06.09.2022 - The number of reports received by the NCSC fell slightly again last week. Reports regarding threatening emails allegedly from the police remained the predominant type. Two cases reported to the NCSC last week show how attackers exploit the fact that practically every office today has a multifunction printer with a scan-to-email function.

Beware of phishing when using multifunction devices
Almost every office now has a multifunction device that can copy, print and scan. As digitalisation increases, the scan-to-email function is becoming more and more popular. This involves scanning documents or letters with such devices and then sending them as a PDF file to an employee's email address.
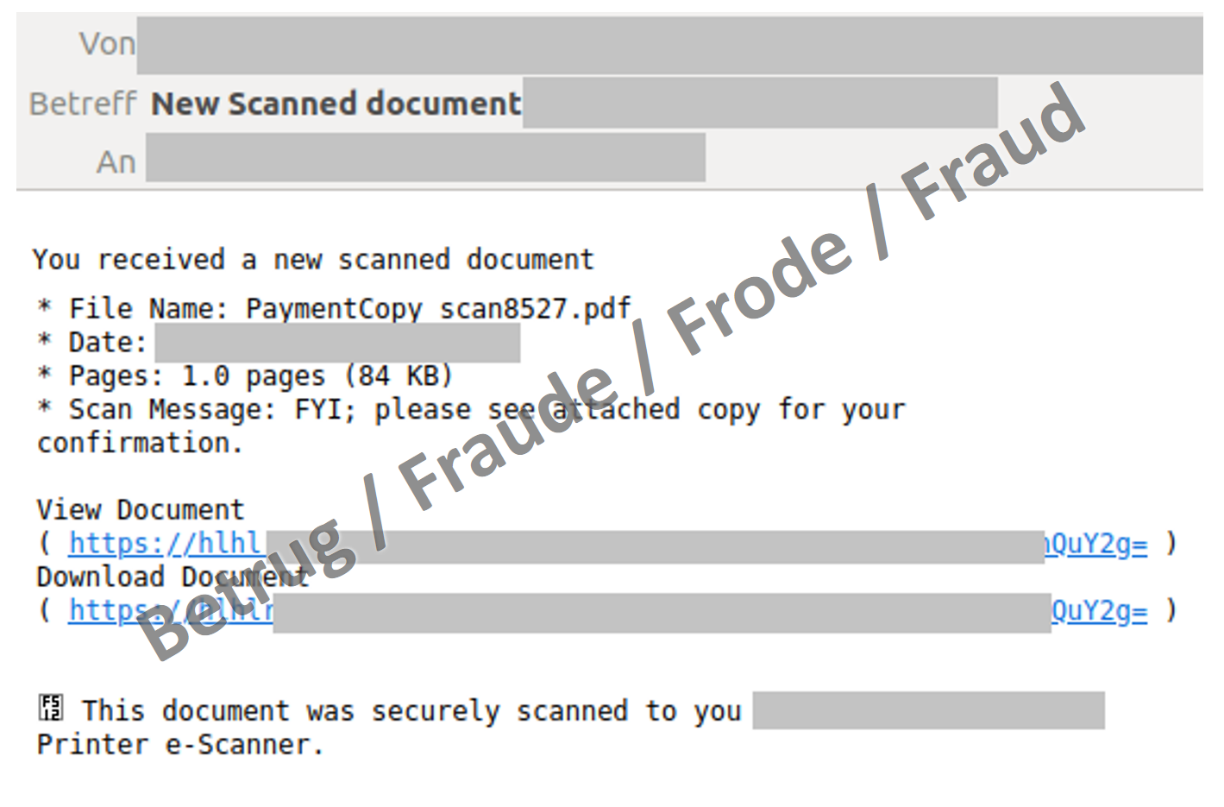
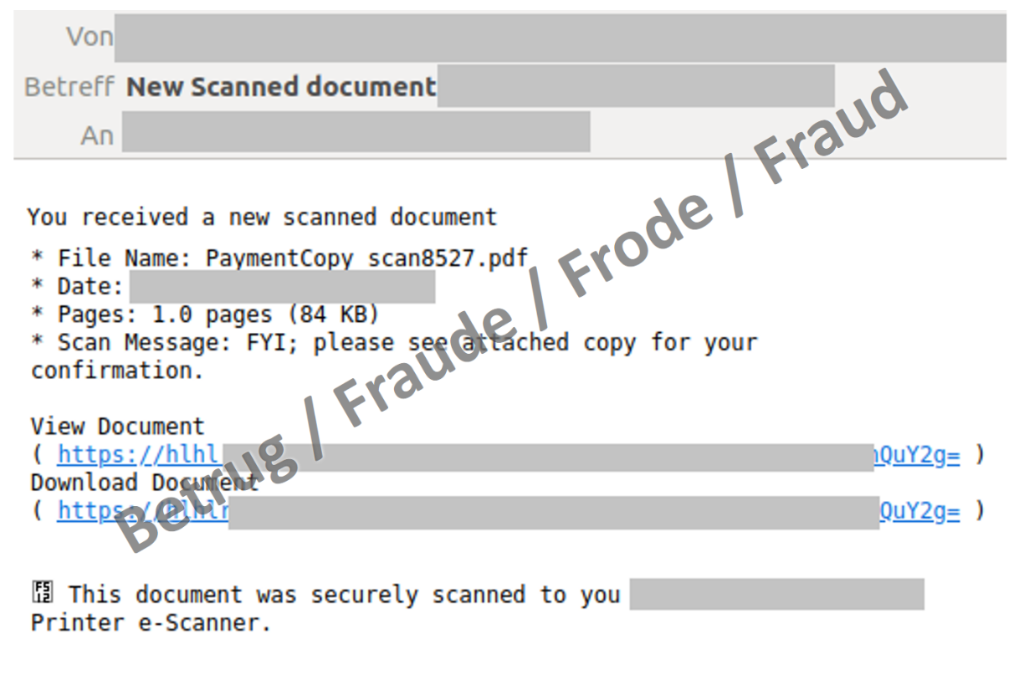
However, this function also carries certain risks and is exploited by attackers to steal email passwords or install malware on computers, as illustrated by cases reported to the NCSC last week. For example, the attackers sent an email which made the employee believe that a document had been scanned with the multifunction device and could be downloaded from the internet address provided. The email was tailored to the company and was intended to trick the victim into clicking on the link and entering the email password on the phishing website that opened. This exploits the fact that employees tend to trust such emails because they are familiar with them and they appear to come from an internal company address.
