01.11.2022 - The number of reports received by the NCSC was up on the previous week. Last week, there were reports of an internet address under which several well-known financial institutions were imitated on dynamically generated websites. Such fake bank websites are mainly used for advance-fee fraud, but also for romance scams, like in this case. Also in the case of a phishing website that targeted web administrators, the fraudsters had designed the website dynamically.

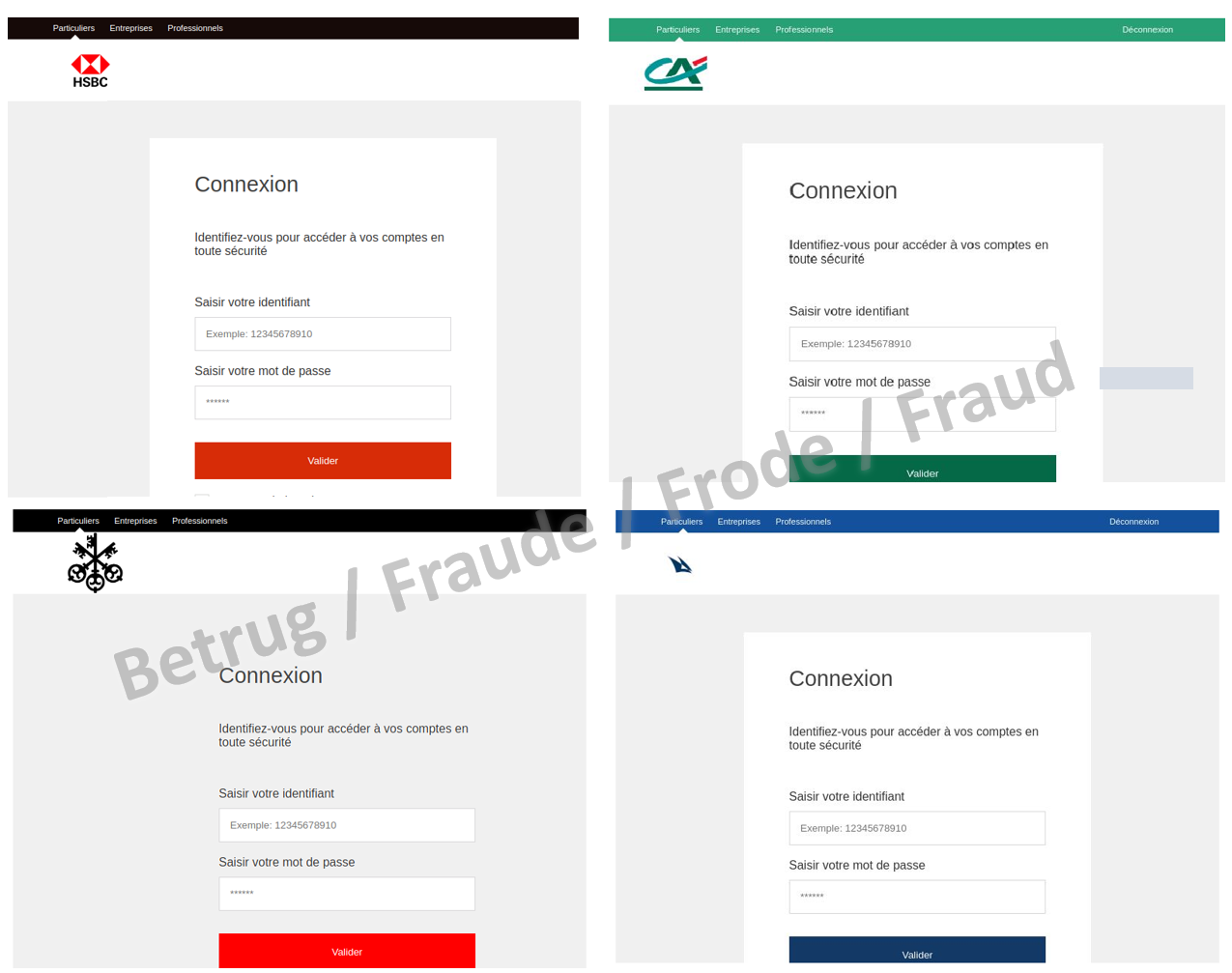
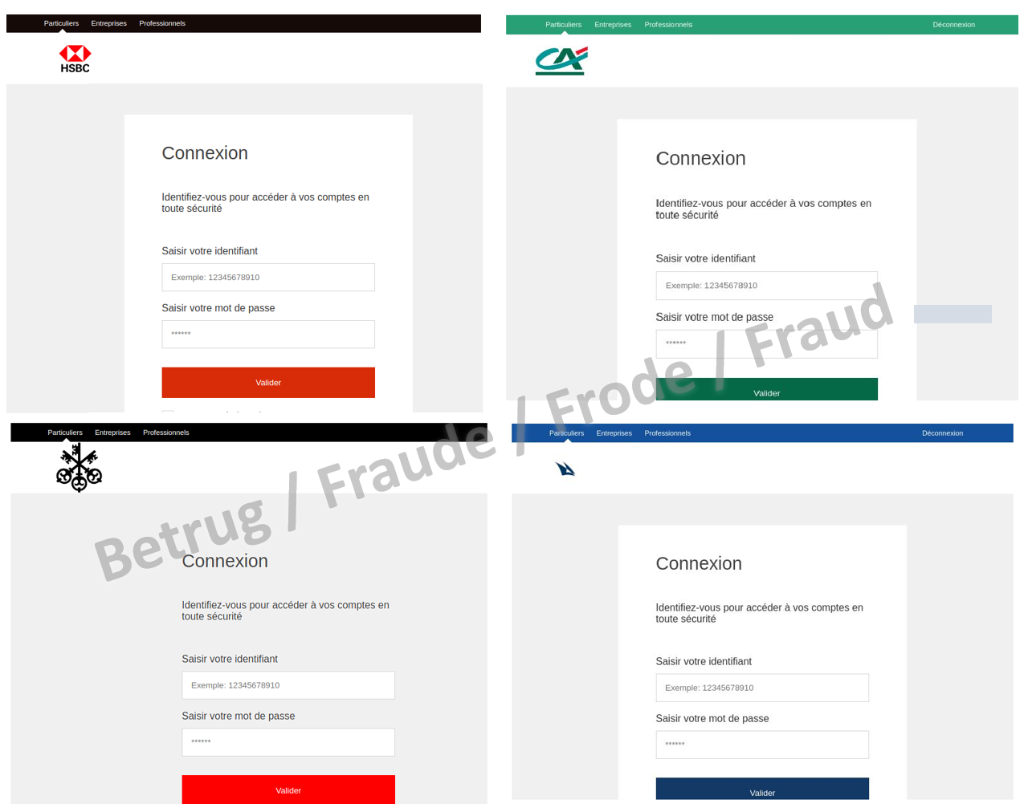
Fake bank website – one size fits all
Phishing is the first thing that comes to mind for most internet users when they think of fake bank websites. However, fraudsters also use fake bank websites for other offences. In the case of advance-fee fraud, for example, the existence of an alleged inheritance or lottery win is often backed up by a bank account on a fake bank website, where you actually see the promised sum in the supposed account.
However, the attackers use dynamic scam sites to avoid having to set up new websites for each scam. In this way, they can tailor their attack to the victim (one size fits all). In the case of Swiss victims, for instance, they do not use Swiss banks, as the victims know the banks too well or even have an account there and would notice the inconsistencies. Conversely, Swiss banks are probably used frequently to target victims abroad.
This latest case, which was reported to the NCSC last week, concerned a romance scam. In this type of fraud, fake profiles are created on social media and online dating sites in order to make other people believe the fraudster is in love with them and ultimately to obtain financial benefits. Fake