13.12.2022 - Last week, the NCSC received more reports than in the previous week, with 641 in total. Data leaked during data breaches can be used for targeted phishing or fraud. Therefore, regularly checking your email address for data leaks will help to protect you from unpleasant surprises.

Leaked data facilitates highly targeted attacks
A data breach occurs when data stored with an internet service provider is lost or stolen and misused for attacks. Information from over ten billion different email accounts is now on the internet – and this is only the number of known data leaks.
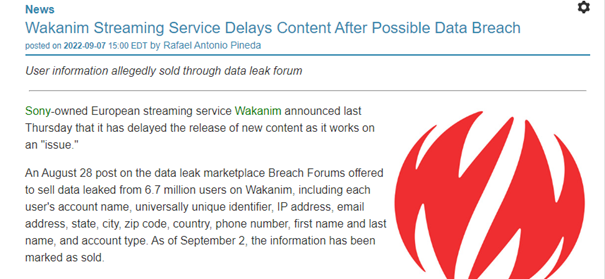
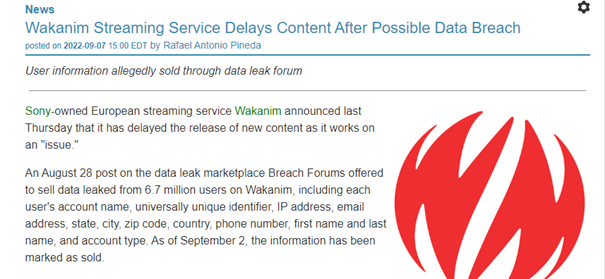
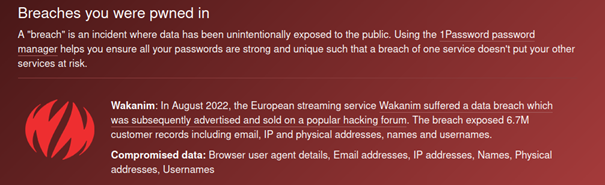
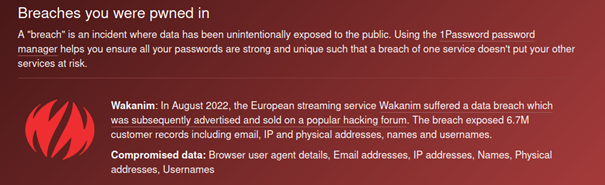
The data leaked in a data breach is offered for sale in most cases. A report received by the NCSC last week is a good example of the fact that the data can be misused not only when passwords are leaked. The report concerned a data leak involving the streaming platform Wakanim. Aside from the account names, first names, surnames, IP addresses, home addresses, telephone numbers and email addresses were also leaked.
The data from this data breach was apparently sold on the darknet as early as September 2022. However, the person who submitted the report did not find out about the data misuse until the end of October, and then only because the antivirus program on his computer flagged the data leak when scanning an email.
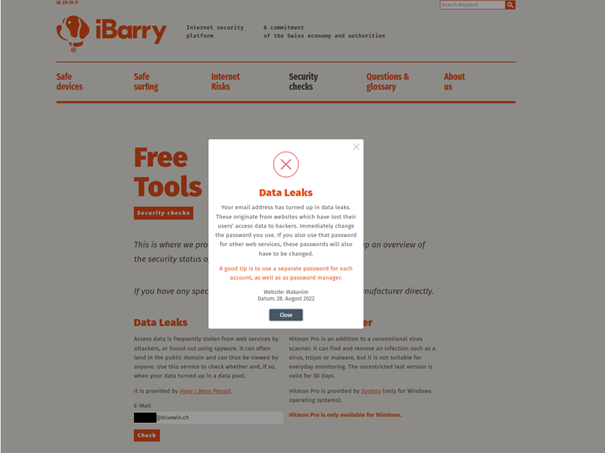
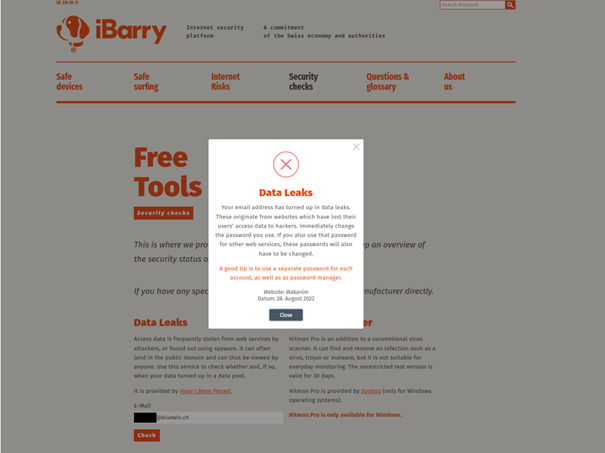
A quick check on the internet security platform iBarry.ch, an initiative launched by Swiss businesses and authorities, indicated that the email address had been leaked.
The definitive proof that the data of the person who submitted the report had been leaked from Wakanim was provided by a check directly at Have I Been Pwned – the data provider for iBarry.
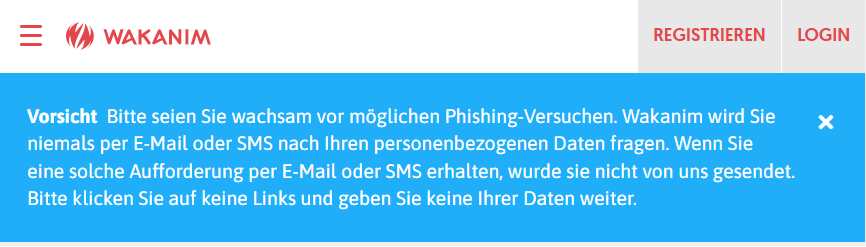
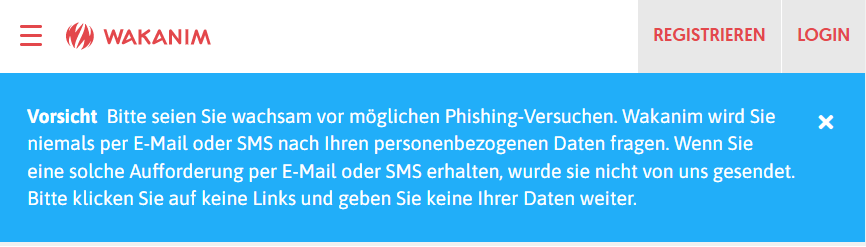
Leaked data is very suitable for targeted attacks. Such data may also be misused for fraudulent purposes. With the combination of an email address and the knowledge that the recipient is a Wakanim customer, like in the case described above, emails with content tailored to the victim can be sent to demand passwords or credit card details, for example, or to lure the recipient into opening a malicious document. The inclusion of first name, surname and address additionally generates trust, causing the recipient to think that the email must be legitimate. The NCSC is unaware of the original email in this case. However, Wakanim is currently issuing warnings about possible phishing attempts.
Data misuse cannot be prevented. However, if you know which data can be misused by fraudsters, you can exercise the necessary caution and not fall for the fraudsters' attacks so easily.
Recommendations:
- Disclose as little data as possible on the internet.
- Regularly check your email address with the available tools to see if your data has been leaked.
Current statistics
Last week's reports by category:
Last modification 13.12.2022