27.09.2022 - The number of reports received by the NCSC declined last week. Phishing emails offering an alleged tax refund began to circulate again. In addition, several reports were received about emails from purported security researchers who claimed to have found vulnerabilities on company websites.

Purported security researchers exploit the responsible disclosure process
Security vulnerabilities are among the biggest risks in IT. This is especially true for systems that are directly accessible from the internet and thus also for attackers from around the world. According to a recent report published by Microsoft, over 80% of ransomware attacks can be traced back to general configuration errors in software and devices.
The risk of an attack can be significantly reduced if such vulnerabilities are resolved as quickly as possible and the systems are also kept up to date at all times. Fortunately, there are many security researchers who scan the internet for such vulnerabilities and notify the relevant administrators when they are found. Therefore, if someone reports a vulnerability on a website or server, you are well advised to take the report seriously, check the facts and take appropriate action as soon as possible.
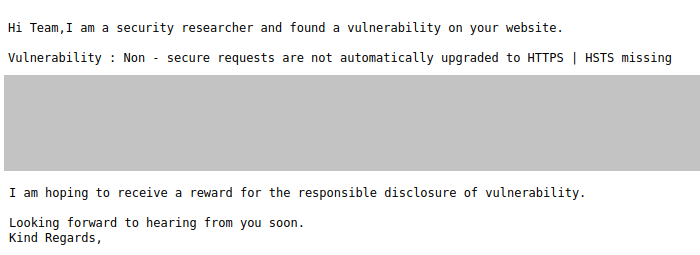
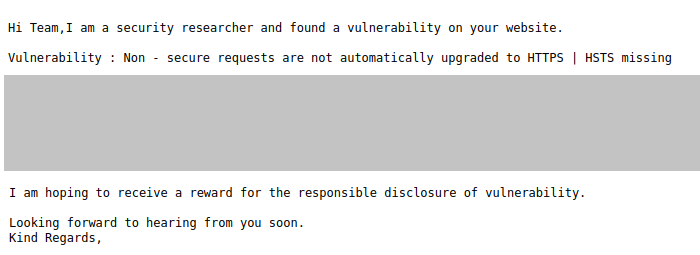
Unfortunately, in addition to reputable security researchers, there are also some people who try to make easy money by sending reports about supposed configuration errors or other security warnings. The NCSC regularly receives reports from companies that have received such notifications and are subsequently unsure how to deal with them.
In one case, a company received a notification about a supposed vulnerability on its website. The email ended with an explanation that, as part of the responsible disclosure process for vulnerabilities, a corresponding reward was expected. However, it quickly became clear that the reported "vulnerability" was merely a notification that the HTTP Strict Transport Security (HSTS) function was not activated on the company's website. If HSTS is activated for a website, an additional header is used in the HTTPS protocol that strictly instructs the browser to use only encryption from the first time the website is accessed. Although it is of course highly recommended to implement HSTS, the lack of HSTS can hardly be considered a classic security vulnerability. There are also numerous sites on the internet which can be used to check whether HSTS is implemented on a website or not; no specialised IT knowledge is required for this. It is therefore more than questionable to demand a reward in these cases. The reporters are probably speculating on companies' insecurity regarding cybersecurity matters. Since such emails are sent in large numbers, it can be assumed that some companies pay up and the reporters thus earn a few francs.
Recommendations:
- Take reports of vulnerabilities seriously, check them and take the appropriate measures as quickly as possible.
- However, do not be put off by free riders who take advantage of the situation and try to earn money with basic warnings.
Current statistics
Last week's reports by category:
Further Information
Last modification 27.09.2022