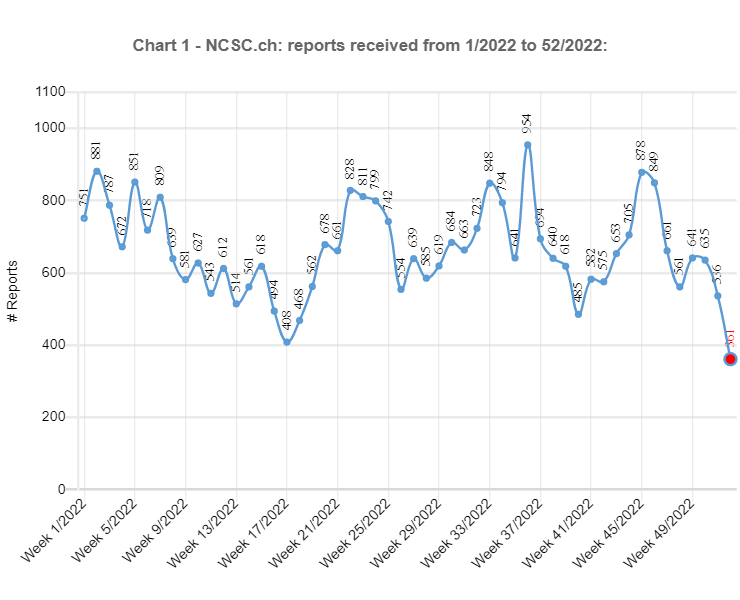
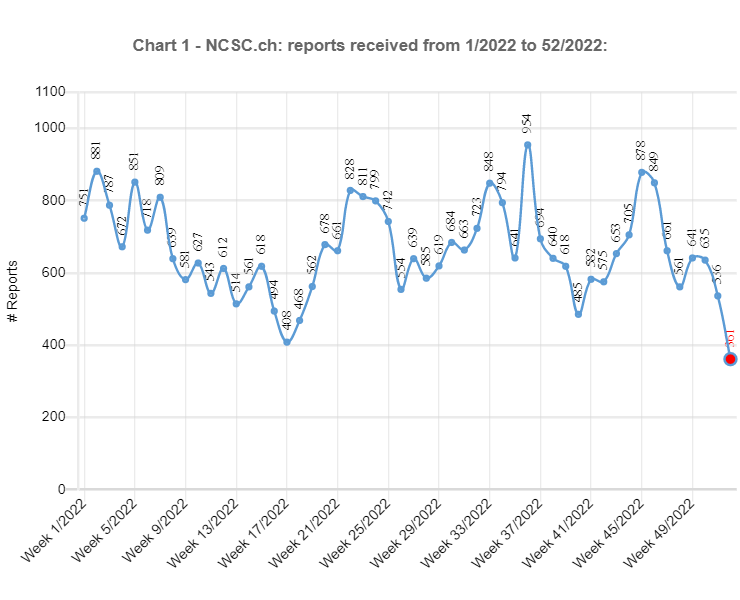
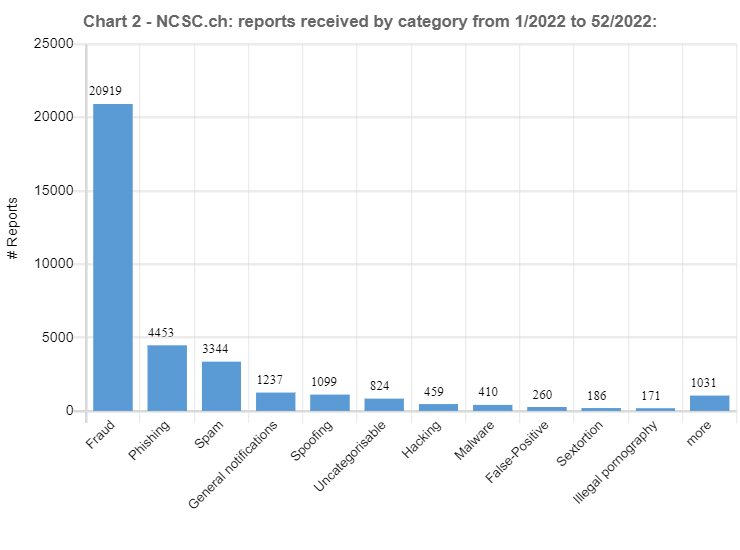
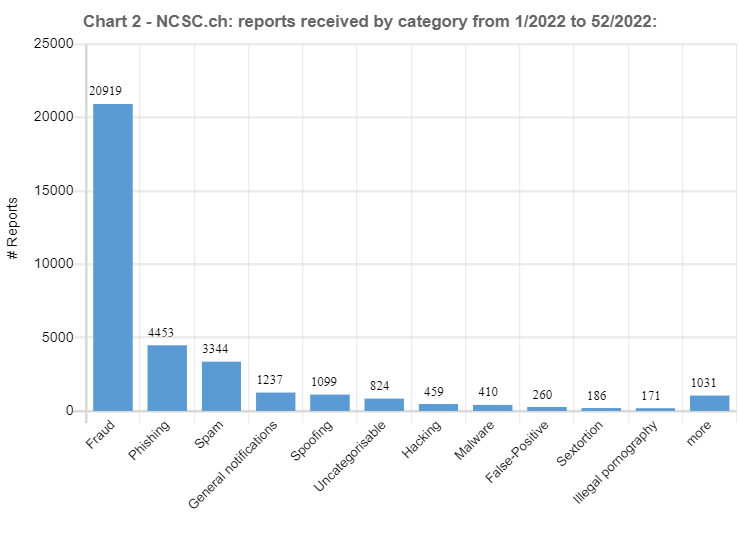
03.01.2023 - In the last weekly review of 2022, the NCSC looks back at the more than 34,000 reports received over the past twelve months. We would like to take this opportunity to thank you for all your reports. They help the NCSC to better assess the situation in cyberspace and warn potential new victims more effectively.