banks are likewise used to gain the victim's trust and also to pretend that the supposed lover is wealthy. As a sign of trust, the fraudsters give the victims their "access credentials" and they then see the large fortune and the numerous transactions, each involving large sums of money. However, in the case of an urgent transaction, the login suddenly no longer works and the victims are asked to execute the transaction from their own account. In the case at hand, the fraudsters managed to scam over CHF 25,000.
In the case mentioned, the fraudsters set up a website where, by adding the bank's correct URL, the bank's real website was actually displayed in the lower part of the browser view. This was loaded directly from the bank's actual website in the background. However, the scammers controlled the upper bar with various links, and the supposed login link led directly to the fraudsters' login page. The NCSC noticed during its research that the page does not work with all banks. This means that an automatic mechanism is not implemented in the background. Instead, the attackers concentrated on large banks such as UBS, Credit Suisse, HSBC, BNP Paribas and Crédit Agricole, probably because these are also more familiar for the victims and thus inspire more trust.
- The NCSC informed the provider, who immediately deactivated the website, which had already been sold on 27 May 2022.
- Do not send money or goods to people you do not know and have never met before.
- Be sceptical if you receive emails that require action on your part and that carry a threat of consequences (loss of money, criminal charges or criminal proceedings, blocking of an account or card, missed chance, misfortune) if you do not do what is required.
