20.04.2021 - Last week, the NCSC recorded fewer reports than usual. Most reports concerned classified ad and investment fraud. A new approach attracted attention, in which companies are made aware of alleged "trivial" security vulnerabilities or missing security settings. The perpetrators speculated on unsettling the recipients and thus persuading them to pay a sum of money. Also of note are attempted scams involving phone-paid services, in which fraudulent amounts are charged directly to mobile phone bills.
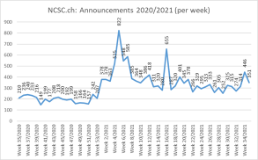
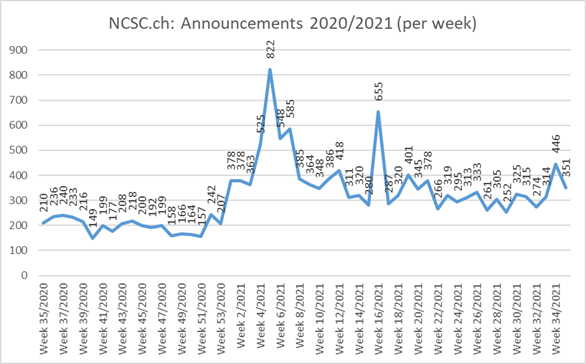
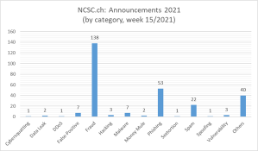
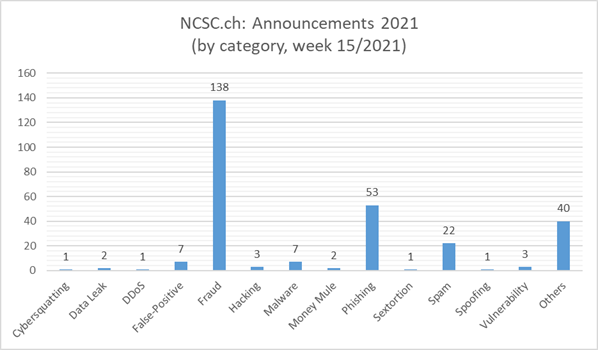
Current statistics
A fatal competition
"You have won and need to submit a code for verification". In this case, what sounded promising at first glance had in fact a criminal motive. The scam began when a small grocery shop's Facebook account was hijacked and a supposed competition was posted. Anyone who took part in the competition and entered their phone number as requested immediately received confirmation that they had won. All they had to do was enter a text message code.
In the meantime, the fraudsters made an online purchase and entered the victim's mobile phone number. Many people do not know that "direct carrier billing" allows online purchases in app stores to be charged directly to the user's mobile phone bill. However, after the phone number has been entered, these purchases have to be confirmed with a text message code. This is sent to the phone number entered, i.e. to the victim. In order to initiate and confirm the purchase, the fraudsters need the text message code. Using some pretext – in the current case it was the competition – the fraudsters therefore try to get the victim to forward this code to them. If the victim forwards the code, the attackers can confirm the payment and the amount is debited or charged to the mobile phone bill.
Reports of unexplained charges on mobile phone bills have increased in recent weeks. In practically all cases, direct carrier billing had been misused. Do not forward any codes you receive by text message under any circumstances!
"You have a security vulnerability"
There are now numerous so-called "bug bounty" programmes, in which researchers who uncover security vulnerabilities in an ethical manner are rewarded appropriately. These schemes set rules that both researchers and victims must follow when discovering and reporting a vulnerability. Last week, we received correspondence alerting a company that it had a security vulnerability. Specifically, the lack of DMARC (Domain-based Message Authentication, Reporting and Conformance) was highlighted. DMARC is a specification that was developed to reduce email misuse. The aforementioned correspondence did not ask for any money, but explained that the researcher would be in touch a few more times if the security vulnerability was not remedied.
However, you do not have to be a specialist to recognise a lack of DMARC; this can be ascertained by the simplest of means. Similarly, the absence of DMARC cannot be referred to as a vulnerability, but simply a missing additional security element. Those who send such correspondence gamble on making the recipients feel insecure and then persuading them to make a payment. It can also be assumed that once a reply is received, other "trivial vulnerabilities" will also be reported and an attempt will then be made to actually obtain money from the victim.
If you receive reports of security vulnerabilities, check them carefully and act prudently. Never allow yourself to be put under pressure.
Last modification 20.04.2021