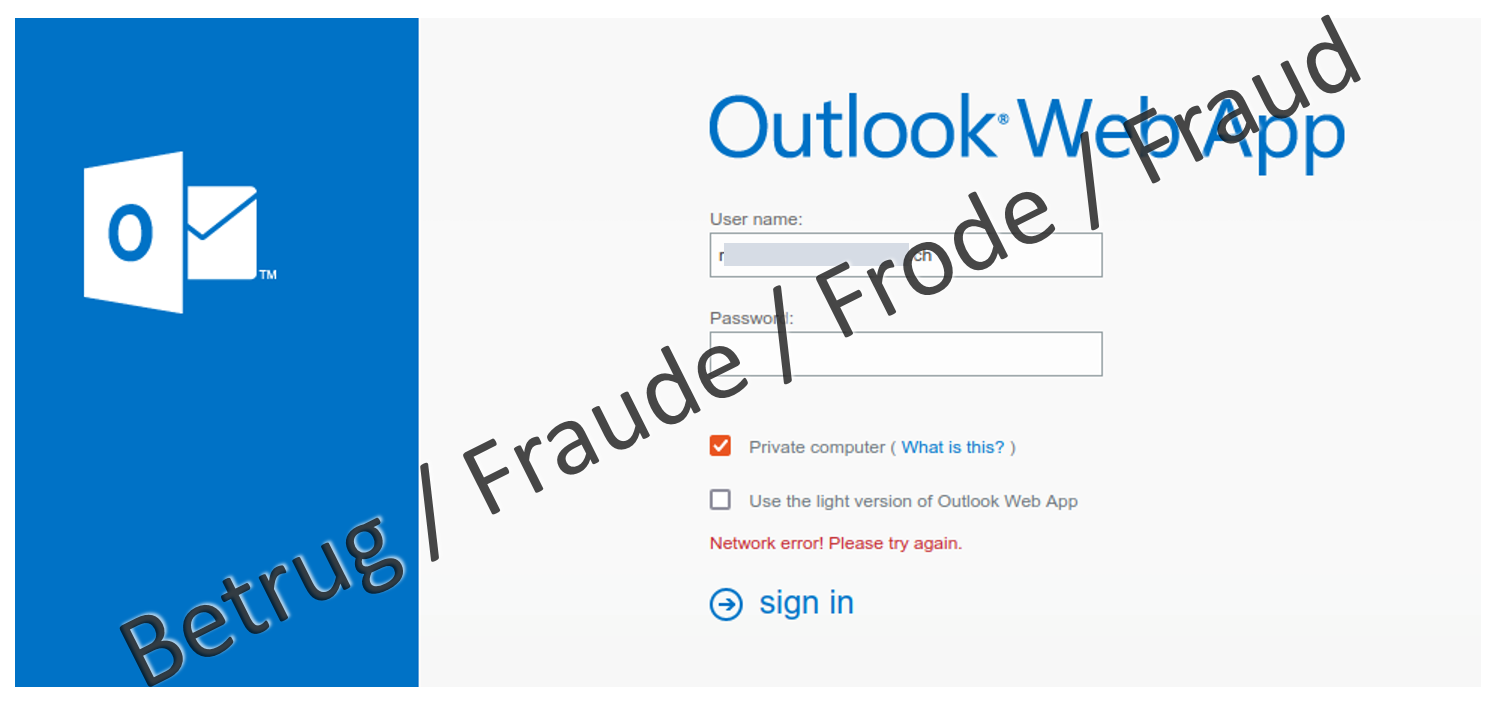
05.04.2022 - The number of reports received by the NCSC was stable last week. What stood out were reports of very targeted phishing attempts on Office 365 login credentials. Only with the use of multi-factor authentication could these attacks be blocked.

Phishing is one of the cyberthreats most frequently reported to the NCSC. Phishing refers to attempts to use an email or text message to trick people into entering their credit card details, bank details or login credentials on a fake website. The attackers then use this data to try to withdraw money or log in with the stolen login credentials and misuse an email account to continue sending phishing emails, for example.
Since Office 365 was launched, the NCSC has been receiving a growing number of reports concerning attempts to gain access to these login credentials. Access to Office 365 accounts is highly valuable for attackers, as messages can then be sent in the name of the hacked account holder. The attackers hope that the recipients will not suspect abuse and will thus notice the fraud less quickly. Emails with malware are often sent via hacked accounts.
Two attacks on Office 365 accounts reported to the NCSC were so well tailored to the attacked employees of the respective companies that the employees fell for them and entered their login credentials on the fake websites. The only reason this did not have any consequences was that, in addition to the user name and password, a second, independent factor was also required in each case – typically a one-time code sent to the user's mobile phone or generated with it.
Shortly after the login credentials were stolen, the attackers tried to register their own phone for multi-factor authentication (MFA), but this was prevented and thus also helped the data leak to be detected.
The use of multi-factor authentication offers very good protection against many such attacks. Fortunately, multi-factor authentication is now proposed by a great many internet services, especially online payment facilities, financial institutions and larger webshops.
Attackers respond to this extra security by attacking users' mobile phones as well. Last week's review warned of such a method with the FluBot malware.
- Use multi-factor authentication whenever possible. This is sometimes called two-factor authentication or multi-/two-step verification.
- Do not click on any links in emails if you cannot identify their origin beyond doubt.
- Do not enter Office 365 login credentials based on a link in an email. Instead, go to your Office 365 homepage in the browser and log in there. This applies likewise to all other login processes.
- Use the reporting form to report any such attempted attacks to the NCSC.
Current statistics
Last week's reports by category:
Last modification 04.04.2022