17.08.2021 - The NCSC received few reports last week. Fraudsters used a fake Google ad to try to lure bank customers to a bogus site. In another case, considerable effort was made to hack a Facebook account. In addition, an increasing number of attempted attacks on Synology network storage devices were reported in Switzerland and around the world. Users are strongly advised to use strong passwords

Considerable effort to hack a Facebook account
Fraudsters usually use phishing to obtain access credentials for Facebook accounts. Using more or less credible stories, the victims are tricked into revealing their passwords.
A case reported to the NCSC last week shows that attackers sometimes go to greater lengths. Here, the attackers tried to gain access to a recovery email address that the owner had set up on Facebook. Account owners who forget their passwords can have a temporary password sent to these predefined email addresses. Facebook allows other email addresses to be registered in addition to the primary email address. The recovery code can also be sent to these email addresses.
This is unproblematic provided the owner of the Facebook account has control over all recovery email addresses. In this case, however, one of these addresses was an old business address. The business no longer existed and the domain under which the business was previously accessible had not been renewed. Resourceful attackers exploited the situation and registered this domain. As soon as the attackers had control over this domain, they could intercept and read all emails sent to any email addresses belonging to this domain, including the "old" ones. Using this method, the attackers could also gain access to the recovery address of the Facebook account, intercept the verification code and take over the Facebook account.
- Email addresses have become the lynchpin of access to social media accounts, webshops and other online services. However, this also means that the loss of an email address has serious consequences. Protect your email account accordingly and use two-factor authentication whenever possible.
- If a domain is abandoned and no longer used, always be aware that the new owner will have the ability to intercept and read emails for all addresses going to that domain.
Google ad leads to fraudulent site
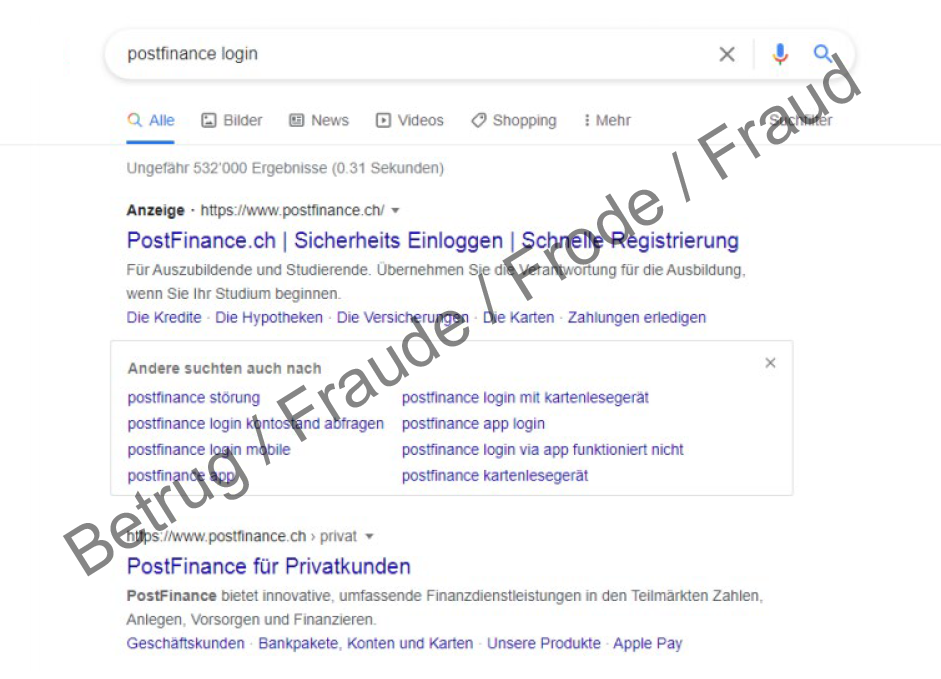
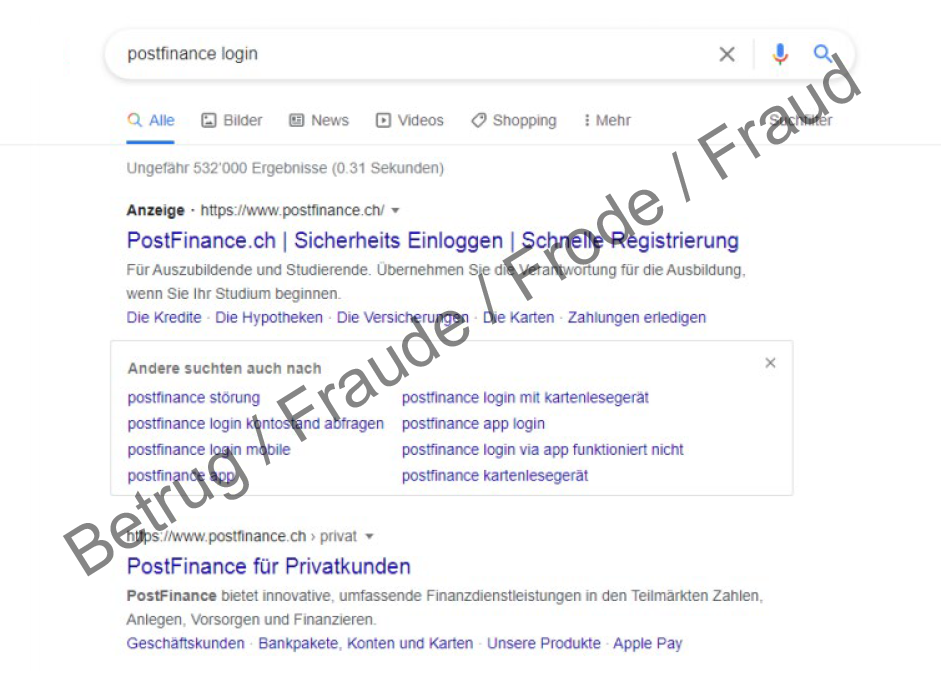
Fraudulent Google ads were again an issue at the NCSC last week. During a Google search for the financial service provider PostFinance, some people were shown an ad that at first glance looked as if it came from PostFinance. However, clicking on it opened the page "poosttfinance.xyz", which had been registered by fraudsters.
