15.04.2025 - Social networks such as Facebook, Instagram, X and Snapchat are particularly attractive to cybercriminals because of their high level of user engagement. By stealing login credentials and gaining access to a social media account, scammers can share content and view private information. This opens up a range of malicious possibilities: they can post scam ads, spread false information about people or companies, or even blackmail victims. And by pretending to be the person whose credentials they have stolen, they can target that person’s friends and exploit them too. This can start a chain reaction where many people fall for the scam.

In recent weeks, we have received reports of scammers exploiting social media accounts, moving from one to the next. They start by stealing a victim’s login credentials, then use that account to send scam emails to the victim’s contacts – who are more likely to trust messages from someone they know. If the recipients fall for the scam, the cybercriminals gain access to their login information as well. To maximise their success, scammers often try to steal credentials for multiple accounts at once. This strategy lets them compromise a large number of accounts quickly, increasing their chances of accessing valuable information. The more of a victim’s accounts that are compromised, the greater the potential loss to them.
A fake contest
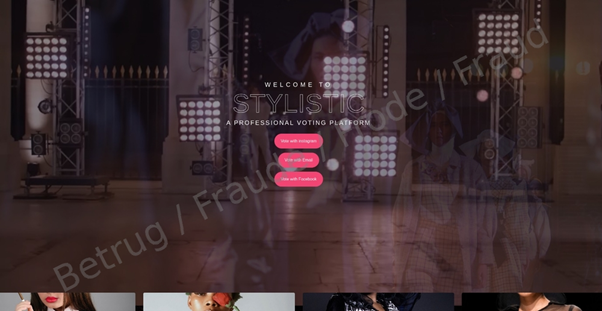
In a recent scam, victims received messages on social media from scammers posing as people they knew. The scammers claimed to be taking part in a fashion or style contest and asked their friends to vote for them. Believing the request was coming from a friend, the victims clicked the provided link without hesitation. That link led to a fake website designed to look like a legitimate voting platform for a fashion contest.
On the scam website, you’ll see the names of people who have already received votes or are leading in the competition, framed by a sleek, fashion-themed layout. To cast your vote, you’re asked to log in using your Instagram, Facebook, or email account. We found that the images of the candidates come from stock image databases – a clear sign that the website is a scam. The entire site was created for the sole purpose of stealing people’s passwords.
A sneaky trick
The scammers have a particularly sneaky trick: when you try to log in, no matter what password you enter, you’ll always get a message saying it’s incorrect. The likely reason for this is that they’re trying to steal your login details for as many platforms as possible. For example, if your Instagram login fails, you might try Facebook, since you really want to help your friend by voting for them. When that doesn’t work either, you try your email. By the end, the criminals have access to two of your social media accounts and your email – all in one go. And once they have access to your email, they can use the password recovery feature to break into other services and accounts linked to that email.
And it starts all over again
Now that they have all this information, the scammers move on to your friends, using the same approach, and the cycle starts all over again. Regular readers of our weekly reviews will recognise this as chain phishing. This type of scam is most commonly aimed at Microsoft 365 accounts in businesses, but it’s also increasingly used on social media in the private sector. That’s why it’s important to stay vigilant, even in your personal interactions online.
Recommendations
- Never enter personal information such as passwords or credit card details on a website that you accessed through a link in an email or text message.
- Before you log in, always double-check that you are on the correct website.
- If you're not sure that a message is really from who it says it is, contact them to check.
- If you've entered your password on a scam website, change it immediately on all services where you use it. Use a separate, strong password for each service.
- Enable two-factor authentication wherever possible. This will greatly enhance the security of your data.
Current statistics
Last week's reports by category:
Last modification 15.04.2025