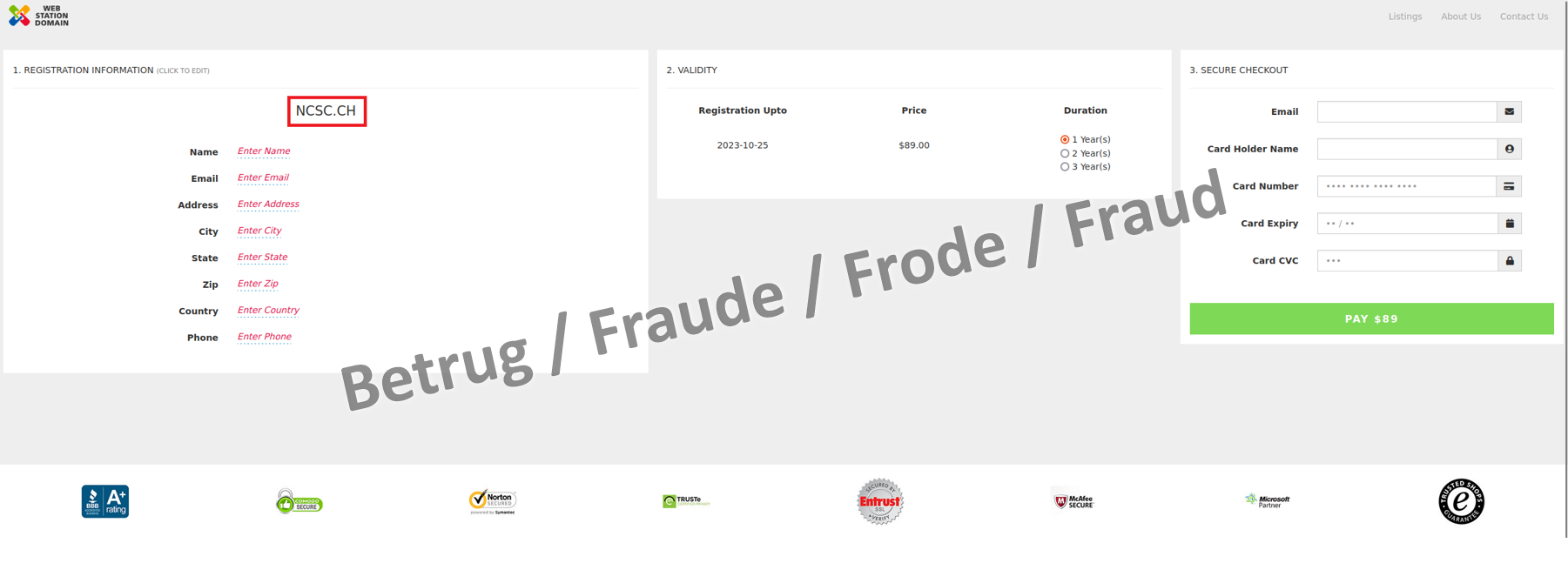
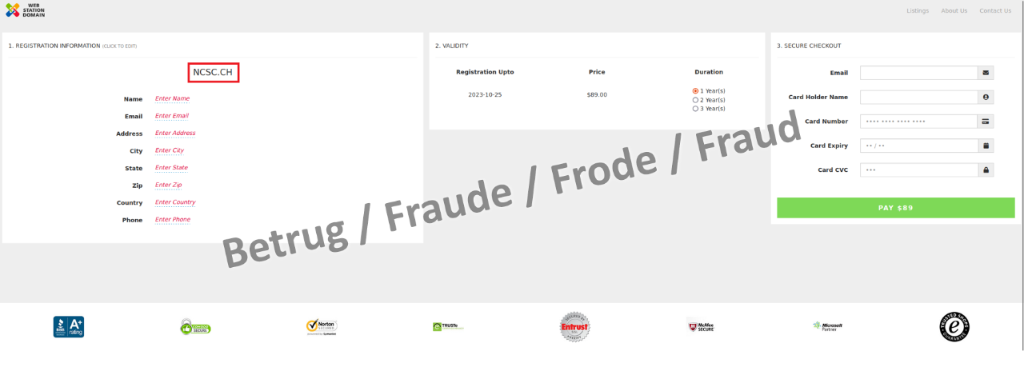
Personalised domain renewal
The NCSC also observed the use of dynamic websites in a second fraud case last week. This time, it involved a supposed domain registration renewal notice sent primarily to website administrators. Credit card details had to be provided to pay. This was thus a typical phishing attempt. Here, too, the entry of the domain name to be renewed in the address bar incorporated it directly into the form, thereby giving the impression of a personalised notice.
- No bank or credit card company will ever send you an email requesting that you change your password or verify your credit card details.
- Never divulge personal data such as passwords or credit card details on a website that you accessed by clicking on a link in an email or text message.
Current statistics
Last week's reports by category:
Last modification 01.11.2022