27.12.2023 - The NCSC receives numerous reports concerning fraudulent web content, various phishing schemes and dubious advertising websites every day. However, when it checks the reported websites, perfectly normal, innocuous-looking websites are sometimes displayed. In these cases, it is worth persevering rather than believing that those who submitted the reports made a mistake or that the website has already been taken down by the provider. In many cases, closer analysis reveals that fraudsters use various techniques to avoid detection by security authorities for as long as possible.

The IP address check
Fraud or phishing attempts are often tailored to a specific country. Phishing emails supposedly sent by Swiss financial institutions, for example, are aimed exclusively at Swiss internet users. The attackers restrict access, for instance, so that the fraudulent website is displayed only if it is accessed from a Swiss IP address. In the case of access from non-Swiss IP addresses, an innocuous website is displayed or the user is redirected to a search engine, for example. Similarly, the hosting provider on whose server the fraudulent website is stored is usually located abroad and only sees the benign website, as the provider's access is from a country-specific IP address outside Switzerland. In the worst-case scenario, the provider does not take any countermeasures. Furthermore, analysts often use VPN connections rather than their actual IP address. This can also be detected by websites and the analyst is then shown a harmless-looking website.
The referrer check
Some fraudulent websites also check the so-called referrer, which is provided each time a website is accessed. The referrer contains information about the preceding website from which the user arrived at the current page. However, if a website is accessed directly by entering the URL in the browser's address bar, no such referrer is provided. The web server then knows that the access was direct, not via a link. Some websites behave innocently when accessed directly, for example. However, the dubious content is displayed when the same website is accessed via a search engine, a link in a fraudulent advertisement or via social media.
The browser check
Nowadays, especially in the private sphere, most websites are accessed on a smartphone. Fraudsters take advantage of this by displaying the fraudulent page only on smartphones. When a website is accessed, the user agent is also transmitted. This contains information on the user's operating system and browser type, and the server can detect whether an Android device or an iPhone was used, for example, or whether the website was accessed from a notebook or PC. While most potential victims arrive at the website via a smartphone, an office device is usually used for analysis purposes.
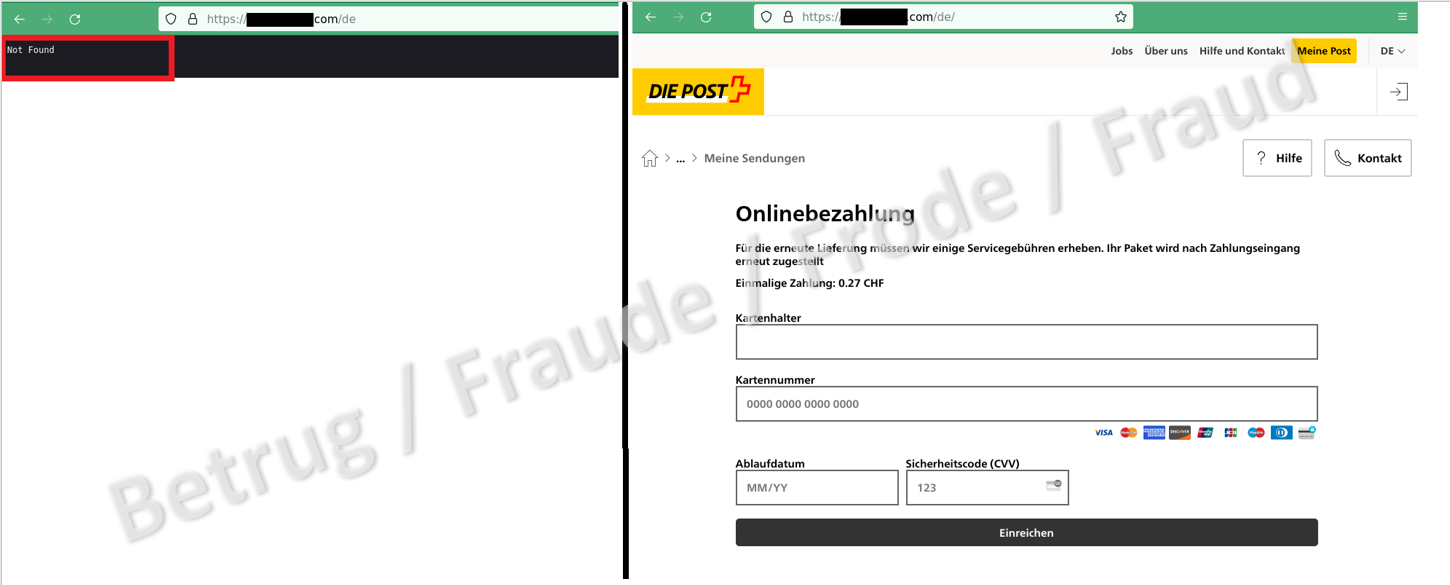
Analysis nevertheless possible
The aim of these technical precautions taken by the fraudsters is to ensure that the websites go undetected for as long as possible and are not recognised as malicious and taken down even if they are reported to the relevant authorities. The good news is that these attempts by fraudsters to outsmart analyses can easily be thwarted. The data transmitted concerning the operating system, referrer and browser type can be manipulated using suitable tools. It sometimes takes several attempts with different settings before success is achieved. And of course, there are also ways of selecting IP addresses according to what is needed. In this way, the attackers' attempts miss the mark and, even in these cases, the fraudulent websites are quickly analysed, verified and deactivated if possible so that Swiss inhabitants enjoy maximum protection.
Nevertheless, it is important to follow a few simple rules to avoid clicking on a fraudulent link in the first place:
- Beware of emails that require action on your part or put you under time pressure.
- Be careful if you are urged to perform an action. This may involve clicking on a link or opening an attachment, for example. Never enter personal data in a form that you opened via a link in an email.
- Be wary:
Fraudsters are constantly devising new scenarios to encourage victims to react rashly. This method is known as social engineering. It is intended to ensure that the victims carry out the actions controlled by the perpetrators without being aware of it. So don't let yourself be taken off guard; instead, think about the situation calmly and, if in doubt, ask friends, work colleagues or the NCSC how to assess the matter.
Current statistics
Last week's reports by category:
Last modification 27.12.2023





