27.02.2024 - Classified ad fraud is one of the offences most frequently reported to the police. The fact that new variants continually arise shows that this is a lucrative business for scammers. Three new types of social engineering attacks reported to the NCSC in recent weeks are designed to trick users of the TWINT payment app.

TWINT account takeover (ATO)
Scammers are not just targeting buyers in classified ad fraud. Sellers are also being targeted, as an example reported last week to the NCSC shows. The victim had offered a games console for sale on a Swiss classified ads platform. It wasn't long before someone was interested in the offer and wanted to buy the device. The buyer wanted to pay via TWINT and asked for the seller's telephone number. A few minutes later, the seller received a text message supposedly confirming that the payment had been successful. However, in order to confirm receipt and effectively receive the money, the seller had to click on a link which then led to a page that seemingly belonged to the classified ads portal with a supposed TWINT chat. The chat confirmed that the amount had been transferred, but pointed out that there had been an increase in fraud attempts recently and that payment could therefore only be released if some security questions were answered beforehand.
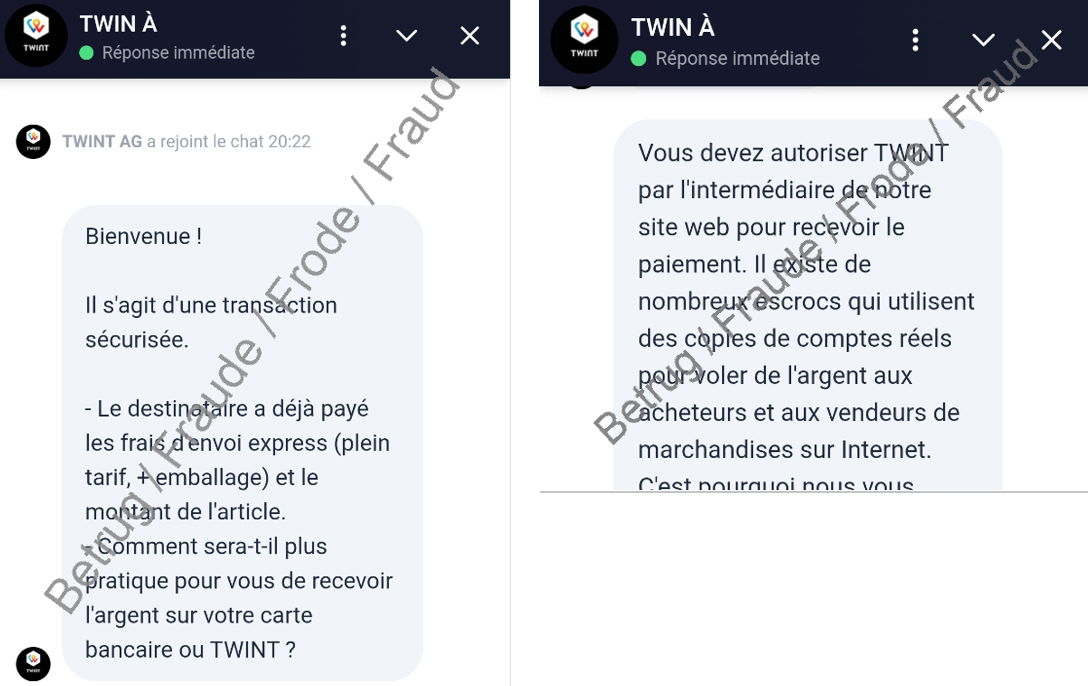
This ‘security process’ required the seller to enter their name, date of birth, TWINT PIN, debit card number and the last five digits of their IBAN number. The seller then received an additional SMS code, which had to be entered on the chat page for confirmation. Once the seller had provided all this information, they received, instead of the money, a message that a new telephone number had been added to their TWINT account. The first direct debits from the seller’s account then followed.
The seller had unwittingly sent the scammers their login details and security codes, which the scammers then used to log on to the app using a new device and make payments from the seller’s account.
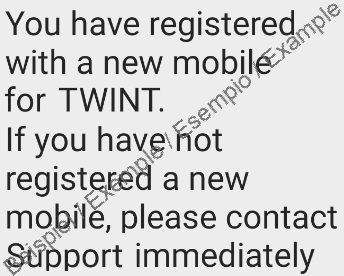
The scammers are likely to have fraudulently used a function that allows a person’s existing TWINT account to be linked to a new device and even a new telephone number if the device is changed or lost. In addition to entering personal data and the TWINT PIN after downloading the app, TWINT’s security standards also require a two-step authorisation process via SMS if the device or telephone number is changed. In the case reported to the NCSC, the security questions were identical to the information that the scammers had requested. The NCSC therefore assumes that the scammers exploited a method called the ‘re-boarding process’ in order to trick the seller into disclosing personal login and security data.
Variant involving a supposed refund
In many cases of classified ad fraud, the scammers demand advance payment from the buyer for items that they then fail to deliver. But sometimes the scammers also try to get more out of their victims. In one recent case, for example, the scammer was not satisfied just with the advance payment. The scammer contacted their victim again shortly afterwards, reporting a mishap in the post: the parcel had allegedly been damaged on dispatch. The scammer said they would of course pay for the damage and refund the buyer’s money via TWINT. But instead of a refund, the scammer sent a claim for money. If the victim is not careful and clicks on ‘accept’, they get scammed twice. The receipt of money does not need to be actively confirmed in the TWINT app.
Other variants involving a supposed refund
In a similar case, the scammer had contacted the buyer again, claiming that another interested party had offered to pay more for the item on sale. The scammer told the buyer that they would refund the money the buyer had already paid, including expenses. To get the refund, the buyer had to scan a QR code using the TWINT app. However, the QR code had nothing to do with a refund: on the contrary, it triggered a payment to a shop, a tactic scammers often use to obtain vouchers.
Precautions you should take
- Never forward codes that you have received via SMS, email or telephone;
- Do not enter any personal data on forms that you have opened via a link in an email or text message;
- Take care when interacting with people you don’t know on online platforms;
- Always be careful when making a payment and check the [recipient’s] details before you make the payment;
- Set limits on all payment methods according to your budget and the security of the payment method. This applies in particular to online (via the internet) or contactless payment methods;
- Never use QR codes that someone sends you from an unreliable source;
- If you suspect that the seller/buyer has fraudulent intentions, stop communication with them immediately and ignore any future messages or emails;
- Inform the classified ads platform and your bank’s customer support about the incident: they can block corresponding offers, buyers and sellers.
Further information and security tips are available on the official TWINT website at
Current statistics
Last week's reports by category:
Last modification 27.02.2024