An error message then suddenly appeared asking the user to call a Swiss telephone number. However, it was fraudsters who answered calls to this telephone number, not PostFinance employees. The exact nature of the calls has not yet been fully clarified. It is conceivable, for example, that it was a case of voice phishing, in which the victim was asked to enter a login name and password. The victim is then told the code to enter into the yellow card reader, which calculates the second authentication factor. If this code is also passed on to the fraudsters, they have full access to the e-banking account and can make transfers. The website has now been deactivated.
- In the case of many Google searches, advertisements are first displayed before the actual hits. These hits are marked accordingly as "ads" and the originators pay to have them listed as the first hits. As the above case shows, Google ads can be misused.
- Therefore, be vigilant when conducting a Google search, especially in the case of ads.
- No company will ever ask you to provide your password via email, SMS, telephone or social media. Such attempts are always fraudulent.
Increased reports of hacked Synology NAS devices
The NCSC received a number of reports of attempted attacks on Synology NAS devices last week. Network-attached storage (NAS) is the term used to describe easy-to-manage file servers that can be connected to a network with little effort. According to a warning from Synology, an increase in so-called brute-force attacks has been observed in recent days. In this type of attack, attempts are made by going through a list of passwords in order to eventually gain access to the server. The attacks are said to be perpetrated primarily by the "StealthWorker" malware family.
If an attack is successful, there is a risk that the attackers will install ransomware, for example, and thus encrypt the entire network storage system. Synology strongly recommends that all system administrators check their systems for weak passwords, enable auto-blocking and account protection, and set up multi-level authentication if necessary.
Moreover, always keep your devices up to date and install all available updates. In general, network storage should be directly accessible from the internet only if absolutely necessary.
More information can be found on the Synology website:
https://www.synology.com/en-global/company/news/article/BruteForce/Synology
https://kb.synology.com/DSM/tutorial/Synology_NAS
https://blog.synology.com/10-security-tips-to-keep-your-data-safe
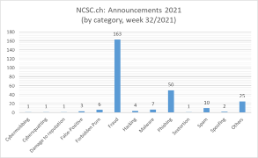
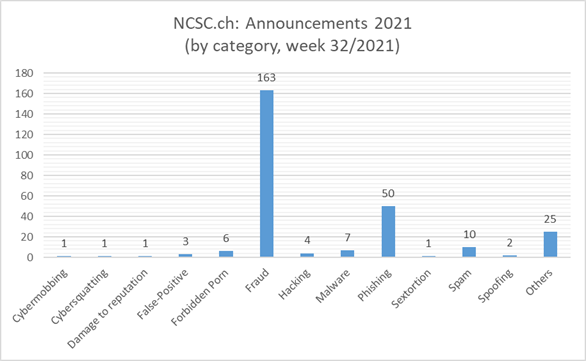
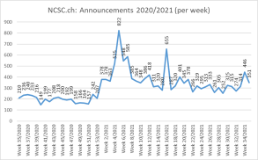
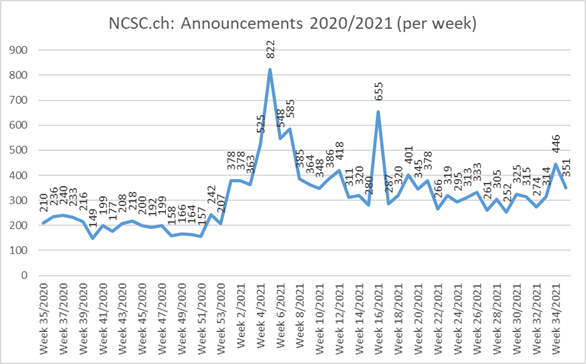
Current statistics
Last modification 17.08.2021