07.02.2023 - The number of reports received by the NCSC rose slightly in the fifth week of 2023, with 726 reports. In a phishing case reported last week, the attackers promise to activate a fast 6G network. This phishing attempt is very sophisticated and comprises a number of stages. The attackers even use stolen personal details from the victim's client portal.

Telephone phishing: A drama in four acts
Phishers are thinking up all sorts of new tricks to persuade their victims to hand over access to the payment functions of their phone and their credit card details. A new and very sophisticated method was reported to the NCSC last week.
Act I: Establish trust and obtain information
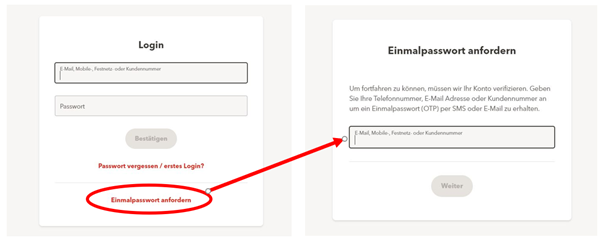
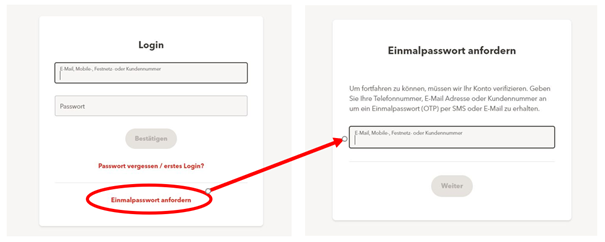
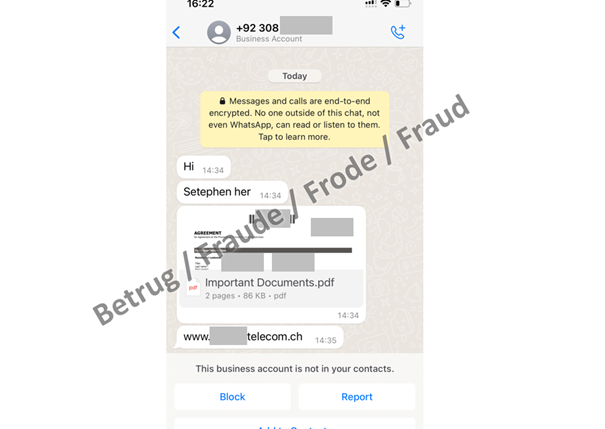
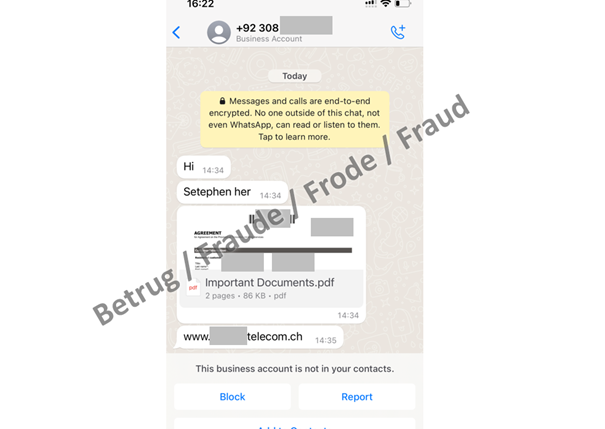
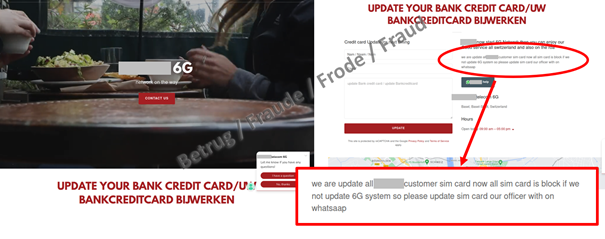
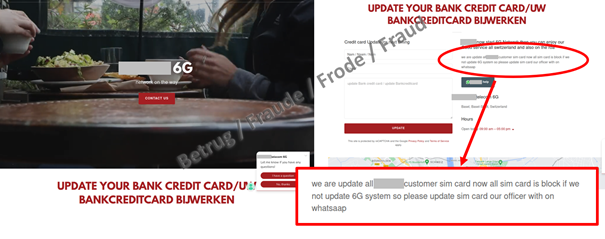
The fraud begins with a WhatsApp call from someone claiming to be from a telecoms provider. The caller claims that the reason for phoning via WhatsApp is because the phone number is currently blocked owing to the activation of the 6G network, and offers to guide the victim through the unblocking process. The victim is promised compensation of CHF 400 for the blockage. During the phone call, the attacker enters the victim's phone number on the telecoms provider's official portal, which causes a one-time code to be issued. The bogus employee now asks the victim to read aloud the code, which has now arrived by text message. The code allows the attackers to log into the telecom provider's portal without needing any further details, and to look at the client documentation, including the contract.
