03.06.2025 - Phishing has been one of the most frequently reported scams for years. Until now, attackers have relied on quantity rather than quality, sending out bulk emails – most of them obviously dubious – in the hope that a small percentage of recipients will respond. However, the NCSC has observed a growing trend in targeted attacks that are fewer in number, but more sophisticated and therefore more likely to succeed. Last week, the NCSC was notified of a two-step attack that demonstrates how sophisticated phishing scams are becoming.

Last week, a case was reported to the NCSC involving a two-stage phishing attack, which demonstrates the growing sophistication of these attacks. The new scam began innocently enough with an email that appeared to come from the victim’s bank. The email claimed that the victim’s personal data had to be updated as part of the bank’s compliance policy and in order to ensure the accuracy of its customer data.

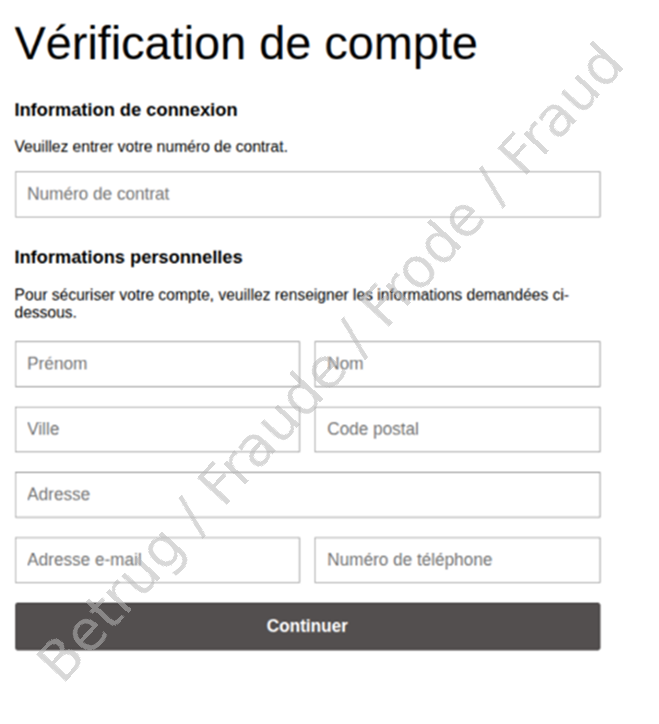
After clicking on the link, a website opened that looked deceptively similar to the website of the victim’s bank. There, the victim was asked to enter personal details, such as their e-banking contract number, name and telephone number. Many people would probably enter this information without much hesitation, as the data requested doesn’t appear particularly sensitive at first glance: for example, the victim was not asked to enter any credit card details or passwords. Once the victim had entered the information, they were redirected to what looked like their bank’s website.
This was not a classic phishing attack: the scammers didn’t ask for sensitive personal data such as credit card details or passwords. That is what made the scam so deceptive. Even the NCSC only warns you to exercise particular caution when entering sensitive data.
The phone call
However, the data collected by the fraudsters was just the first step in the scam. The second step took place a few days later when the scammers contacted their victim again, this time by telephone, pretending to be a representative of the bank. The telephone number of the relevant bank came up on the victim’s display.
The caller addressed the victim by name and wove personal details such as the victim’s home address or banking card information into the conversation, which lasted several minutes. The caller’s aim was to lure the victim into a false sense of security by referring to the personal information that the victim had already given them. Once the caller had gained the victim’s trust, they revealed the real reason for the call: a supposedly fraudulent transfer had been made from the victim’s account to a hotel in Milan and must now be blocked. To stop the transaction, the victim was asked to scan a QR code with their e-banking app.
What the victim didn’t realise was that by scanning the QR code they were giving the scammers access to their e-banking account. This allowed the scammers to use the victim’s multi-factor authentication feature.
Targeted phishing attacks – a new trend
While classic phishing attacks are usually based on mass phishing campaigns, the NCSC is observing an increase in targeted attacks. These are more complex, but appear to offer the scammers a higher chance of success.
A typical example of this trend is the classified ad phishing attack. In this scam, fraudsters pose as prospective buyers on classified ad sites and tell the seller they want to pay for the purchased item via a secure payment service. Victims are lured to deceptively genuine-looking websites, where they are deceived into entering personal data. In these cases, too, the scammer first builds up the victim’s trust by means of a specific situation, e.g. a sale on a classified ad platform. This scamming method is widespread and uses a simple but effective principle: the victim is less suspicious in a specific situation or when the scammer already has a lot of their personal information.
Recommendations
- Be wary if asked to provide personal information, even seemingly harmless information; it could be the first step in a phishing scam. If you give someone your personal data, it could be used in a targeted phishing attack against you.
- Only scan QR codes with your e-banking app if you are absolutely sure that you are on the genuine website of your bank. Never disclose transaction authentication numbers (TANs) or passwords over the phone or by email: no reputable institution or provider would ever ask you to do so.
- Don’t share personal or sensitive data with someone you don’t know over the phone.
Current statistics
Last week's reports by category:
Last modification 03.06.2025





