14.06.2022 - The number of reports received by the NCSC was high again last week. A supposed SBB competition spread very quickly thanks to the snowball system. And one report provided a perfect example of how important it is to apply patches swiftly.

Supposed SBB competition spread with the snowball system
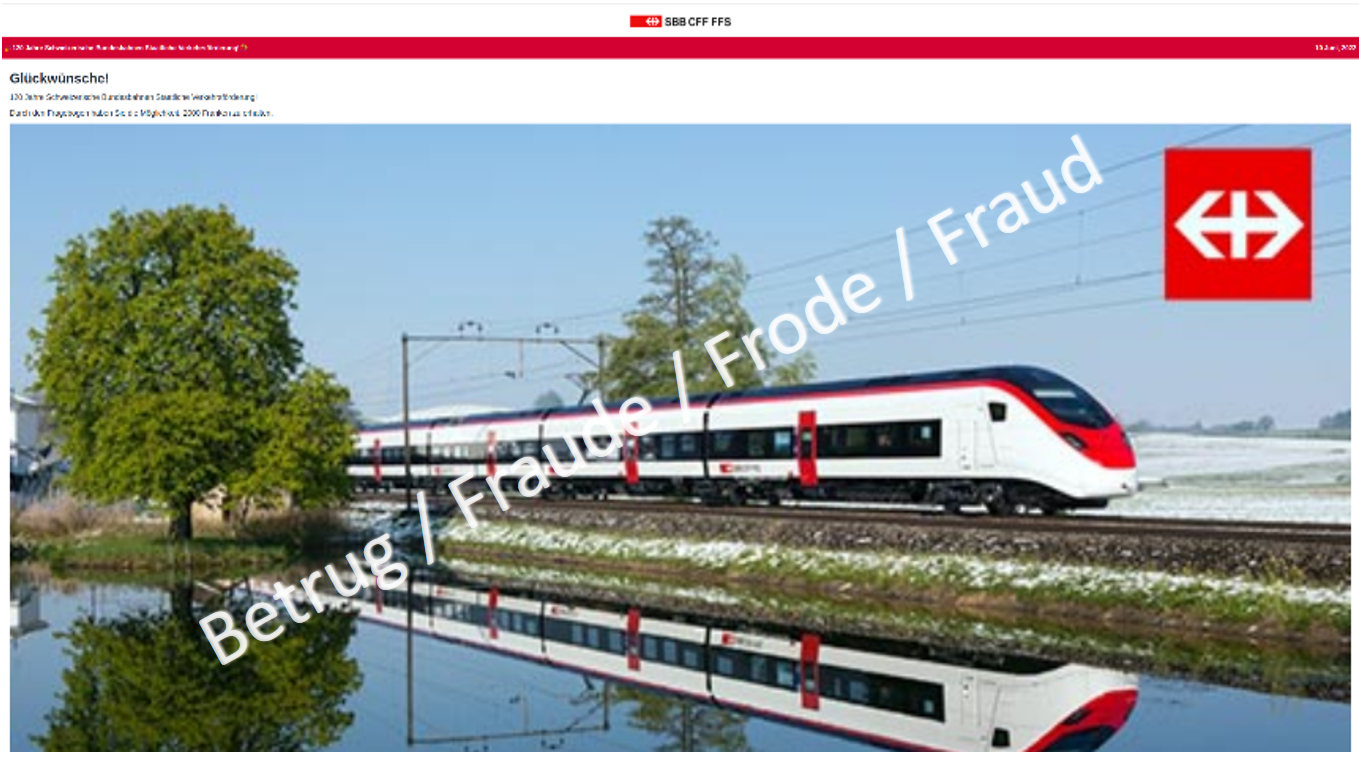
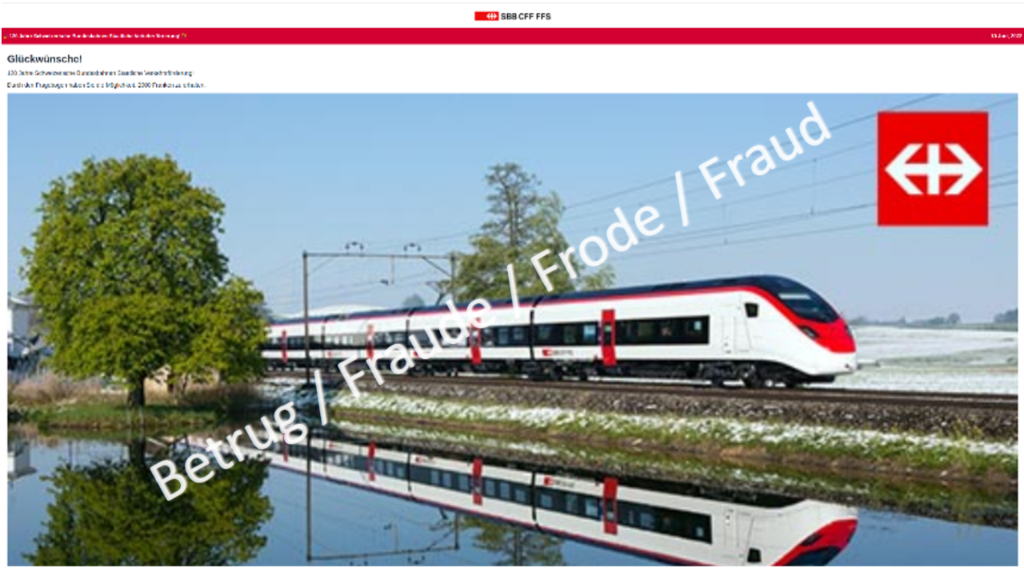
Last week, the NCSC received a large number of reports concerning WhatsApp messages about an apparent SBB competition, claiming that people could win CHF 2,000 because of the "120th anniversary of the state transport subsidy".
After answering four very simple questions, participants have three chances to guess in which of the packages the CHF 2,000 is hidden. Unsurprisingly, they always win. However, to receive the prize, people must first forward the link via WhatsApp to 20 contacts or 5 groups. In this way, the attackers ensure that the scam is spread without them having to do anything. Numerous examples of this approach have been observed in the past using different company names, including Migros, Coop, Mediamarkt and Rolex, etc. By the way, the same competition, but involving Deutsche Bahn, was also observed last week. It too was supposedly in celebration of a 120th anniversary.
What exactly may be lurking behind the last step varies. It depends on the different configurations and the user's device. In one variant, participants are supposed to answer several questions by sending a premium rate text message to foreign numbers. In another, participants are told to register, and unknowingly take out a subscription that costs CHF 14.50 per week. In yet other variants, people are taken to dubious investment sites or other competition sites open up and the procedure starts all over again.
- Be sceptical about messages claiming that you have won something.
- Be particularly careful if you have to give your credit card details or phone numbers in order to access free offers.
- Do not forward such messages.
- If you provided your phone number, please contact your mobile provider.
- If someone unwittingly takes out a subscription, the State Secretariat for Economic Affairs (SECO) recommends sending a registered letter to the provider immediately after discovering the error and contesting the contract on the grounds of error and willful deception:
