22.03.2022 - The number of reports received by the NCSC remained high last week. A sophisticated attempt at CEO fraud failed because of the targeted firm's use of familiar forms of address, and also highlighted the misuse of parked domains. In addition, malware was distributed under the pretext of a visa renewal.

Sophisticated CEO fraud attempt rapidly unmasked
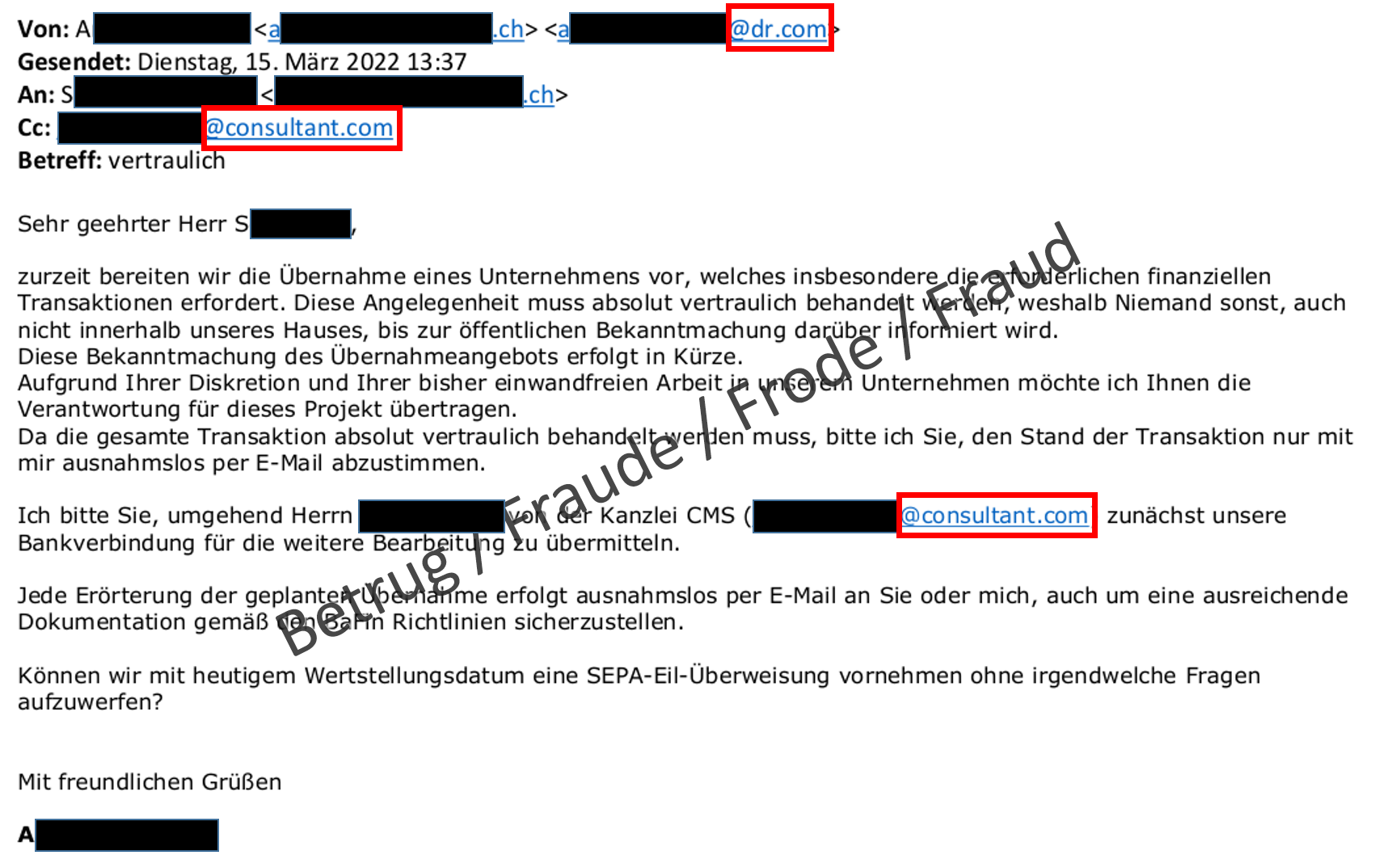
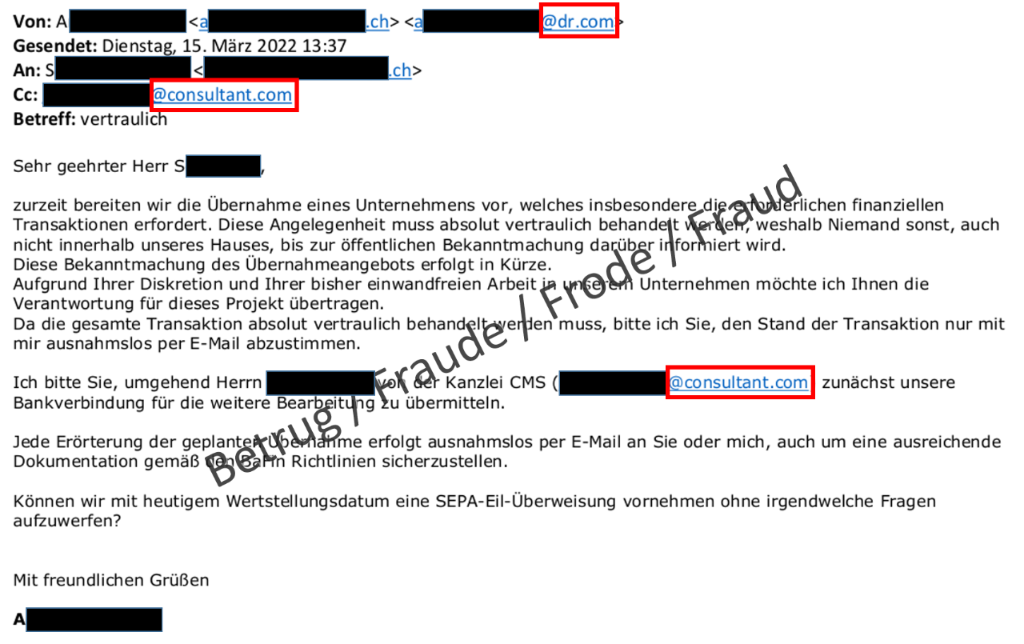
This type of fraud, in which a company CEO or club chairperson supposedly sends the head of finance or the treasurer a payment request, is called CEO fraud. The fraudsters forge the sender address in the email in an attempt to win the victims' trust and persuade them to exchange emails with the purported CEO. For this purpose, they try to make the forged addresses appear as plausible as possible. They obtain these addresses from a domain grabber, i.e. a company that registers a large number of domains and then sells them on at a huge markup. The domain grabber allows the parked domains to be used for sending and receiving emails. This is part of the domain grabber's business model, and the fraudsters exploit this.
In a case of attempted CEO fraud in the healthcare sector reported to the NCSC, the domains dr.com and consultant.com were fraudulently used.
Although the fraudsters went to a lot of trouble to make the fraudulent email appear genuine, the very sharp-eyed recipient spotted the fraud immediately. Unaware that the company in question had a culture of familiarity and first names, the fraudsters used a formal style.
- Raise all employees' awareness of CEO fraud! Especially employees in finance divisions and in key positions must be informed about these possible methods of attack. In the case of associations, all presiding members and treasurers must receive training.
- All processes which concern payment transactions should be clearly defined internally and complied with by employees in all cases (e.g. dual control principle, joint signature by two people).
- In general, do not divulge any internal information and be careful with payment requests. Do not respond to unusual payment requests.
