20.04.2022 - The number of reports received by the NCSC last week remained at a similar level to the previous week. Threatening emails supposedly sent by law enforcement agencies remained dominant. Reports of fake sextortion emails accompanied by a hacked webmail or social media account are also on the rise at the moment. This is a new variant.
Week 15: New variant of fake sextortion emails, with email accounts and social media accounts hacked at the same time

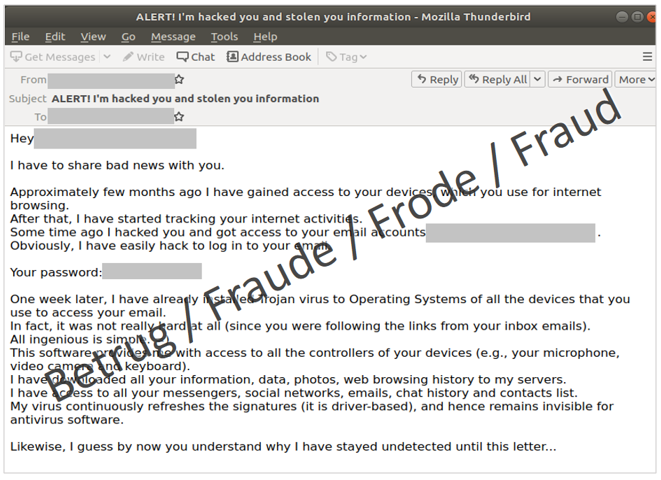
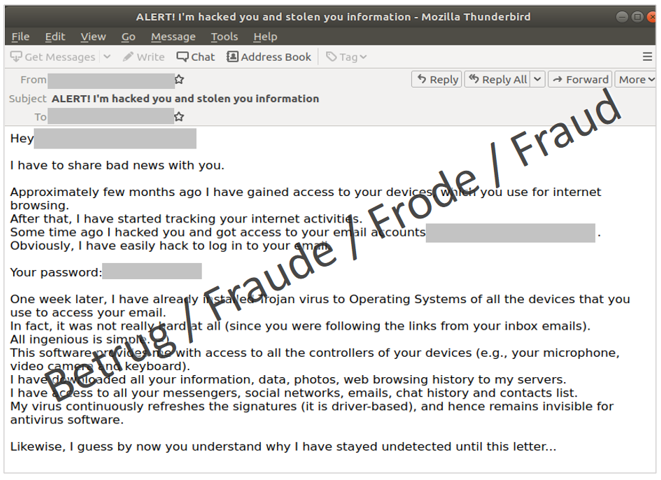
After a five-week period in which very few fake sextortion reports were received, the number started to rise again last week. In fake sextortion, the scammers claim in an email that they have collected photo or video material which shows the email recipient allegedly visiting pornographic websites. The extortionists threaten to publish the photo or video material if the ransom demanded is not paid within a certain period of time. To lend weight to the threat, some of the threatening emails also mention passwords used by the recipient. So far, these passwords have come from data leaks that are several years old and, provided people have regularly changed their passwords, they are no longer valid.
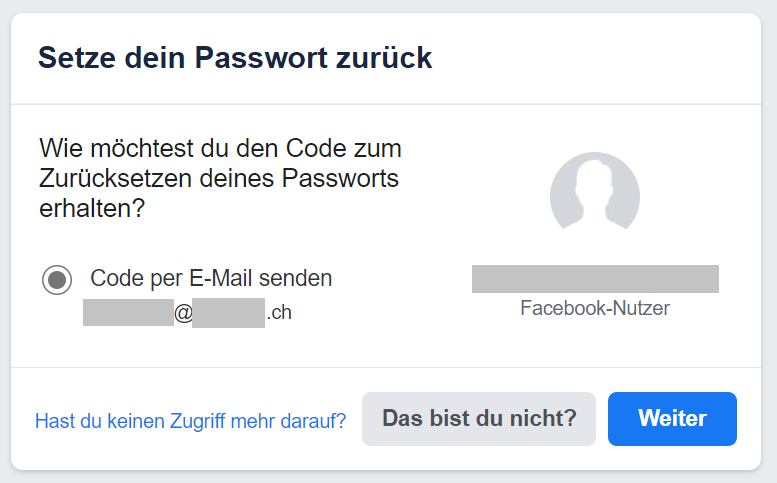
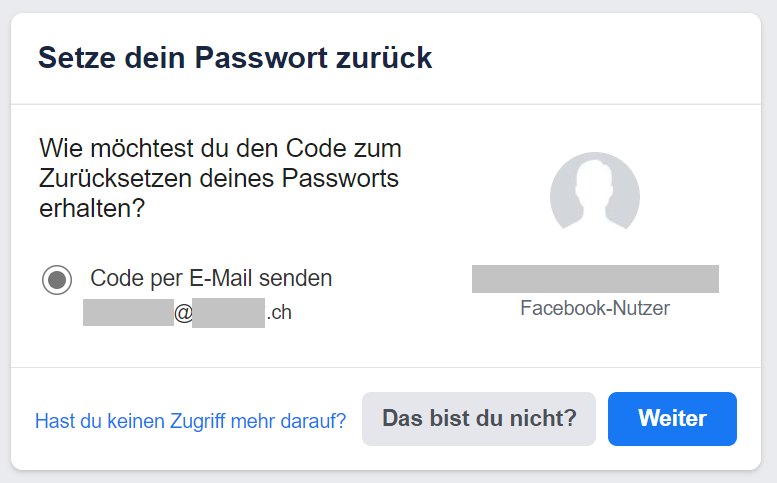
In the current wave, the attackers are going a step further. There are more and more reports that the passwords given in the email are current and correct and that the attackers are also trying to hack the email account at the same time with these access credentials. In some cases, the attackers have even gained access to the victims' social media accounts, such as Facebook or Instagram. One possible approach the attackers could take is to abuse the password reset function. With many online services, a reset request can be triggered in the case of a forgotten password, and a link is sent to the registered email address. A new password can then be set using this link. If attackers have access to the email account, they therefore potentially have access to other online services as well. Because of this function, the email address has become the linchpin of various online services. Consequently, the access credentials for this central email account should be treated with appropriate care.
Another frequently used variant is the creation of a forward rule on a hacked email account. This means that all emails received by the victim are automatically forwarded to an email address defined by the attacker – even if the email password has been changed. In this way, the attackers retain full access to all password reset requests.
It has not yet been possible to clarify where the attackers got the passwords used in the current cases. Since email addresses from various providers are affected, the NCSC does not believe at the moment that there was a data leak. It is more likely that the data originated from recent phishing attacks. Alternatively, it is also conceivable that the data was stolen by means of malware on a mobile phone, for example.
- If a password mentioned in a fake sextortion email is one you use, you should change it as a matter of urgency. In addition, you should check the email account for any forwarding rules.
- Also change the passwords of any other services linked to the email account.
- If an internet service provider offers two-factor authentication, be sure to use it. By doing so, you considerably increase the level of protection.
- Even though the attackers in these cases had access to the email account, the NCSC is not aware of any cases so far where compromising images were present or the computer was hacked.
- The bitcoin addresses contained in the emails may provide information about the unknown perpetrators. By forwarding such blackmail emails to reports[at]stop-sextortion.ch, you will help to support the investigations.
Current statistics
Last week's reports by category:
Last modification 20.04.2022