10.05.2022 - The NCSC again received about the same number of reports last week as the week before. There was an increase in reports of emails claiming that computers were infected. Interestingly, after a few clicks, the users actually arrive on the websites of well-known antivirus manufacturers. Resourceful operators are behind all this, exploiting the commission offers of well-known providers of antivirus software.

The variations in fake support calls are manifold and have been known about for years. For example, in one type, a website displays a warning that the computer has a security problem and that the user should call the telephone number given. During the phone call, the victim is then tricked into downloading a program that allows the purported support staff to access the computer and manipulate it. In most cases, the attackers also try to sell the victim a service ("system cleaning"), for which credit card details are requested.
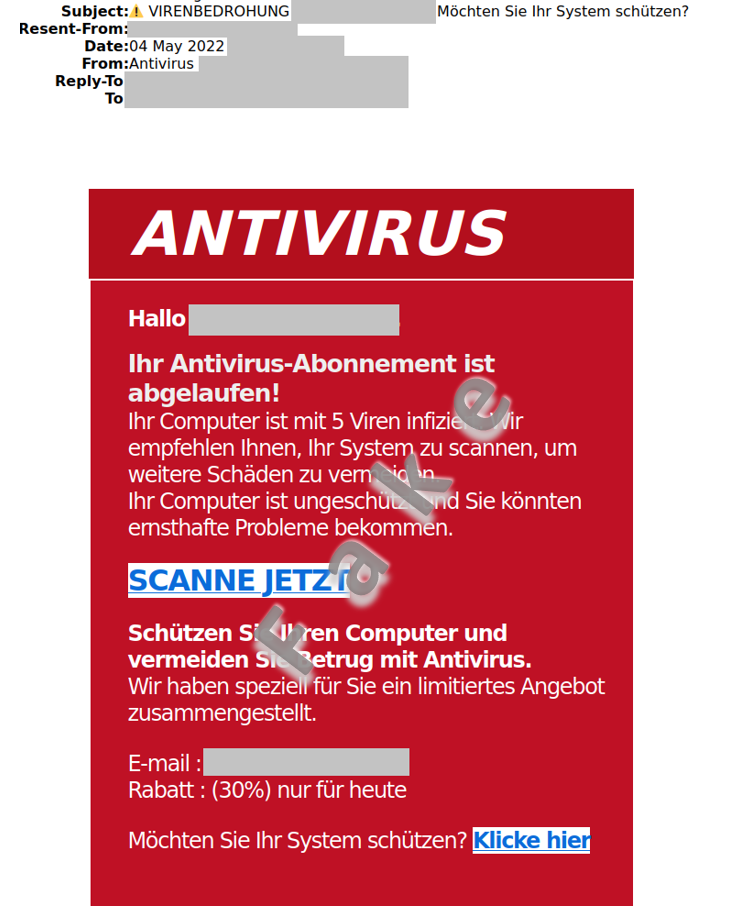
Last week, there was an increase in reports about a similar approach. Emails with the subject "Virus threat! Do you want to protect your system?" were sent to various recipients. The emails claimed that the antivirus program subscription had expired and that the computer had been infected with five viruses. Instead of calling a telephone number as usual, the recipient was enticed to click on a link promising a 30% discount on an antivirus program subscription.
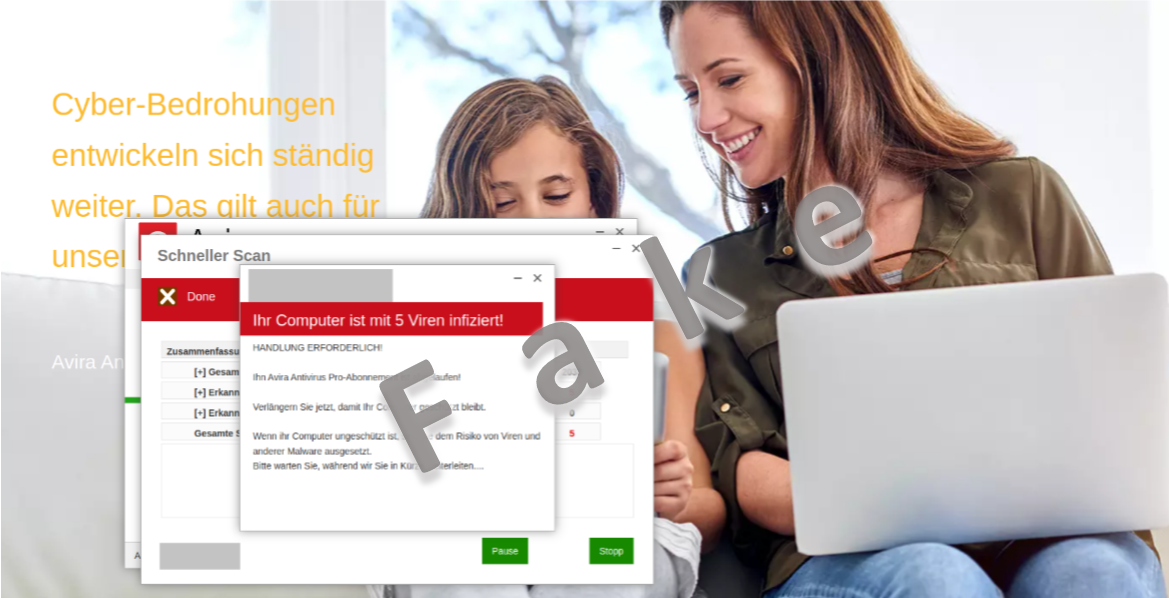
However, clicking on the link did not open the website with the promised discount offer, but rather a page with numerous pop-ups, which simulated a virus scan of various computer directories. Not surprisingly, the five viruses mentioned were detected. Incidentally, the scan always checks Windows directories, regardless of whether the page is opened on a Windows or Mac system, or on a mobile phone.
After a few seconds, users were redirected to the websites of well-known antivirus manufacturers. The promised offers of a 30% discount were indeed listed and available for purchase.
The emails and the virus scan are fake and only serve to scare the recipients into purchasing the product in question. But who is behind them and what is their intention? This is certainly not a promotional campaign by a manufacturer of antivirus programs. The NCSC's research shows that, in these cases, partner and commission programmes of the respective antivirus manufacturers are misused in order to earn money illegally. In these programmes, money is paid to individuals who convince others to buy a certain product. Such commission schemes are particularly common in connection with insurance and estate agents. However, the practice is now established also in the virtual world and many internet service providers offer such programmes. In addition to the advantages such bonus programmes offer, this example shows they can also be misused.

Recommendations:
- Antivirus software is a basic form of protection. However, when purchasing such a program, use the official websites and not dubious enticement offers.
- Do not click on any links in emails if you cannot identify their origin beyond doubt.
- Neither antivirus manufacturers nor other software companies make unannounced or unsolicited support calls, or send unsolicited emails, to resolve computer problems.
- Do not give anyone remote access to your computer. If you have granted remote access, there is a possibility that your computer has been infected. The first step is to uninstall the remote access program.
Current statistics
Last week's reports by category:
Last modification 10.05.2022