10.01.2023 - With a total of 559 reports, the number of reports received by the NCSC in the first week of 2023 has increased again compared to the previous week. A report on a Google search that returned dubious search results turned out to be a case of search engine manipulation. Numerous websites were hacked with the aim of tricking Google's search algorithm.
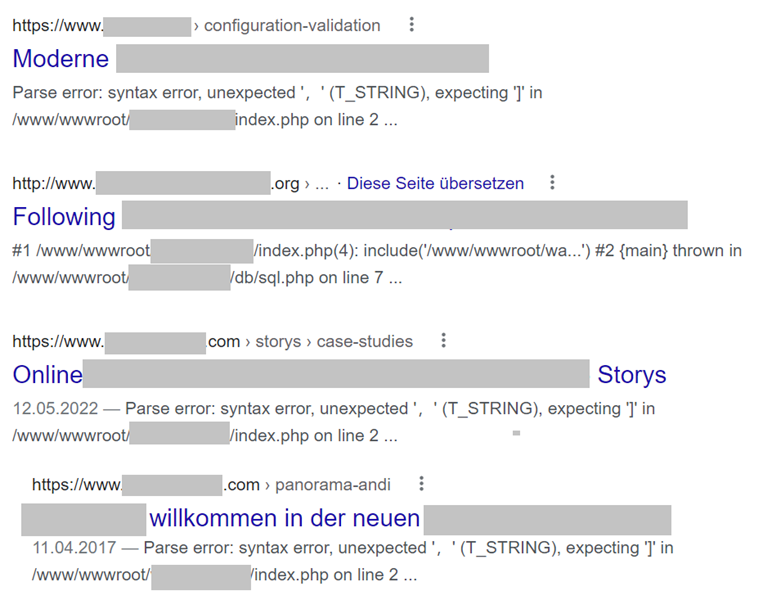
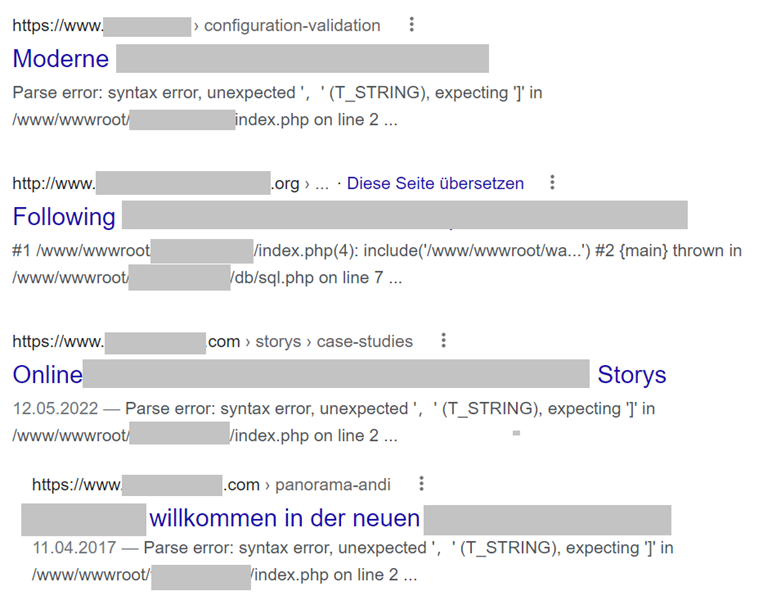
Last week, the NCSC received a report indicating that a Google search for a school was producing dubious search results. The main thing that stood out was a suspicious JavaScript file. A Google search for the suspicious domain in this file showed no fewer than 5,500 websites that followed the same pattern: Google displayed the correct title of the website found in the results, but instead of the usual extract from the website content, various error messages were displayed below the title. If the website was opened using Google Cache – a copy of the website cached by Google – the error messages were also displayed. However, if the website was opened directly by entering the URL, the website was displayed without any error messages.
