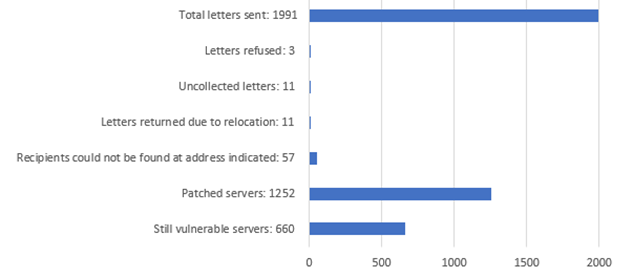
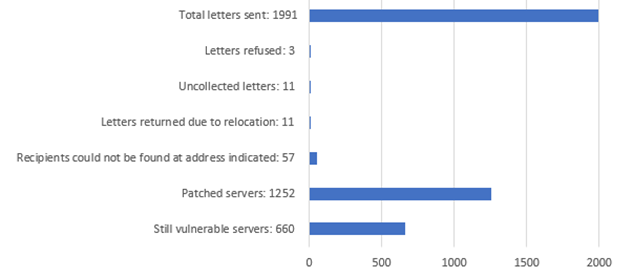
02.02.2023 - Back in November 2022, the National Cybersecurity Centre (NCSC) indicated that more than 2,800 Microsoft Exchange servers in Switzerland were vulnerable because of the critical vulnerability called ProxyNotShell. A month later, the NCSC sent registered letters to around 2,000 operators, asking them to patch the vulnerability. Nevertheless, the message has still not got through to everyone. More than 600 servers in Switzerland are still affected by the gateway for cybercriminals.

Microsoft announced in September 2022 that there was a critical vulnerability called ProxyNotShell in Microsoft Exchange servers and belatedly released a security update in November 2022. The vulnerability has been actively exploited by cybercriminals for quite some time (zero-day exploit), which is why it is very important to fix the problem quickly. Although the Microsoft patch has been available for several months, 660 servers in Switzerland are still vulnerable.
Install the update as quickly as possible
This number is worrying, as the NCSC has been warning about this vulnerability at regular intervals for the past two months and has also sent registered letters to the operators, personally asking them to patch the vulnerability. Every day, each of these 660 servers is at risk of falling victim to a cyberattack. For this reason, the NCSC recommends patching the vulnerable servers as quickly as possible.
Post the correct security contact
In addition, the NCSC recommends that the security.txt standard should be used to store the security contact for all online applications and websites, and that the accuracy of the address should be verified in the Whois domain database. This is the only way to ensure that the NCSC can contact the person responsible as quickly as possible the next time there is a threat. Otherwise, the NCSC's only option is to send registered letters. Due to incorrect address information, 83 of the roughly 2,000 letters sent could not be delivered.
Recommendations on what to do:
The NCSC recommends that operators of Microsoft Exchange servers should ensure that all patches have been installed. Highly critical patches should be applied as quickly as possible, i.e. outside the regular maintenance windows.
Microsoft Exchange Server Remote Code Execution Vulnerability (ProxyNotShell):
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-41082
- Make sure that you have applied a current Cumulative Update (CU) with all corresponding Security Updates (Nov22SU).
- Check your Exchange Server with the Health Checker provided by Microsoft:
https://microsoft.github.io/CSS-Exchange/Diagnostics/HealthChecker/ - Scan your Exchange Server with up-to-date antivirus software.
- Review your patch strategy and ensure that critical security updates are installed outside of maintenance windows.
Last modification 02.02.2023