23.05.2023 - Phishers are constantly trying new ways to trick victims into providing their access details. In doing so, they also do not shy away from telling the victim that intimate pictures have supposedly been published. However, things do not always go according to plan, as a second example reported to the NCSC last week demonstrates.

Phishing with threat
Never divulge personal data such as passwords or credit card details on a website that you have accessed by clicking on a link in an email or text message. This simple basic rule will already prevent many phishing attempts.
Thanks to internet users being ever more aware, many now react sensitively to classic phishing emails that threaten to block an account or offer the prospect of a refund, for example. The attackers therefore try to catch the recipients off guard with a stream of new stories and exploit the brief moment when the victims are unsettled, do not pause to think about the plausibility of the story and therefore do not suspect anything.
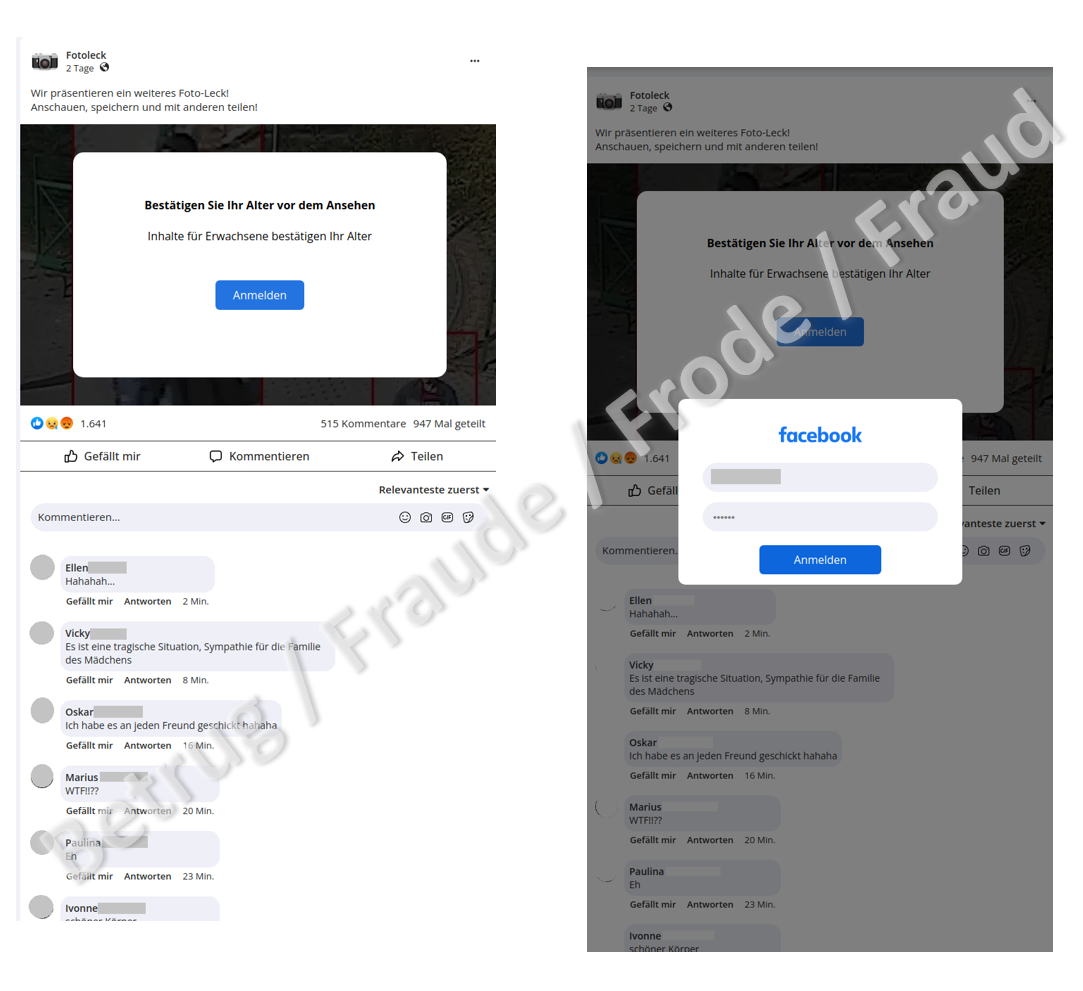
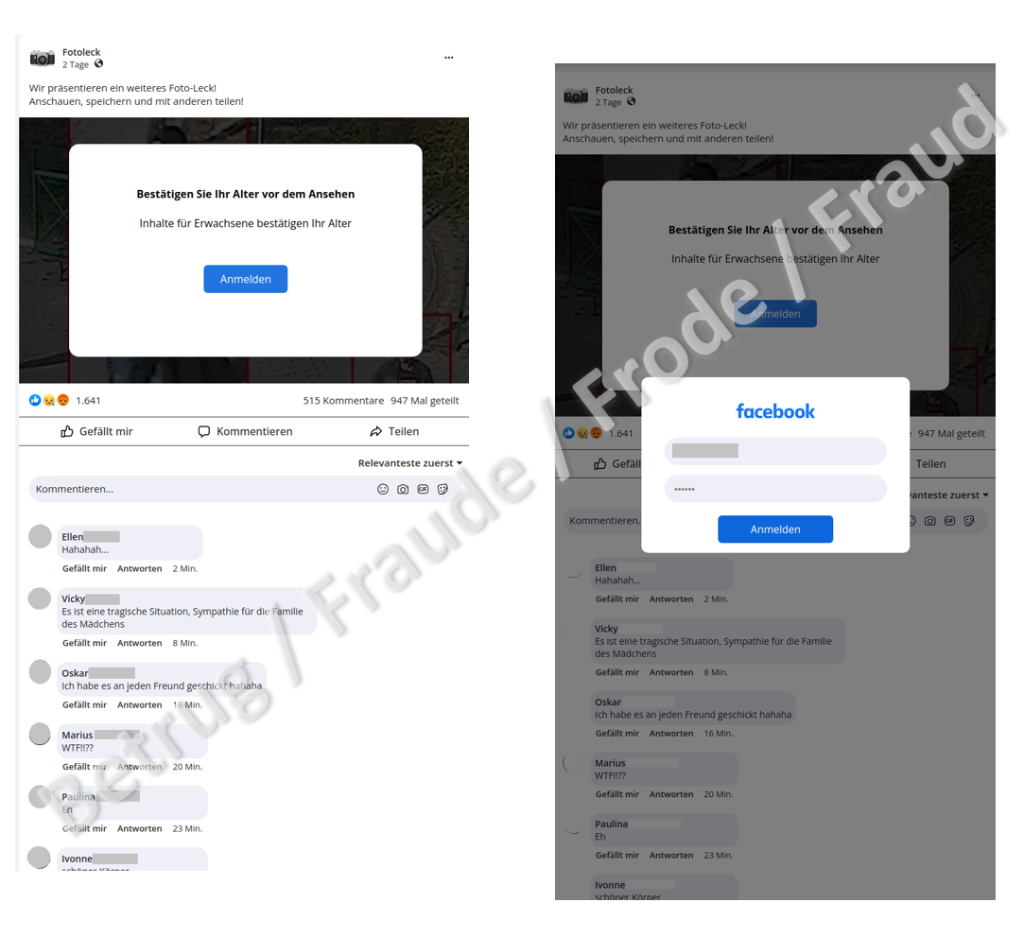
A particularly perfidious case was reported to the NCSC last week. In the name of a person who was "friends" with the victim, the victim was told via a Facebook message that someone had posted nude photos of them on the internet. In order to see the photos for themselves, they were told to click on the link provided. The page that then opened mimicked Facebook and contained numerous comments which did indeed suggest that the content contained compromising images. These comments and the indication that the content had already been shared 947 times were intended to put the victim under pressure. However, in order to view the images, they first had to confirm their age, as it involved adult content. To do this, they had to provide their Facebook login details. In this case, of course, this information did not go to Facebook, but directly to the attackers. The whole page was a bluff to make the victim feel insecure. After the login details had been entered, a page appeared saying that the photos had already been removed.
As mentioned above, the victim was tipped off about the page with the alleged nude photos by a Facebook acquaintance, giving the message even more credibility. The NCSC assumes that the purported sender had also been previously phished and that the contact details are being used to send more targeted phishing messages.
Oops! – Phishing email addressed to the wrong person
Phishing attempts with real names are still rare. In many cases, the fraudsters use an impersonal "Hello" or "Hi customer", or use the information from the email address to display a more or less appropriate form of address.