However, after entering the password, there was no document, just an error message stating that the service was currently unavailable. The victim thus has the impression that it is a technical problem and initially does not suspect anything. In the meantime, the attackers log into the email account and create a forwarding rule, for example, causing all incoming emails to be forwarded to the fraudsters from then on.
Even if the victim detects the attack later on and changes the password, the attackers continue to receive the incoming emails. The attackers are mainly on the lookout for incoming invoices. They copy such invoices, specify a new IBAN and resend them in the hope that the victim will then transfer the amount to the fraudsters. However, other information is also collected, and this can then be used for targeted attacks against the company.
In the case described above, the attackers took the trouble to tailor the email to the company. But even without a great deal of research, the attackers are likely to hit on the right manufacturer, as a limited number of manufacturers share the market for multifunction devices. If a company publishes information such as employee names or email addresses on its website, a highly targeted attack can be launched against a company without a great deal of effort.
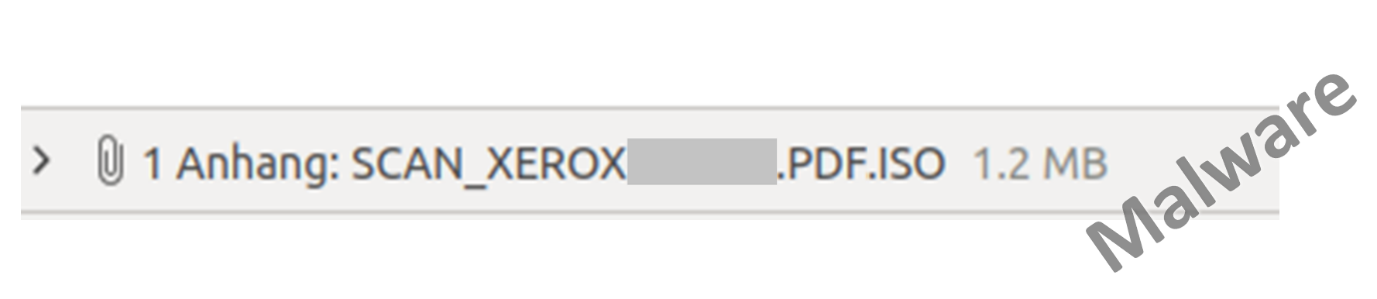
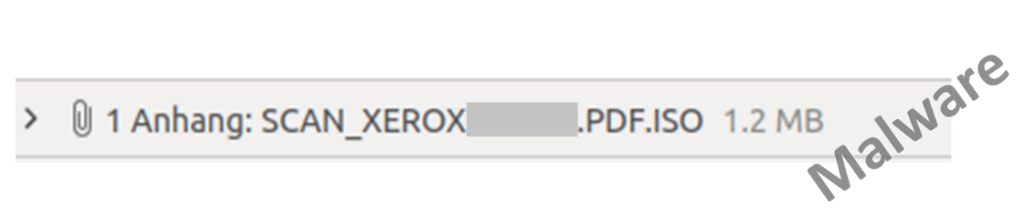
Attackers also try to install malware on company computers in this way by tricking recipients into clicking on a malicious email attachment. In one case, for instance, a malicious ISO file was disguised as a scanned XEROX document.
Recommendations:
- Ignore emails regarding scanned documents unless you launched the scan yourself.
- Sender email addresses can easily be spoofed. Even if the email appears to be from your own company, be careful.
- If you are unsure, consult your colleagues.
- Be especially suspicious if you are asked to open or download a file.
- Never allow your computer to execute files obtained in this way.
- If employees provided the email password in a phishing attack, it is necessary not only to change the password immediately, but also to check email filters and forwarding rules. Attackers will often set up email forwarding rules which send them a copy of all the emails you receive.
Current statistics
Last week's reports by category:
Last modification 06.09.2022