31.01.2023 - The number of reports received by the NCSC fell slightly again in the fourth week of 2023, with 716 reports. In a recent case, a bogus receptionist contacted a hotel guest in order to obtain credit card details and to persuade him to make an additional payment. Following on from such cases being observed in France in recent weeks, a case has now also been reported in Switzerland. The guests' booking data is stolen in advance from the affected hotels by the RedLine Stealer malware.

Re-emergence of a scam – hotels and hotel guests targeted by cybercriminals
Three years ago, a scam was already doing the rounds in which fraudsters randomly called hotel guests and pretended to be a receptionist. For this purpose, the fraudsters simply speculatively dialled the number of the hotel and asked to be put through to a randomly chosen room number. Some hotels even (still) provide the direct extension numbers for their rooms on their homepage. The purported hotel employees then pretended that they had made a mistake when charging the credit card and would therefore have to make the booking again. The hotel guests were then pressured on the phone into giving their credit card details including security features.
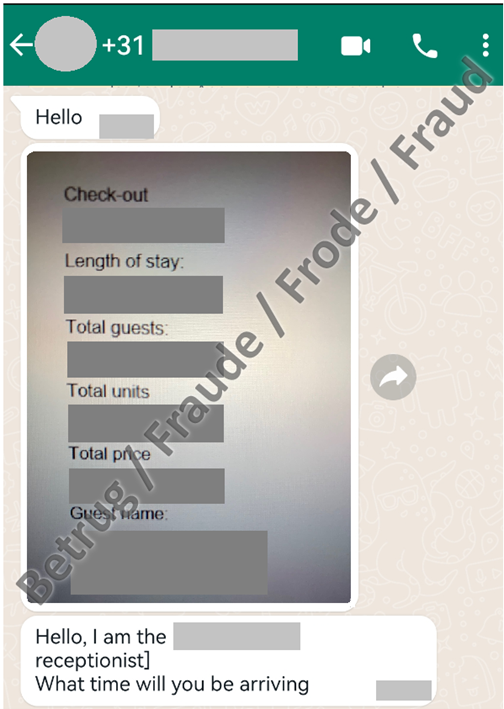
Three years later, the fraudsters have now refined this scam. In a new variant, which had already been observed in France over the past few weeks and was also reported to the NCSC for the first time last week, the approach is similar. People who have booked a hotel are contacted via WhatsApp and drawn into a chat. The attackers know all the booking details and use this information to convince the other person that the request really is from the hotel. In this specific case, the reporting party booked a hotel in Bern and received a response from the purported receptionist via WhatsApp on the same day. The attackers were able to provide information on the specific travel dates, the guest's address and even the hotel costs. After initially harmless questions about the arrival time, they asked for credit card details and urged the victim to make a payment. In this case, the victim was contacted from a Dutch telephone number. This made the victim suspicious and the conversation was then ended.
RedLine Stealer malware stealing booking data
The question is how the attackers were able to access the booking details. The reservations in both the recent case and the cases observed in France were made via the booking.com portal. The suspicion was therefore that the attackers were able to gain access to the hotel's booking.com account, perhaps by phishing for these access details in advance. Latest reports indicate that login details are being stolen from hotels by the RedLine Stealer malware. The malware collects information from browsers, such as stored login details, auto-fill form data and credit card information. To persuade hotel employees to click on the malicious file, they are contacted by supposed guests who want to know the hotel's location or cancel a reservation. They are then persuaded to open a file and thus install the malware. The attackers then have access to various hotel accounts and can commit further fraud.
Recommendations:
- Never disclose credit card details or passwords when prompted by email, phone or a messenger service.
- Beware of emails that require action on your part and be careful if you are urged to perform an action. This may involve clicking on a link or opening an attachment, for example.
- Bear in mind that email and text message sender IDs can easily be spoofed.
- Even the telephone numbers shown when making or receiving a call can be easily faked.
- Never enter personal data such as passwords or credit card details on a website that you have clicked on via a link in an email or text message.
- Install two-factor authentication whenever possible. This offers an additional layer of protection to prevent your account from being hacked.
- No bank or credit card company will ever send you an email requesting that you change your password or verify your credit card details.
Current statistics
Last week's reports by category:
Last modification 31.01.2023