https://www.seco.admin.ch/seco/en/home/seco/nsb-news.msg-id-34118.html.
Quickly installing patches is crucial
Devices and servers that are directly accessible from the internet are particularly vulnerable. The internet is constantly scanned for existing security vulnerabilities. If a server is not up to date, it does not take long for attempted attacks to be carried out. Network-attached storage (NAS) devices have been targeted time and again in the past. The Qlocker and Deadbolt malware are just two examples, but Microsoft Exchange Server vulnerabilities are also repeatedly sought and found. The NCSC has regularly issued warnings to affected companies (see NCSC-News, 16 February 2022).
A case involving the vulnerability in the Confluence collaboration software, which became public at the beginning of June, illustrates the importance of immediately patching critical vulnerabilities. On 2 June 2022, the manufacturer Atlassian warned of a serious security vulnerability in Confluence (CVE-2022-26134) that was already being actively exploited. One day later, the manufacturer published a patch for the affected versions and a workaround. However, the first case in Switzerland quickly occurred. On 7 June 2022, the NCSC received the first report of a ransomware incident in which this vulnerability was exploited. Fortunately, the damage was minor in this case, as the backup was not affected by the encryption and worked. However, the example shows that swift action is called for, especially in the case of critical security vulnerabilities.
- Make sure that all critical patches are always applied consistently and promptly in the software you use.
- Keep an overview of the software used in your company.
- Ensure that the manufacturer informs you regularly and in a timely manner about serious security vulnerabilities in the software you use.
- Ensure that you always have an up-to-date offline backup.
- Install risk-reducing measures by restricting access to systems visible from the internet (e.g. geoblocking).
Current statistics
Last week's reports by category:
Last modification 14.06.2022