21.11.2023 - A number of phishing cases were also reported to the NCSC last week. Fraudsters continue to target customers of parcel, telephony and transport service providers very frequently. This weekly review presents two less common phishing scams.

Purported tax refund
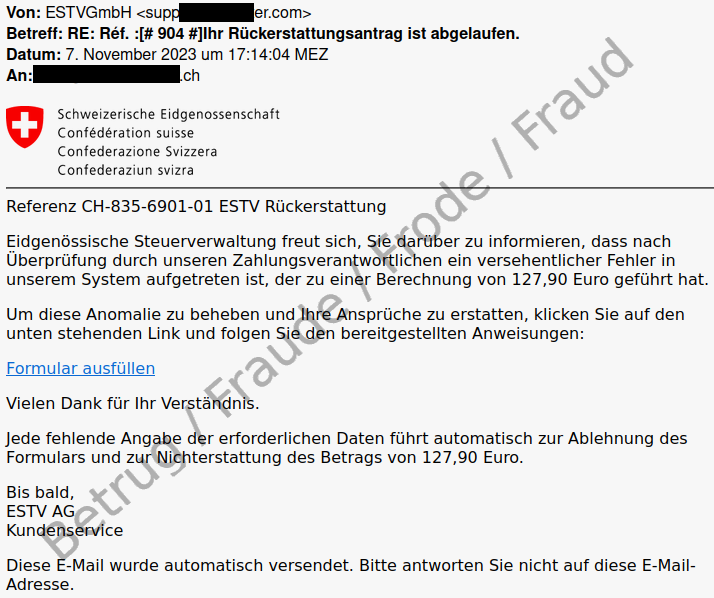
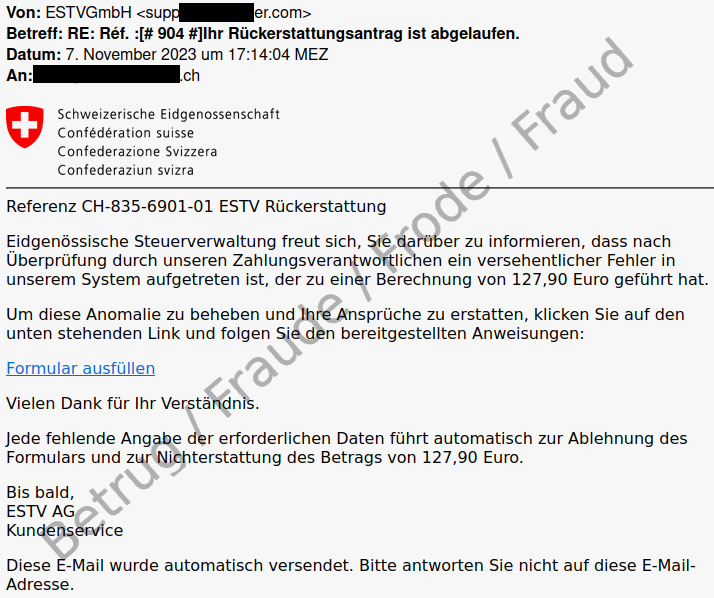
An email claims that the recipient is entitled to a credit note (refund) from the Federal Tax Administration (FTA). The following image shows such an email. However, the sender, which does not look at all like it is the FTA, is enough to make anyone suspicious. Even if you do not know the exact domain of the FTA, federal services and websites are always found at admin.ch, never at *.com.
If you move the mouse over the link (without clicking), the URL to which the link would lead is displayed. Here too, the URL/target domain have no connection with the FTA. Even just one of these features alone (sender or URL) indicates that this is a fraud attempt.
If you take a closer look at the email, you will notice that the fraudsters have made a number of mistakes:
- The FTA is not a GmbH or AG.
- Any tax refunds would be made in Swiss francs and not in euros.
- The language used in the email does not reflect that of an official notification from the authorities.
