in the name of the police were reported last week, mainly by GP and paediatric practices. In addition, a request for quotation attempt was observed again; the aim was to obtain the access credentials for an email account.
Week 10: Fraudsters who make mistakes yet persevere, and threatening emails sent to doctors' surgeries

Request for quotation ends in phishing
The first NCSC weekly review was published exactly one year ago. Since then, the NCSC has provided weekly reviews of the most interesting and most frequent reports of the past week. Weekly review 44 probably described one of the most elaborate fraud attempts seen last year. The scam involved a request for quotation for a "subsea bolt tensioner" which ultimately lured the victim to a dubious website. A similar scam was reported again last week. This time, however, the attacker did not go to great lengths, but was all the more persistent.
In the current case, the request for quotation started with a simple email from a foreign general contractor who was interested in the products of the company contacted. A quick check showed that the foreign company existed and that the sender actually seemed to be an employee of this company.
However, the given link to a website where further information on the request was supposed to be found did not work, which meant that the email was ignored. Investigations by the NCSC revealed that the fraudulent website was not registered until three days after the email was sent. It seems that the fraudsters had forgotten to register the website or did not check the link before sending the email.
However, the fraudsters did not give up and tried their luck once more a few weeks later, without a link this time, but with a fresh enquiry as to whether there was any interest in working together. After the company's reply, the scammers again took almost two months to answer the email. This reply likewise contained a reference to documents that were to be downloaded, this time with a link that worked. At this point, the company that had been contacted became suspicious and contacted the NCSC.
A closer analysis showed that, in the email signature, both the email address and the Skype contact had been changed by the fraudsters and replaced with a Hotmail address.
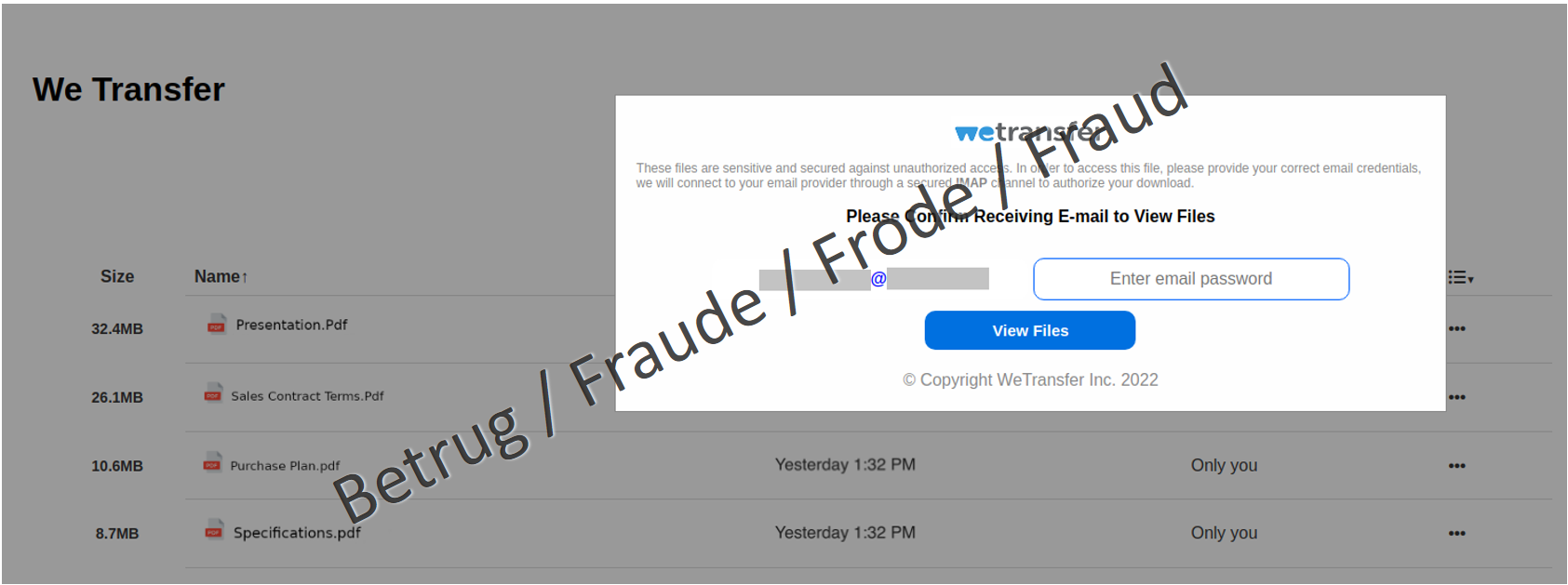
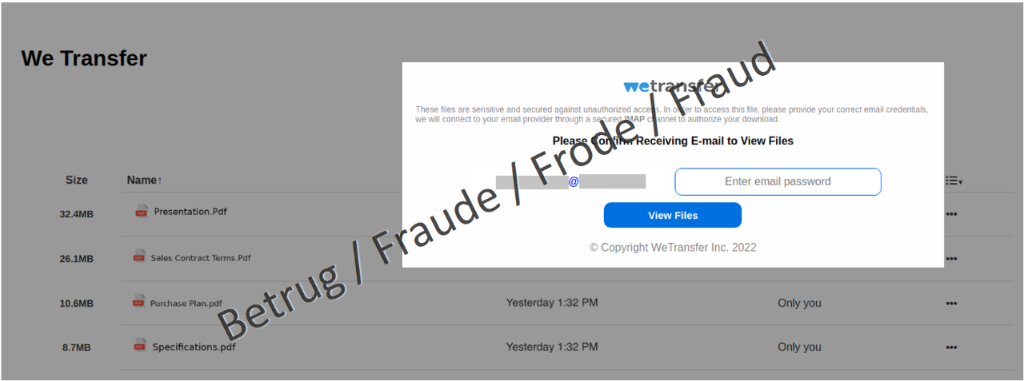
Clicking on the link caused various documents to be displayed in the background, while a pop-up window where the email password was to be entered appeared in the foreground. The aim was to make the user think that the documents were on the email server and that the email password had to be entered in order to download them. This password then gives the attackers full control of the respective email account and allows them to read client communications and manipulate invoices sent to clients to their advantage.
What is astonishing in this case is the fraudsters' persistence; this fraud attempt went on for several months. It is possible that the attackers were using this lengthy and continuous communication to try to gain the trust of the company.
- Install two-factor authentication whenever possible. This offers an additional layer of protection to prevent your account from being hacked, especially if the attackers have access to your email account.
- Before buying anything online, check that the company in question is reputable; pay particular attention to the email addresses provided.
- Exercise particular caution with company email addresses from free providers such as Google, GMX or Hotmail.
- Aside from information on the internet, checking the commercial register number or the address can also give clues about a company's reputability.
Current statistics
Last week's reports by category:
Last modification 15.03.2022