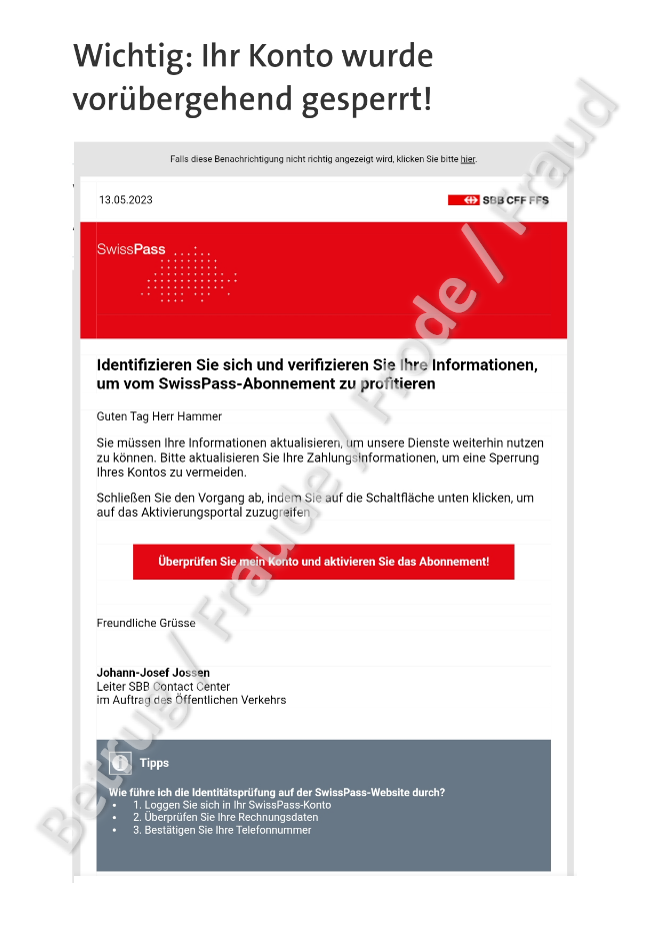
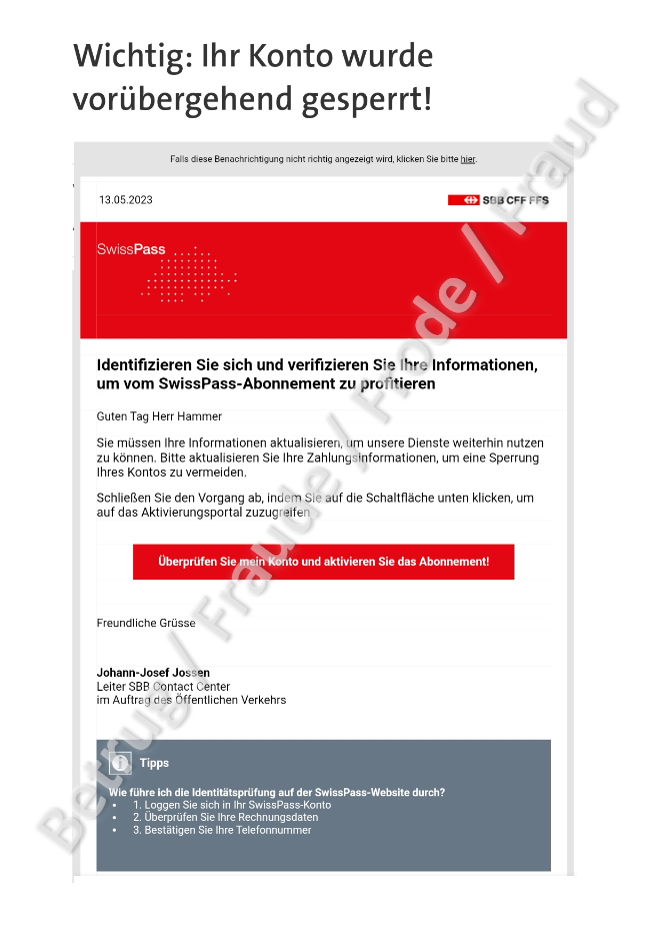
Last week, a new variant of the well-known SBB phishing attempt appeared, luring people with an alleged ticket refund or threatening to block their Swisspass account. In the current variant, the victim was addressed personally. At first, it had to be assumed that the fraudsters were using data from a data leak, which makes a very targeted attack possible. However, after the initial reports received by the NCSC, it quickly became clear that the same surname was always used as the form of address, regardless of the name of the recipient.
This error by the attackers is an example of how they operate. They hack into email accounts and search the inbox for useful material. Emails from companies, in this case a ticket refund from the SBB, are of course of interest to the fraudsters and are subsequently customised and a phishing link is added. In this way, the fraudsters do not have to worry about the accuracy of the language. These emails are written in perfect German, French or Italian, except of course for the sections that have been adapted by the fraudsters. In this case, the attackers used "Mr Hammer" everywhere and forgot to personalise it.
This case also shows how important it is to send reports to the NSCS. It was only thanks to the numerous reports we received that the NCSC was able to quickly assess the case and recognise that these were not targeted attacks, and to issue the relevant warnings.
- Never divulge personal data such as passwords or credit card details on a website that you have accessed by clicking on a link in an email or text message.
- Wherever possible, use two-factor authentication. This offers an additional layer of protection to prevent your account from being hacked.
- No bank or credit card company will ever send you an email requesting that you change your password or verify your credit card details.
- Bear in mind that email sender IDs can easily be spoofed.
- Be sceptical if you receive emails that require action from you and otherwise threaten with consequences (loss of money, criminal charges or legal proceedings, account or card blocking, missed opportunity, misfortune).
Current statistics
Last week's reports by category:
Last modification 23.05.2023