28.02.2023 - The number of reports received by the NCSC rose again in the eighth week of 2023. Phishing messages in both email and text message form are among the cyberphenomena most frequently reported to the NCSC. In most cases, they are simple standard phishing attempts. However, last week saw a few very sophisticated and original variants being reported. This included apparent voice messages, password-protected phishing PDFs and phishing websites disguised as special offers on belated motorway tax sticker purchases.

Personalised phishing domain in an apparent voice message
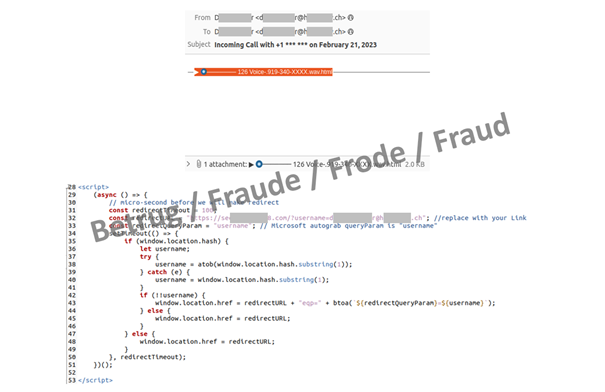
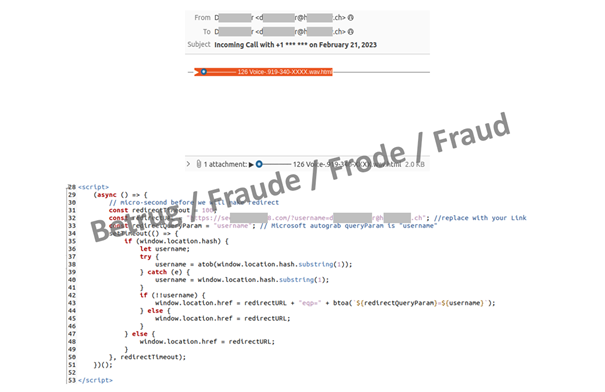
Cybercriminals are constantly thinking up new cover stories to conceal their criminal intentions. The recipient of one phishing email reported it this week, because he was worried he might end up on a blacklist. A detailed analysis by the NCSC revealed the following background: The phishers had manipulated the sender address in the email so that it appeared to come from the recipient himself. Many people do not know how easy it is to fake the sender address, so this phishing email naturally caused the reporting person to worry that he might be reported as a phisher and end up on a blacklist.
However, the faked sender was not the only personalisation in this case. The HTML document in the email, which was disguised as a voice message, contained a phishing link tailored to the recipient. In order to listen to the voice message, the recipient was told to click on the link and then enter his email credentials on the subsequently opened page. His email address had already been completed in the login field.
Phishing link in a password-protected PDF
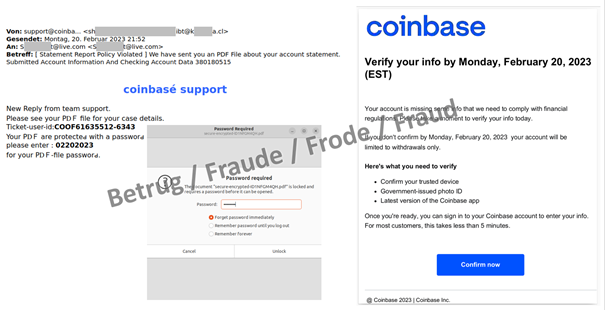
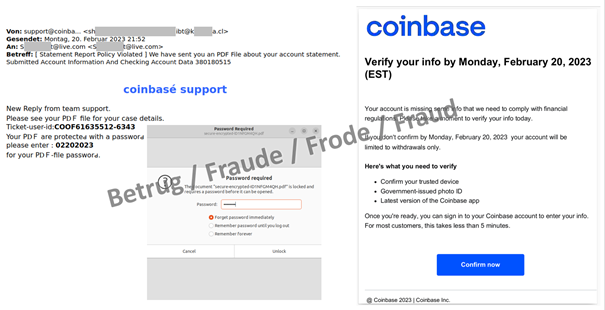
Another new variant was an email purporting to come from the support team of the Coinbase cryptocurrency exchange platform and containing a password-protected PDF. The email itself contains the password needed to open the PDF. The PDF, in turn, contains a link to a phishing platform which steals the Coinbase login data.
Sending a password-protected document together with the password is about as secure as leaving the key in the door of a safe.
The encryption in this case is designed solely to circumvent an automatic analysis of the PDF by anti-virus software or other security programs. It is also a reliable indication of malware or phishing.
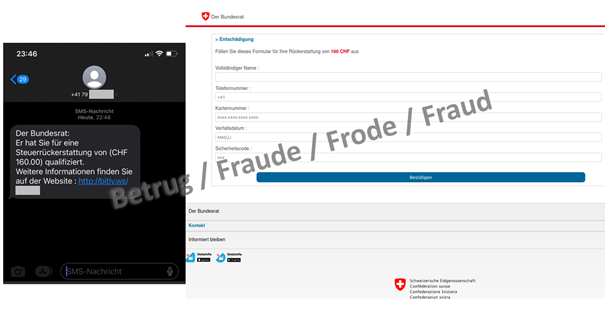
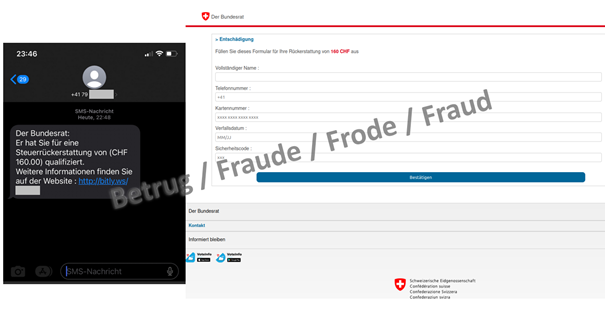
Apparent text message from the Federal Council leads to a disguised phishing page
It is nothing new for the Federal Council to address a message directly to the Swiss population. However, this has never yet taken the form of a text message. The NCSC has now received a report of a text message purporting to be from the Federal Council, in which a tax refund of CHF 160 is promised. Anybody following the phishing link ends up on a website with the Federal Administration logo, which asks people to enter their credit card details in order to receive the apparent tax refund. This website is wearing a cunning disguise: anyone clicking on the link usually ends up on the phishing website. However, if an automatic analysis is run – like the ones performed by the NCSC – the website tries to detect this and show a harmless Arabic news site instead of the phishing website. This mechanism is intended to prevent automatic analysis by security researchers.
Phishing webshop apparently from Swiss Post
An old friend among phishing techniques is apparently aimed at stragglers who have yet to buy a motorway tax sticker, and offers them a "fantastic" special offer on the stickers. A new aspect is the fact that the phishing link appears to lead to a Swiss Post webshop.
The website is so badly designed that none of the links work and the number of ordered stickers cannot be changed. However, one can imagine that the phished credit card details would end up with the phishers in any case.
Recommendations:
- Wherever possible, use two-factor authentication. This offers an additional layer of protection to prevent your account from being hacked.
- No bank or credit card company will ever send you an email requesting that you change your password or verify your credit card details.
- Never divulge personal data such as passwords or credit card details on a website that you have accessed by clicking on a link in an email or text message.
- Bear in mind that email sender IDs can easily be spoofed.
- Be sceptical if you receive emails that require action from you and otherwise threaten with consequences (loss of money, criminal charges or legal proceedings, account or card blocking, missed opportunity, misfortune).
Current statistics
Last week's reports by category:
Last modification 28.02.2023