The total number of reports rose sharply once again this year. Although the total of more than 34,000 reports was not double the previous year's figure of 21,714, the increase of 13,000 reports in absolute terms still exceeds last year's rise (increase 2020/21 +10,881). This can be partly attributed to the growing awareness of the NCSC and its reporting form. However, there are also other reasons for the renewed surge, as shown by the examples below.
From almost 0 to 10,000 reports – Threatening emails supposedly from the police accounted for almost a third of the reports received
In the preceding year, threatening emails supposedly from law enforcement agencies, so-called fake extortion emails, were still of minor significance in terms of the reports received. The NCSC did not even have a special category for this type of fraud, and instead grouped the reports under the heading of "general fraud". These threatening emails claim that the people contacted have been found guilty of significant misconduct (typically in connection with child pornography) and that the charges against them can be dropped only if they pay money. At the end of 2021, the wave spread from France to French-speaking Switzerland and shortly afterwards to German-speaking Switzerland. This caused the NCSC to create the new "fake extortion" category in January 2022, and it was one of the categories with the most reports right from the start. Consequently, it is hardly surprising that even in the record-breaking week 36, which saw the biggest number of reports for 2022, with 954 in total, threatening emails supposedly from the police accounted for the largest share, with a total of 418 reports. Overall, more than 10,000 reports fell into this category in 2022, which corresponds to around a third of all the reports received.
Powerlessness in the face of spoofing calls
Reports concerning spoofed, i.e. falsified, telephone numbers have also virtually exploded. While just 26 reports were received the preceding year, the NCSC has received a total of over 1,100 in 2022. This is due to a new approach taken by dubious foreign call centres. In order to ensure that those called actually answer as many of their advertising calls as possible, the attackers spoof and use inconspicuous Swiss numbers. This approach is seemingly innocuous at first glance, but it has far-reaching consequences for the person to whom the number belongs. In the event of a missed call, many return the call if the number is displayed, causing the owner of the number to be inundated with calls. Since the call centres use the same number for weeks or even months, this is extremely trying for the victims.
Unfortunately, little can be done about such calls. Since the calls from the call centres originate abroad, the Swiss telephone providers' obligation to verify number use is not applicable. It applies only if the call originates from the provider's network. If the calls do not stop, the only solution is to change number.
Unchanged amount of ransomware
An increase was not observed for all phenomena. Especially in the ransomware category, the figures are virtually unchanged relative to 2021. With 159 reports received, there was even a drop of 5 reports year on year. The ratio between ransomware attacks targeting private individuals and businesses likewise remained more or less the same. Around a third of the reports concern private individuals and two thirds businesses. In the case of private individuals, the focus is primarily on attacks with the malware Deadbolt and Qlocker on network storage devices. Many of these devices are not updated by the users, or only after a time lag. If the device is still accessible from the internet, it is only a matter of time before it is attacked.
The LockBit ransomware is often used in attacks targeting businesses. Precisely this malware is known for the fact that not only is data encrypted, but it is also stolen and posted on the internet if the ransom is not paid. Such double extortion approaches are being observed more and more frequently. This trend is likely to continue in 2023. Many businesses have recognised the threat of ransomware and responded with an adapted backup strategy. Consequently, pure encryption is no longer lucrative enough for attackers. By threatening to publish the data, they are attempting to increase their profits again.
These are just a few examples of the numerous reports the NCSC received. We would like to take this opportunity to thank everyone who sent us reports. They help the NCSC to better assess the situation and to accompany our warnings with concrete examples.
The NCSC thanks you for your trust and support, and wishes you a virus-free new year, in both the digital and the physical world, and a good start to 2023!
Current statistics
Last week's reports by category:
Last modification 03.01.2023