24.01.2023 - QR codes are becoming increasingly popular and are used for various purposes. They are used not only to provide links to websites, but also to organise entire logistics processes. QR codes have also found their way into invoices. Effective since 1 October 2022, only invoices with QR codes are accepted in Switzerland. Clearly, QR codes can also be misused, as illustrated by two examples reported to the NCSC last week.
Week 3: From invoice manipulation to subscription scams – a growing number of different types of fraud using QR codes

Business email compromise – with a remarkably authentic-looking invoice – now including a QR code as well
Attackers are increasingly scouring hacked email accounts for sent invoices or payment instructions. If they find them, they copy and manipulate the invoice. The fraudsters change the IBAN indicated on the invoice to which the amount is to be paid and re-send it to the victim in the name of the actual invoice issuer on the spurious grounds that the beneficiary account has changed. The recipient is now supposed to pay the amount into the new account, which is actually the fraudsters'.
Until recently, the attackers in this sort of invoice manipulation scam, also called business email compromise, confined themselves to changing the IBAN in the invoice or simply indicated to the invoice recipient that the amount should be transferred to another account. However, a case reported to the NCSC last week was different. The invoice was manipulated and looked remarkably authentic. Not only was the IBAN changed, but the QR code was also adapted accordingly. In addition, the amount was supposed to be paid into a Swiss account, which made it difficult for the victim to spot the fraud attempt.
- Raise the awareness of all employees, especially those in finance divisions and key positions, about these possible methods of attack.
- Ignore unusual payment requests.
- In the case of unusual requests within the company, check by telephone that the request is genuine.
- All processes which concern payment transactions should be clearly defined internally and complied with by employees in all cases (e.g. dual control principle, joint signature by two people).
When the QR code suddenly takes you to the wrong page
Last week, the NCSC also received reports about an information letter from a company that was sent by post. To make it easier for recipients to respond, the letters contained a QR code enabling them to go directly to the correct feedback page without the hassle of typing it. However, some recipients complained to the sender of the letters that they were taken to a dubious site that required credit card details.
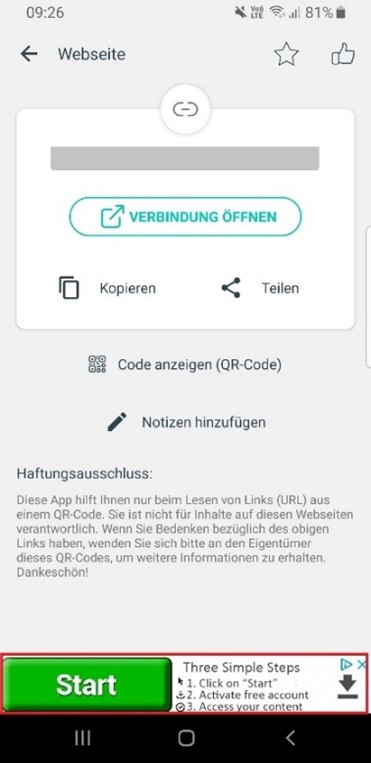
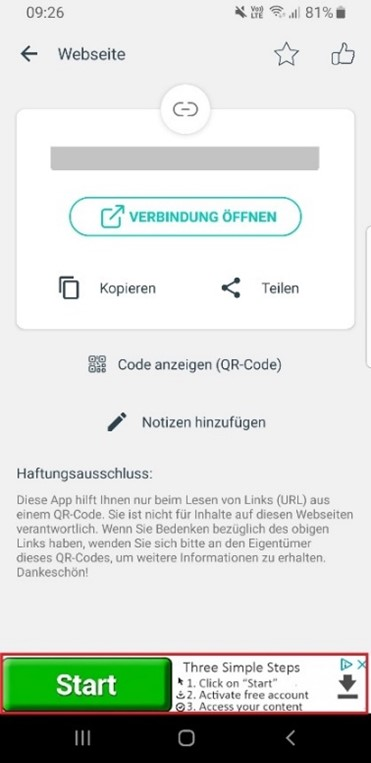
The underlying reason was unclear at first. Manipulation of the QR code itself was quickly ruled out. The QR code was identical in all of the letters, including those sent to the people who had noticed the suspicious behaviour. Consequently, the QR scanner came under suspicion, especially since all of those affected had always used the same QR scanner. The NCSC then took a closer look at the QR code scanner, but there were no irregularities in the scanning process and the link was reproduced correctly. However, it was conspicuous that an advertisement was displayed in the lower part of the screen whenever the link was accessed. Some of these advertisements were designed to confuse the user and suggested that the advertisement was an official part of the app.
Specifically, in addition to the genuine "Open connection" link, which is outlined in an inconspicuous light blue, a "Start" button is displayed at the very bottom in vivid green. If people are stressed and do not look closely at the page, they inevitably press the button that is the most conspicuous. This is precisely what the people who place these advertisements are after. They buy advertising space with the intention of confusing users and thus tricking them into clicking on the dubious link – in this case, a subscription scam. The providers, who make their space available for advertising and thereby finance the app, can do very little about this, as they commission the advertising through third-party companies. They have no influence on the content.
The advertisements placed are always very small and are therefore hardly noticed.
- Use a reliable app that is recognised as secure to scan QR codes. The advantage of this is that your device will ask you to confirm the action before the code contained in the QR is executed. Both Apple and Android also allow the camera to recognise QR codes.
- After scanning and before execution, most scanners will display the action to be performed or the page to be accessed. Check this information.
- Never enter login credentials on a website that you accessed via a QR code.
- Before scanning a QR code, take a close look at it or touch it to see if it is not just a sticker that has been affixed to the original.
- If you scan a QR code that contains something malicious, immediately notify the owner of the place (magazine, website, etc.) where you discovered it.
Further information can be found on our website at:
Current statistics
Last week's reports by category:
Last modification 24.01.2023