29.03.2022 - The number of reports received by the NCSC was slightly higher last week. It received reports of text messages again trying to trick victims into installing FluBot malware on their smartphones. In addition, website owners received emails from purported Ukrainian hackers claiming to have hacked their website and demanding a "donation".
Week 12: FluBot malware is active again in Switzerland and various web administrators receive a threatening email from purported Ukrainian hackers

FluBot malware is back
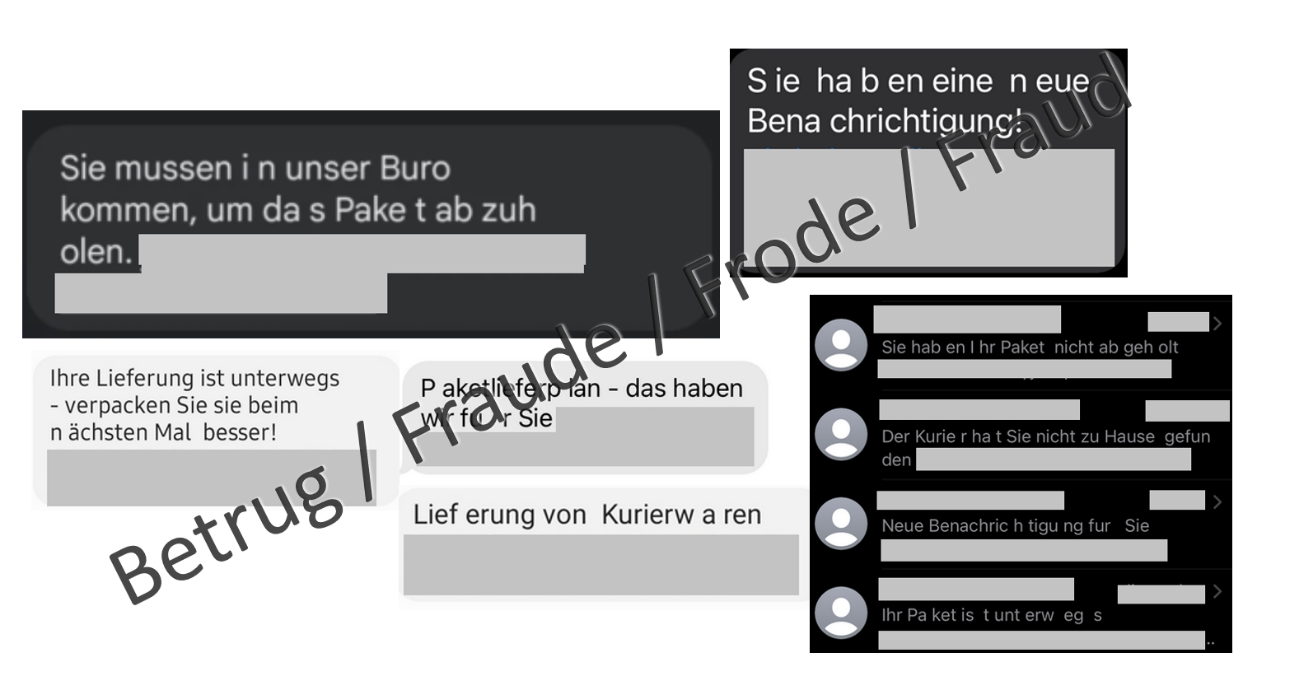
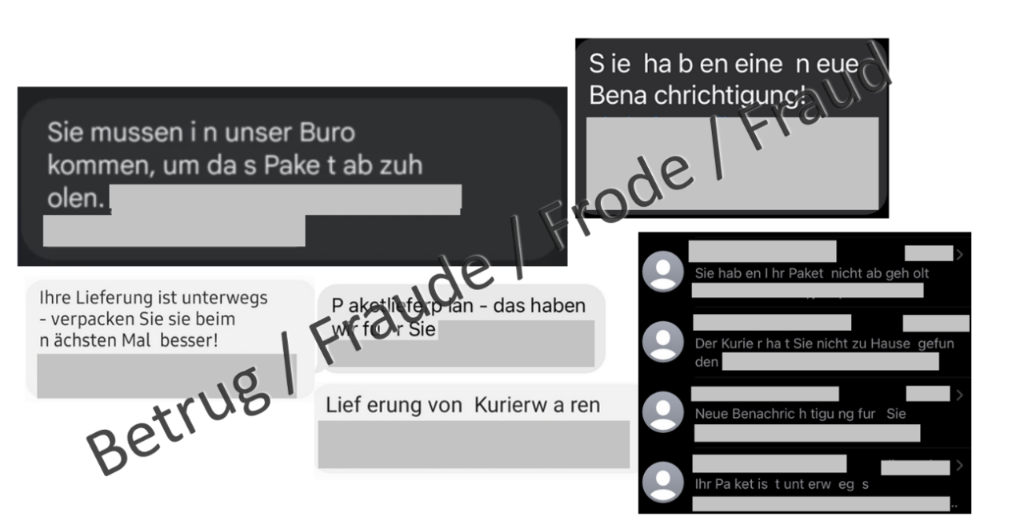
Last week, the NCSC received reports of numerous text messages containing notifications of supposed parcel deliveries. Although various wordings were used in the messages, there were similarities in the formatting: the words contained numerous spaces. The link under the text led to a website which prompted the victim to download and install the software of the parcel service provider on the Android smartphone.