The attackers exploit the fact that, in addition to the login method involving the user name and password, it is also possible to log in using only a one-time code sent to the person's phone. This means that the user name and password are not necessary.
Act II: Using the payment service
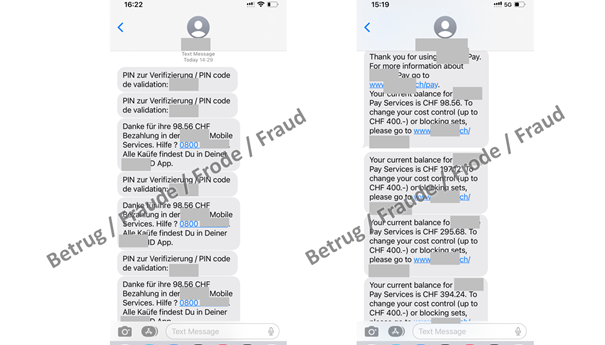
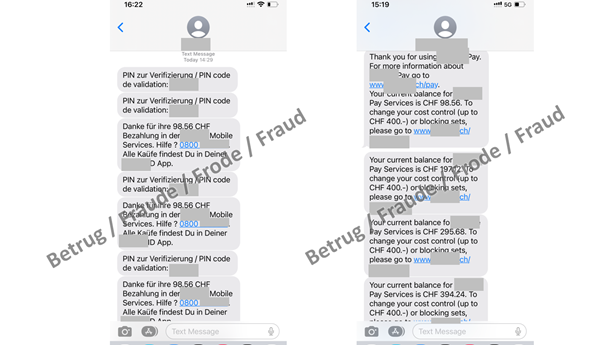
Now that they have access to the client account, the attackers can activate the phone's payment function. This function is used to make purchases from partner companies and pay for them via the phone bill. However, this function also needs to be activated using a one-time code. The limit for such purchases is CHF 400. In order not to exceed this limit, the attackers now make four purchases for EUR 100 each – probably gift vouchers as they are practically untraceable – from one of the registered businesses.
Here too, the attackers manage to persuade the victims to read the codes aloud. They claim that the amounts displayed will be credited to the victim.
Act III: Credit card phishing
Yet the attackers are not satisfied with only gift vouchers. Now they try and phish for credit card details. So someone else calls via WhatsApp, and also claims to be from customer services. To prove that they are genuine, they send the client contract which they obtained in Act I.
The message recipient is now supposed to enter their credit card details on a website that purports to be a page of the telecom provider. However, it is a phishing site.
Act IV: Happy ending
However, the message recipient thought this was a little too suspicious. They went to one of the telecom provider's shops, where the attack was quickly discovered and stopped. The telecoms provider was generous and did not debit the amount from the payment function. The phishing site was also rapidly blocked after the case was reported.
There is still one fly in the ointment: the private details in the contract fell into the hands of the attackers and could be used for further attacks.
Recommendations:
- Never reveal codes or passwords to people over the phone;
- Set cost limits for payment functions that are as low as possible, or deactivate these functions. The telecoms providers can also permanently block these services;
- If you are unsure, terminate the call and phone back using the provider's official number. You can find the phone number on the official website of the provider concerned;
- Never allow yourself to be put under pressure on the phone;
- Email sender IDs and phone numbers can easily be spoofed.
Current statistics
Last week's reports by category:
Last modification 07.02.2023