Malware instead of a visa for Thailand
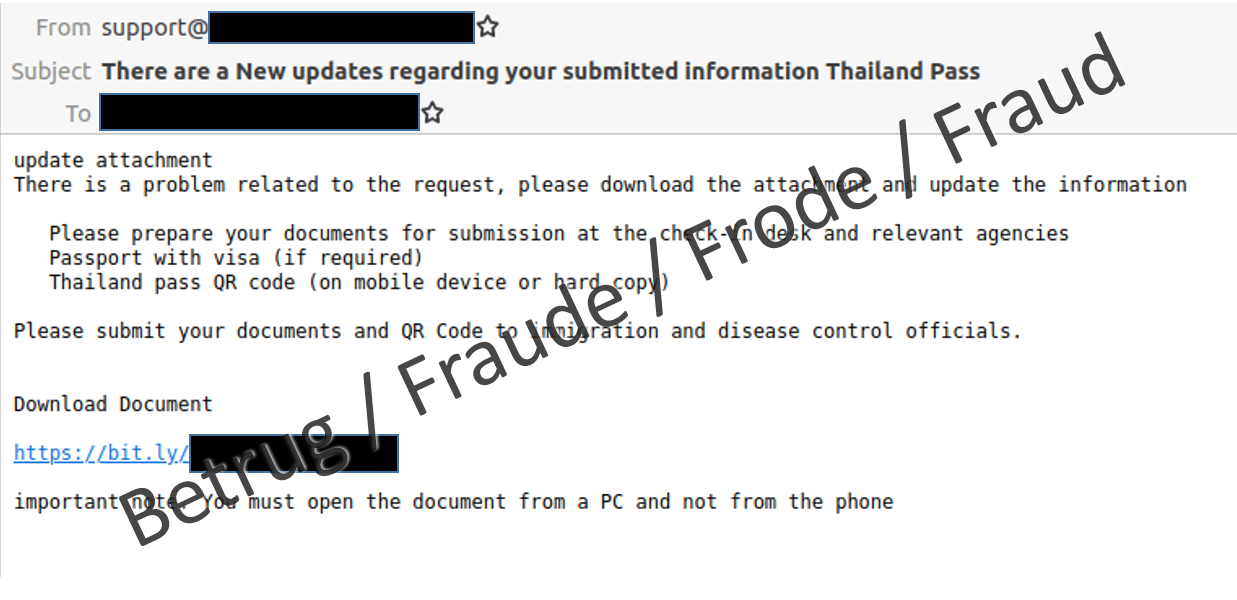
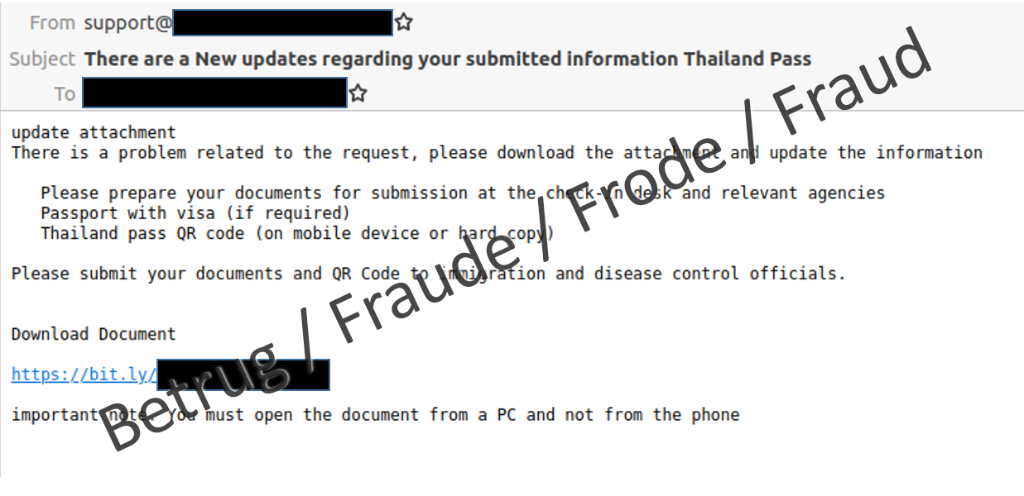
A new method of distributing malware was reported to the NCSC. Someone who regularly travels to Thailand received an email requesting them to update the details of their Thailand visa. Since the recipient was indeed planning to travel to Thailand soon, they complied with the request. They then received an email with a link to what appeared to be a visa application form.
The link resulted in an HTML file being downloaded, part of which was directly executed in the relevant browser.
The HTML document itself showed an apparent passport registration page and contained an ISO image which was immediately displayed as an apparent download. ISO files are treated by computers like executable CDs and DVDs, and often contain installation media for games or office programmes, for example. For this reason, ISO images are often executed immediately.
The reported ISO image contained a malicious downloader that attempted to install a Trojan in the system.
- Be wary all unsolicited email notifications you receive.
- Be especially suspicious if you are asked to open or download a file.
- Never allow your computer to execute files obtained in this way.
- Report such cyberincidents to the NCSC and, if possible, send us the email in question.
NCSC-Reporting form
Current statistics
Last week's reports by category:
Last modification 22.03.2022