29.08.2023 - Fraudsters use various methods to optimise their spam lists. Last week, the NCSC discovered scam emails that exploit the read receipt function. In these cases, if the recipients confirm that they have opened and read the email, they receive further scam emails that increase the pressure and urge them to pay.

Fraudsters use various methods to have spam lists that are as promising as possible. For example, they check whether the email was actually delivered, whether the recipients received and opened the email, and whether they clicked on the link. So-called external content, for example, has been used for quite some time to confirm receipt of an email. In this case, visible or "invisible" images are integrated into the email and are loaded from a server that is controlled by the spammers when the email is opened. If these links are personalised, the attacker can see precisely which emails were opened and which were not. Recipients who opened the email are very likely to receive even more fraudulent emails. Aside from the confirmation, the attackers also receive information about the browser and operating system used. As a result, they not only know which people are vulnerable to fraud, but can also target their future attacks very specifically to the operating system used. Moreover, phishing or fraudulent emails with personalised links are increasingly being observed. In this way, the attackers can see exactly which recipients have taken the bait or have at least fallen for the first step of the scam.
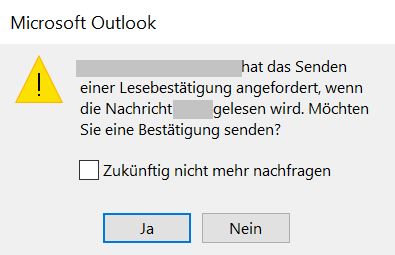
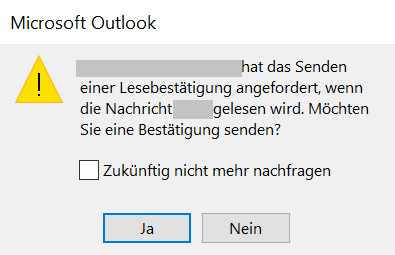
Last week, the NCSC received reports about scam emails that use a different method to spy on user behaviour. For example, a read receipt was requested in several cases of the well-known fake threatening emails from authorities. This message disposition notification (MDN) is used to transmit to the sender confirmation that an electronic message has been received once the message has actually been opened and viewed. If the recipient deletes or ignores the email already at the preview stage, no confirmation is sent. In this way, attackers can perform an initial triage and see with which recipients the attack will fail and with which they have a chance of the recipients falling for it.
The reports from people who opened such a threatening email with a read receipt show that this function is actually used by fraudsters. Another email that made reference to the first one followed after a short time to step up the pressure. Thanks to the read receipt, the attackers know that the victim at least opened the email.
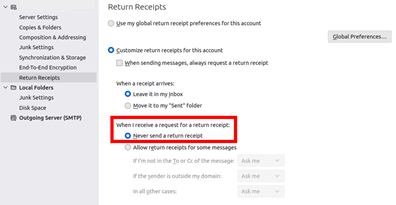
Disabling the read receipt certainly makes sense in many cases. However, you should at least configure it so that you are asked each time whether a read receipt should be sent.
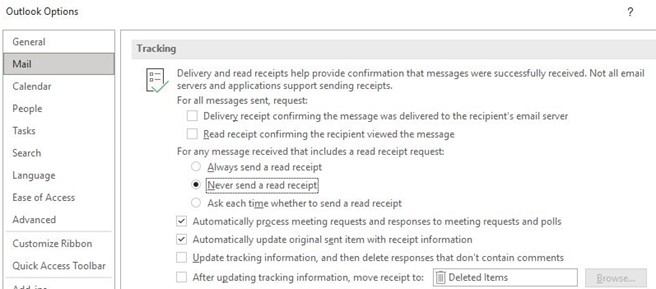
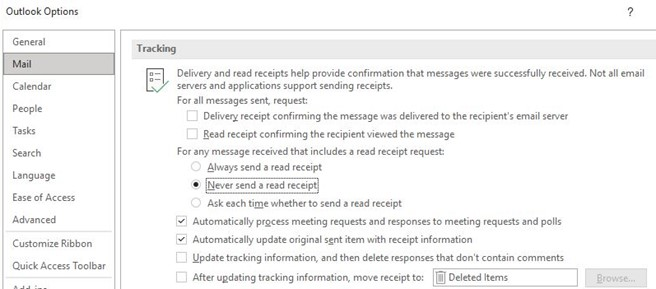
In Outlook, you will find the corresponding function under "File", "Options". Select "Mail" and scroll down to "Tracking", where you can switch off the read receipt function completely or specify that you are to be asked each time whether a read receipt should be sent.
Recommendations:
- Disable automatic read receipts in your email client.
- Do not click on the link in phishing and scam emails, not even to test it.
- Ignore and delete familiar scam emails already at the preview stage.
- Disable external content in your email. This function is already disabled in most email clients.
Current statistics
Last week's reports by category:
Last modification 29.08.2023