01.03.2022 - There was a slight drop in the number of reports received last week. The likely reason for this is the adjustment of the spam policy at the NCSC, which led to a significant reduction in spam reports. Furthermore, the internet address of a payment service was laboriously falsified in a small ad scam. The NCSC shows how to recognise fake internet addresses of this kind.
Fraud with internet addresses
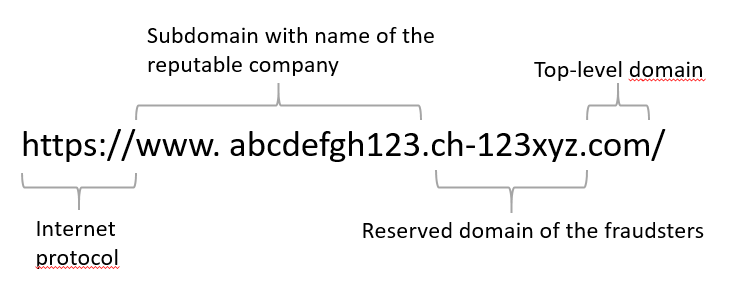
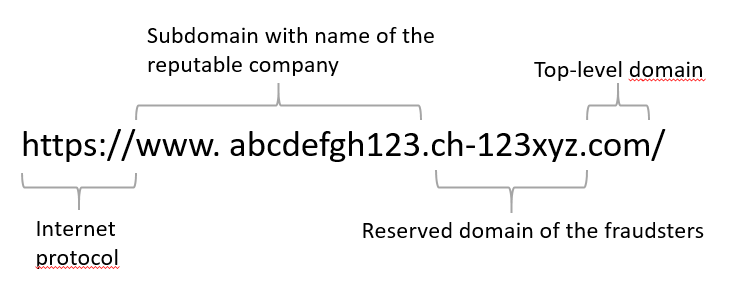
We all use internet addresses (URLs) to access online content. However, many scams rely on falsifying these URLs to lure us to fraudulent websites. It is important to note that a URL consists of the following parts: "subdomain" ("www"), "domain" (e.g. name of the company) and "top-level domain" (e.g. "ch", "com"). These three elements are always separated by a dot: e.g. "www.abcdefgh123.com".
In the case of a small ad fraud that was reported, the NCSC became aware of a fraudulent website that had been elaborately designed. The website of a reputable company was copied for the supposedly secure payment. In order to avoid making the link to the bogus website immediately recognisable as a fake, the fraudsters reserved their own domain, which followed the ".ch-123xyz.com" format. They then added the name of the reputable company to it, so that the URL appeared like this: "www.abcdefgh123.ch-123xyz.com".
At first glance, this looks confusingly similar to the address for the official website. A scam can usually be quickly identified by taking a closer look at the URL. If in doubt, always enter the actual URL of the company directly in the browser.
Other tricks used by fraudsters involving URLs:
Use of a fake top-level domain:
Another fraudulent method is the use of a fake top-level domain (e.g. .com instead of .ch). One well-known case in the past concerned the official website of the White House in the United States, which uses the URL "www.whitehouse.gov". However, on "www.whitehouse.com", which appears to be a much more frequently accessed website, sex service offers were to be found. In weekly review 5, the NCSC already reported on a bogus download page for the KeePass password manager.
Typos:
As also shown in weekly review 5, fraudsters likewise exploit typos made when entering a URL (typosquatting) by luring the victims to a website with a similar name, but which is fraudulent. A competing offer or an advertisement is then displayed, or malware is even distributed. For the website www.ncsc.ch, an inversion www.nscs.ch, a double letter www.ncssc.ch or a typo www.ncsv.ch would be conceivable.
Misuse of similar letters:
We all know that it is impossible to tell the difference between a lower case "L" and an upper case "i"; even the various "O"s and zeros are sometimes difficult to distinguish. The introduction of international characters for domain names has increased this range even further. Here are some examples of characters that can be confused with our "i": "ì", "í" and "ı".
www.example.com could be faked as: ęxąmplę.com. However, if you check this URL, you can see that it actually leads to "xn--xmpl-bta2jf.com" This is often used by scammers to deceive people.
Note:
- Report fraudulent domains to the NCSC.
- Always check the address bar in the browser to make sure you are on the right page, especially if you have to enter your login credentials and/or credit card details.
Current statistics
Last week's reports by category:
Last modification 01.03.2022