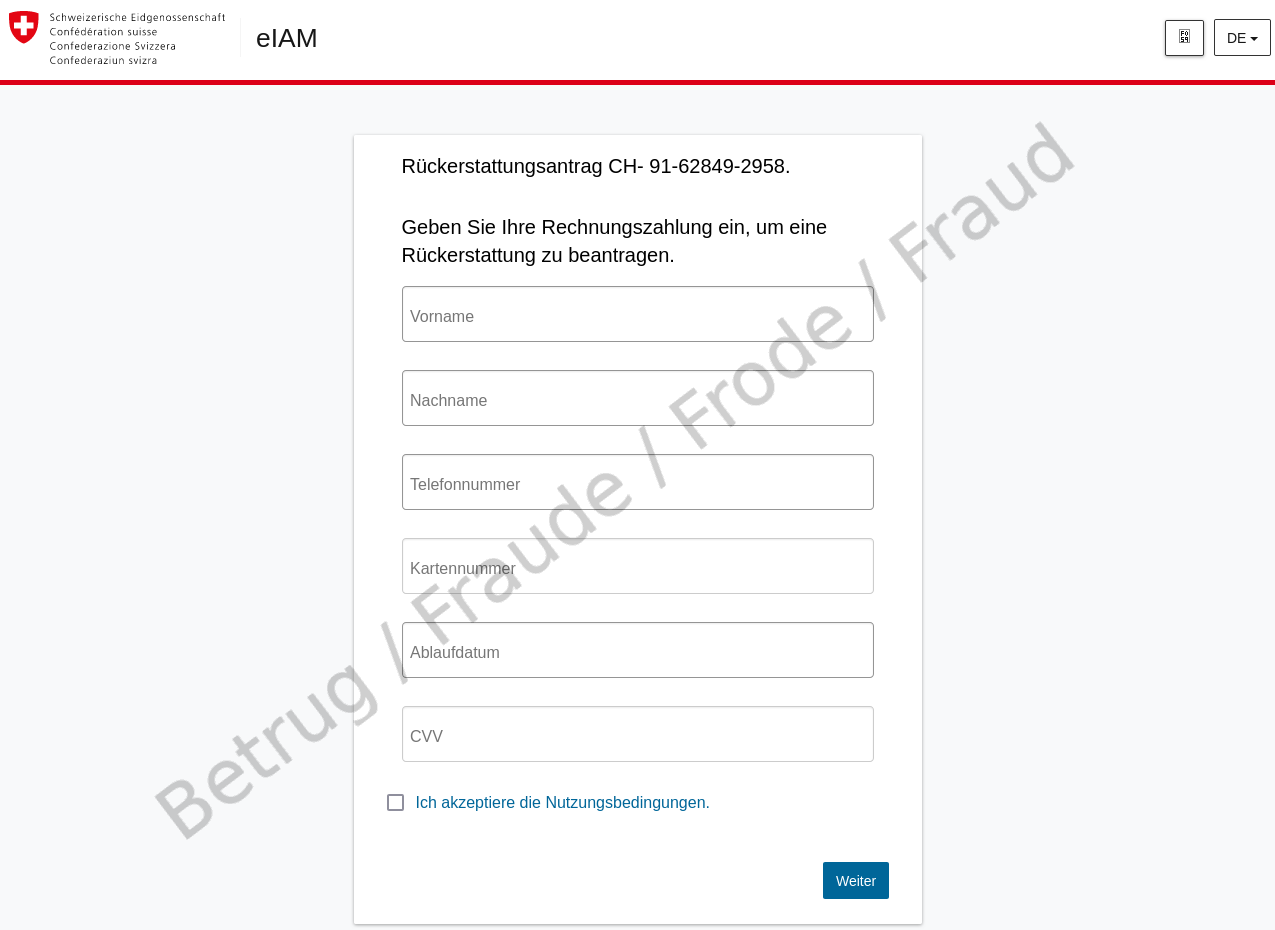
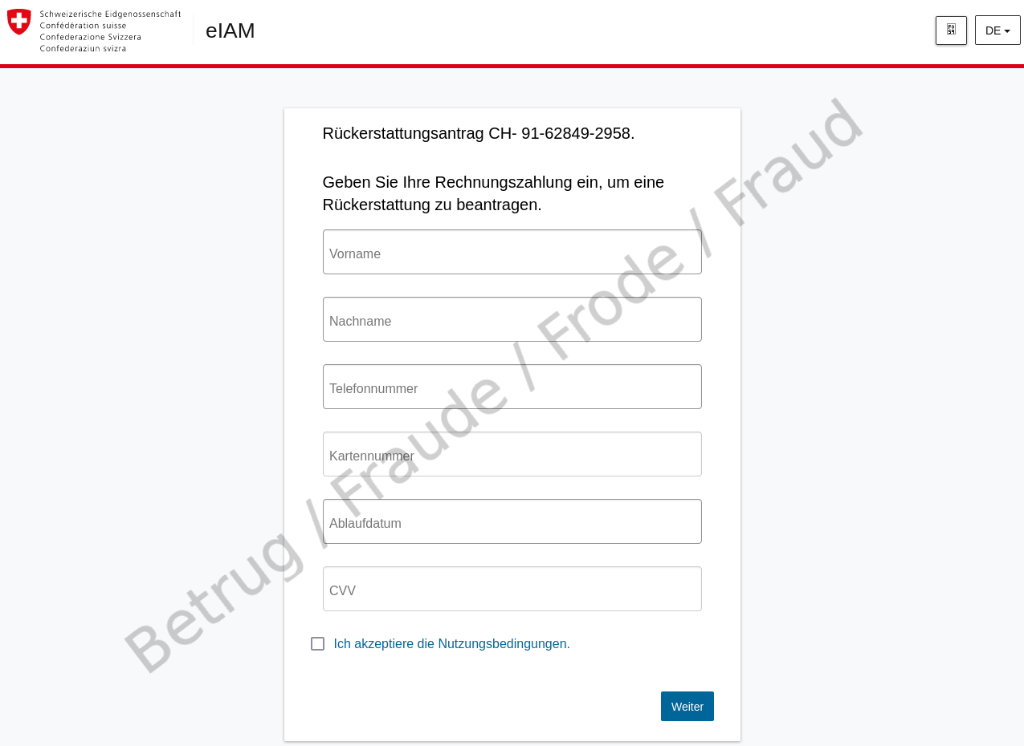
But what happens if you are tempted to click on the link? A page opens that imitates the eIAM service. eIAM is the Federal Administration's central access and authorisation system for web applications.