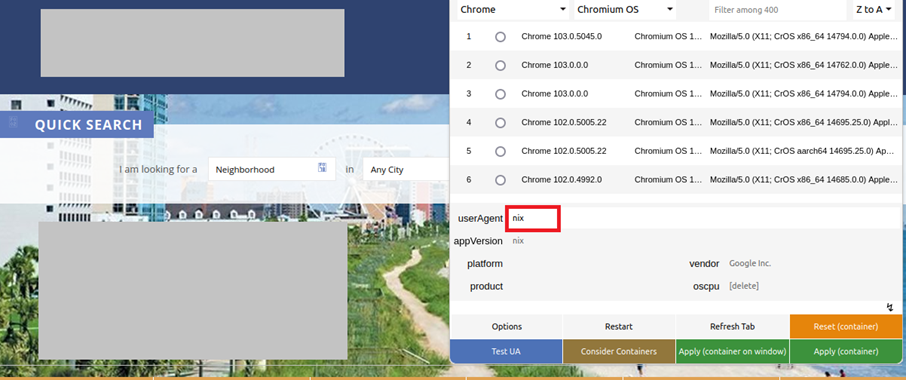
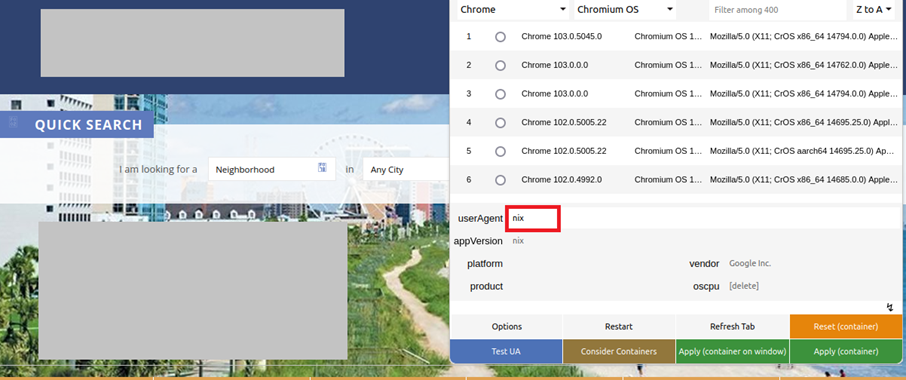
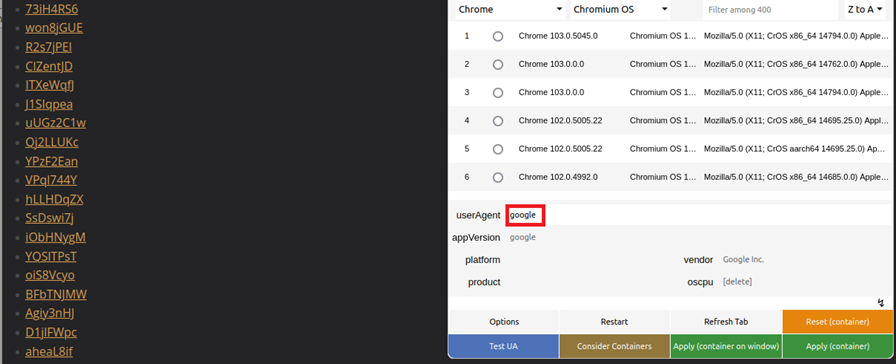
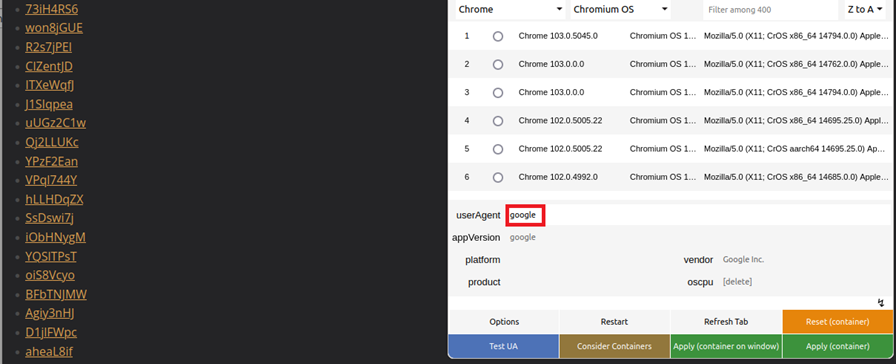
It was assumed that, in this case, different page contents would be displayed – depending on the "user agent". The user agent is sent every time a website is called up and provides the web server with information about the visitor's operating system and the browser. In addition to statistical surveys, such data can also be used to optimise website content for a specific browser type. Particularly in web design, this is used to distinguish between notebooks, tablets and mobile phones, and to adapt the website content to the respective screen format, for example. Search engines also use a special identifier when browsing the internet and thereby identify themselves as such.
A test with the websites found confirmed the suspicion: opening the website with a user agent of a common browser (here marked with "nix") led to the expected website being displayed correctly.
However, if the user agent was set as Google, the website's appearance changed completely. Instead of the content, a series of links was displayed, hidden behind combinations of letters and numbers.
Search engine optimisation
But what are the attackers intending to achieve with this approach? It is a classic attempt to manipulate search engine results. Search engine optimisation comes in many different guises. In the current case, the attackers used hacked websites and injected malicious code to trick Google and improve the ranking. This increases the chance that potential victims will click on the manipulated search results and thus end up on dubious websites. A noticeable number of the affected websites were operated by Kentico CMS software. Unpatched vulnerabilities in this CMS are likely to have been the reason behind the manipulated websites.
The injected malicious code checks the user agent. If the request comes from Google, the links described above are displayed, which are saved and indexed by Google. Since the same links are always displayed on the various hacked websites, Google assumes that they are of interest and rates them as more relevant than they actually are. The links move up in the search results accordingly and then reach more people. For all other visitors to the website who use a direct URL to access it, as well as for the website owner, the normal content is displayed. This way, the manipulation is less noticeable and can maintain its effect over a long period of time.
Recommendations for website operators:
- Attacks on content management systems can be reduced dramatically by promptly installing security patches.
- In addition to normal authentication (username and password) for accessing the administration area, the NCSC recommends the use of two-factor authentication.
- Administrator access should be restricted to the IP addresses used by the administrators.
Further information on protecting the CMS can be found on:
Current statistics
Last week's reports by category:
Last modification 10.01.2023