20.09.2022 - The number of reports received by the NCSC declined last week. Fake threat emails claiming to be from the police still make up the majority of reports. Last week, the name of the NCSC itself was misappropriated as the sender of these emails. There was also a resurgence in phone calls purporting to be from parcel delivery services, which attempted to fool the victims into downloading software in the guise of a parcel delivery notification.

Dial M for malware
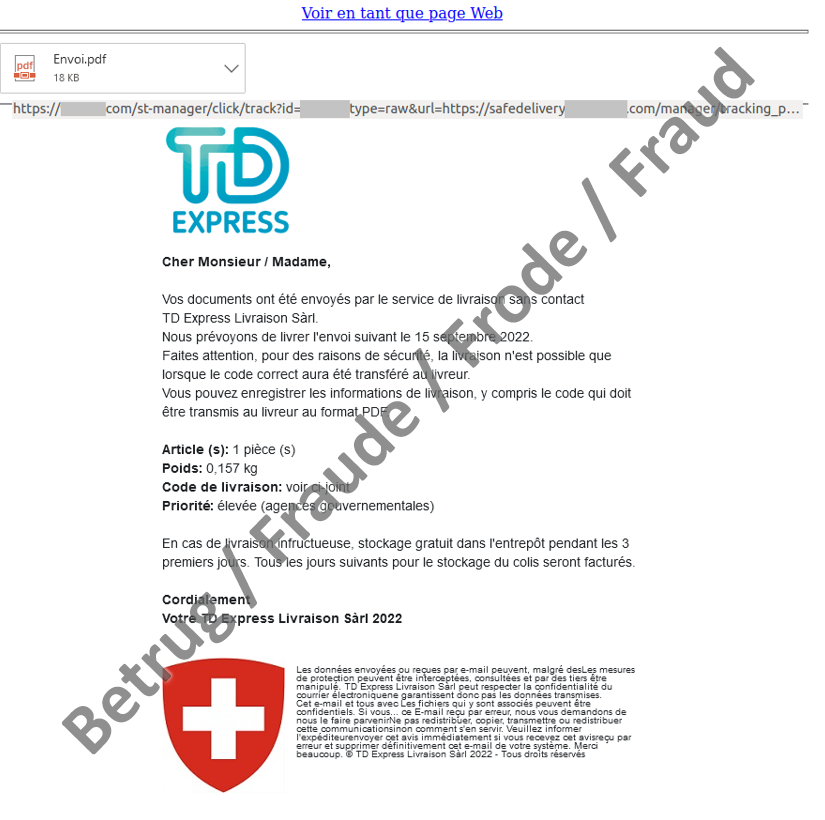
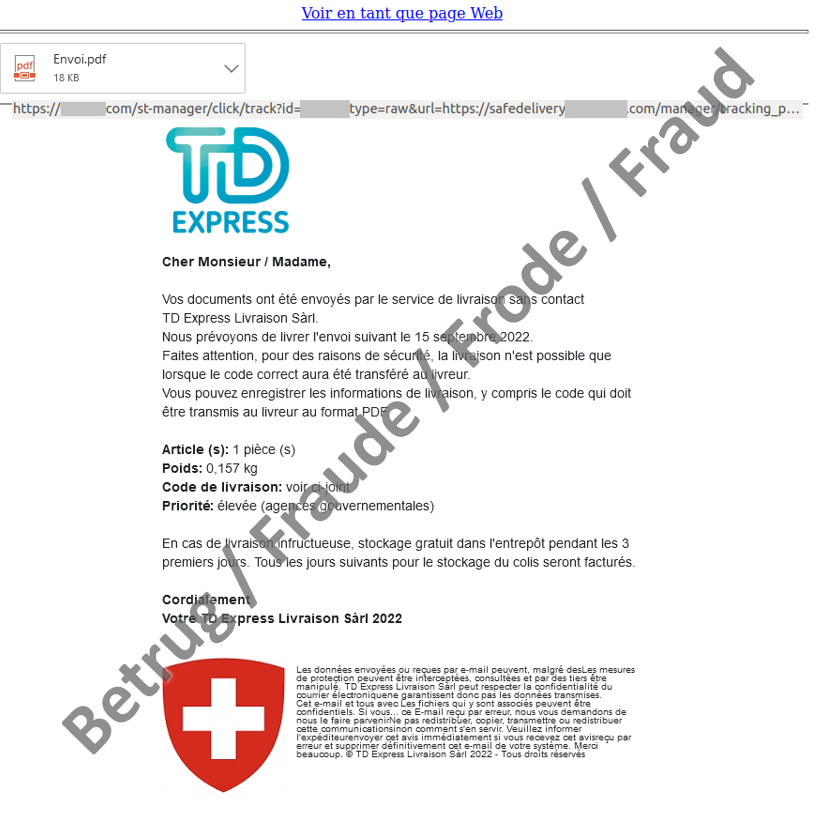
For a long time, all was quiet as regards phone calls from apparent parcel delivery services which tried to trick their victims into opening malware. No cases had been reported to the NCSC for over six months. Last week, however, a number of reports about such calls were received from French-speaking Switzerland. The current cases are similar to those reported during the wave of attacks in February 2022. The NCSC reported on this in weekly review 6. The fraudsters even reused the name of the fake parcel delivery service: TD-Express. In this type of attack, companies are called by the fictitious company TD-Express, informed that a parcel has been sent and asked to confirm the delivery. The displayed phone number, which has an 021 prefix, suggests a connection to Switzerland in an attempt to lull the victims into a false sense of security. During the phone call, the caller refers to an email that has been sent to the victim. The phone call's only aim is to gain the trust of the victim, so that he/she will click on the pdf attached to the email. Moreover, a federal logo at the bottom of the message is intended to give the email a certain official character and reinforce trust.
In the earlier variants, the email really did have a pdf attachment and the victim had to open it and then click on the link it contained. In the current variant, one click less is needed. The presence of a pdf attachment is only suggested. For this purpose, a corresponding pdf logo is inserted as an image in the email. However, the image hides a link. If the victim now clicks on the apparent pdf file, a malicious file hiding behind the link is opened and malware is downloaded. It seems that the attackers are assuming that the victim, expecting a pdf document, will happily click away from the windows that open up with queries and warnings.
In a bid to circumvent the spam filter, the email contains no text, only images. In addition to the pdf logo, the entire email text is also inserted as an image and, just in case the email program does not display these images correctly, the attackers have taken precautions. At the top, there is a link that can be clicked in case the email is not displayed correctly. It goes without saying that this link leads to the same malware as the link behind the pdf document.
This is an e-banking Trojan that tries to steal access credentials. In the past, phone calls in German have also been reported. So it is likely that, in this attack wave too, the attackers will expand their operation to German-speaking Switzerland over the next few weeks.
- Be wary of all unsolicited emails;
- Do not allow yourself to be put under pressure by the caller, especially if they want you to click on a link or open a file in an email;
- If you already clicked on the file or the link, stop using your computer – any data you enter could be diverted to the fraudsters;
- If you use your computer for payment purposes, inform your financial institution;
- Perform a full reset of your computer.
Report it:
- Report such cyberincidents to us and, if possible, forward us the email concerned.
Report an incident
Current statistics
Last week's reports by category:
Last modification 20.09.2022