However, this is only an intermediate step. Once you have entered an email address, a screen for entering credit card details appears. The real eIAM service would require authentication with at least a password.
To continue with the fraudulent process, it is sufficient to enter the credit card number and the CVV code – this shows the fraudsters' intentions.
Further alarm bells should ring for the potential victim at this point at the latest: for a standard refund, a credit card number is of course never requested, but rather an IBAN (account number).
The fraudsters then try to go one step further. To be able to debit the card, they need confirmation from the card owner, which is often sent to the legitimate owner's mobile phone by text message. They immediately ask for this code.
If the victim enters all this data, the attackers can take control of the credit card and make purchases in the victim's name.
Crypto wallet phishing
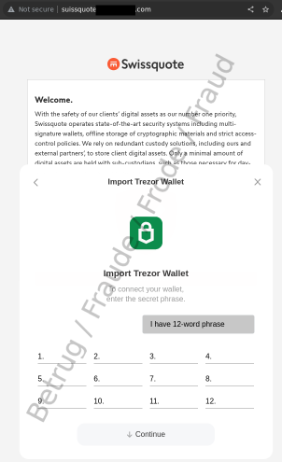
Last week also saw emails in the name of the financial services provider Swissquote doing the rounds. A link was sent with a request to connect crypto wallets to the financial institution, allegedly for security reasons.
A quick look at the URL again reveals that the link does not lead to Swissquote.
Clicking on the "Connect" button opens a menu with a selection of crypto service providers.

Here, the aim of the fraudsters is to gain access to the contents of the user's wallet. For this purpose, the so-called "seed phrase" is requested, also known as the "recovery phrase". This is a sequence of 12 or 24 random words that enables access to the user's wallet if the user's private key is lost. Therefore, this seed phrase should be kept safe and not given to anyone. Fraudsters can use a user's seed phrase to take over the victim's wallet and thus their cryptocurrencies.
Tips on recognising phishing messages
As a general rule: never enter passwords, codes or credit card details on a site that you have opened via a link in an email or text message.
It is usually enough to focus on the typical features of a email to recognise phishing. Paying a little attention will unmask a phishing email in seconds:
- The sender's address: unfortunately, this can be easily faked. In legitimate emails, the email address domain in the sender field must match the contact details, which are usually given at the end of the email.
- The phishing link: the display name can be deceptive. If you move the mouse pointer over the link (without clicking), you can see where the link would actually lead. If it is a domain that is clearly not related to the sender, do not click on the link.
- Language and graphics: inappropriately used or incorrect logos, strange salutations and greetings, possibly a mix of languages and stylistic uncertainties – all of these indicate that the sender's intentions are not legitimate.
Further tips:
- Check the message for the three points mentioned above;
- Never enter passwords, codes or credit card details on a page that you have opened via a link in an email or text message;
- Never forward codes that you have received by text message;
- If someone wants to legitimately transfer money to you, you will be asked for your IBAN, not your credit card number;
- If in doubt, ask the service provider in question directly what the enquiry is about. Do not use a telephone number given in an e-mail or text message, instead look up the correct number online;
- Phishing emails can be reported to the NCSC (https://www.report.ncsc.admin.ch/);
- If you have provided credit card details, contact your credit card service provider immediately so that they can block your card;
- In the event of financial loss, report the matter to the cantonal police.
Current statistics
Last week's reports by category:
Last modification 21.11.2023