In fact, the software in question is FluBot malware, which is not new to Switzerland. The last big wave hit the country in autumn 2021, when text messages containing a purported voice message were sent in large numbers. The NCSC reported on this. Internationally, text messages asking "Is that you in the video?" have also been observed, but bogus requests to update a browser or operating system are also part of the FluBot repertoire. Typically, attackers change their target areas after a very short time, usually after just a few days. Campaigns have primarily been observed in Australia and Germany since December 2021. In Switzerland, text messages with parcel notifications have been sent since 18 March 2022.
FluBot specialises, among other things, in stealing text messages from mobile phones. The aim here is to find one-time passwords among the stolen text messages. Once infected, a smartphone's entire address book is sent to the attackers' control server. The smartphone then receives a list of phone numbers from other hacked smartphones to which it should send the malicious text message.
Even though this malware only attacks Android devices, users of devices with the iOS operating system must also be careful and should not click on any links in text messages.
- Do not install any software that is offered outside the operating systems' official stores.
- In particular, you should not install any software received via a link in a text message or other messenger service (WhatsApp, Telegram, etc.).
- If you nevertheless installed such software, you should have the device checked by a specialist and should not carry out any banking transactions or online shopping. Do not enter any passwords either.
- Restoring the factory settings on the infected device is almost the only way to remove the malware.
Purported hackers from Ukraine demand a "donation"
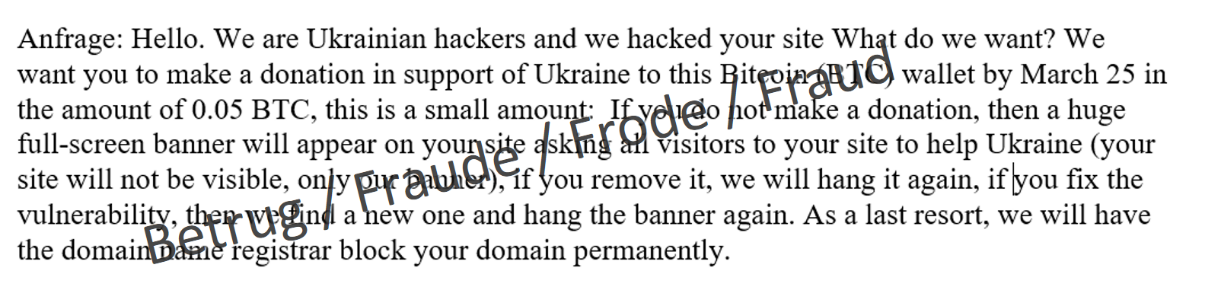
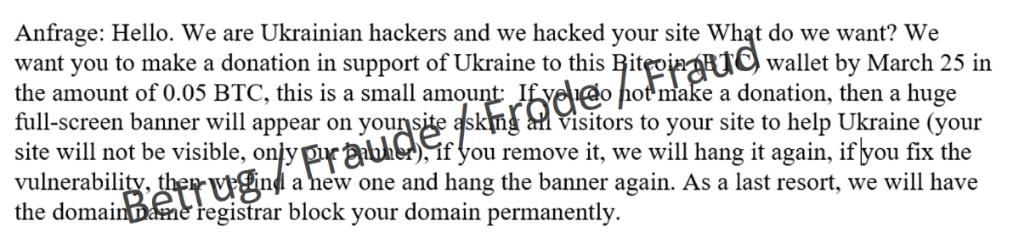
The NCSC also received several reports of threatening messages to website owners from supposed Ukrainian hackers last week. The messages were sent via the websites' contact form. The hackers claimed to have found a vulnerability in the website and asked the website owner to transfer a "donation" of BTC 0.05 (currently approx. CHF 2,000) to a specified bitcoin account.
If the website owner did not comply with the demand, the site would be hijacked and a banner would be displayed asking all visitors to help Ukraine. If the banner or vulnerability was removed by the owner, the banner would be reinstalled and a new vulnerability identified. If this did not work, the attackers threatened to permanently delete the domain from the registry.
Needless to say, the message was only a bluff. However, the case shows that fraudsters are also exploiting the tragedy of the war in Ukraine in various ways for their own purposes. The NCSC drew attention to this issue back on 8 March 2022. Last week, the Zurich cantonal police also warned against fraud attempts.
- Do not allow yourself to be intimidated. If in doubt, report suspicious messages to the NCSC or the police.
- Of course, you should keep web servers and all web applications up to date.
- As a general rule for donations:
- Do not respond to contact attempts via email
- Avoid making donations by credit card
- Do not transfer any cryptocurrency funds
- Do not send gift voucher codes (Google Play, Apple iTunes etc.)
- It is best to only use IBANs from aid organisations that are ZEWO certified:
https://zewo.ch/en/
Current statistics
Last week's reports by category:
Last modification 29.03.2022