07.09.2021 - The NCSC registered an average number of reports last week. It dealt with reports about the resurrection of websites that were thought to have been deleted. There were also renewed reports of a familiar blackmail technique involving deleted databases.
Resurrected websites advertise for online casinos
Last week, the NCSC received two reports on similar incidents. Both cases related to domain names, i.e. internet addresses and the associated websites, which the original owner had closed down and deleted but which had then suddenly come back to life with the original content and domain. The only discernible difference was that the resurrected websites were now advertising, more or less subtly, for online casinos which are forbidden in Switzerland.
This phenomenon is already well-known to the NCSC from previous cases. Often, the misappropriated websites have a small following, but one that is nonetheless interesting for the attackers. They exploit the ranking that the original websites have acquired in search engines. If a relevant search term is entered, the attackers' newly resurrected website is displayed together with its content in the usual place, rather than the original site. For the attackers, websites that display as the first result for a specific search term are most lucrative. The attackers obtain the website's old content from web archiving services, which save earlier website versions and make them accessible – as we know, the internet never forgets. Both corporate and private websites are targeted, but those of clubs and local authorities, for example if they are no longer needed following a merger, are also popular targets.
In addition to the observed advertising for online casinos, the defunct domains are often also used to set up fraudulent webshops. Thus, it seems to be worthwhile for an attacker to pay the small fee to register a defunct website and then reactivate the site for their own aims, in order to obtain the corresponding search ranking.
- Be aware that a defunct domain (the website's registered name) can be reserved and potentially used fraudulently by other people.
- If you want to close down a domain, check to see whether it has achieved a certain ranking in search engines. If you keep the domain for a while but do not put any content on it, it will automatically lose its ranking and become unattractive.
Online database deleted
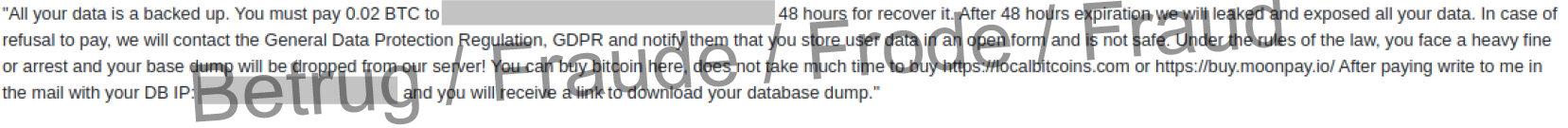
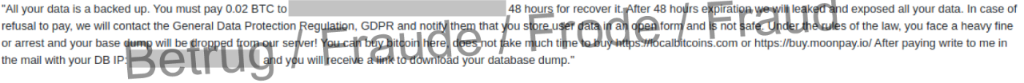
Last week, the NCSC received a report of an attack on a database that is accessible from the internet and which had been deleted by fraudsters. In its place, a ransom demand was posted, together with a threat to report the incident to the data protection authorities, if 0.02 bitcoin were not paid. It was claimed that personal data had been found in the databases and that it had been made publicly accessible, in contravention of the Data Protection Act. Prosecution was threatened. However, the available log data shows that the database was neither copied nor read, but simply deleted. So this is probably a bluff.
This tactic has been used by attackers since 2016, mainly against MongoDB installations that are accessible from the internet. Last year, over 23,000 such incidents were reported worldwide.
- Check whether it is necessary for your database to be accessible from the internet.
- Use a firewall to protect the database and leave only the absolutely essential network ports open. Restrict services to the absolute minimum.
- Set up strong authentication, for instance by using a second factor.
- Never pay a ransom to a blackmailer.
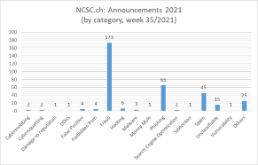
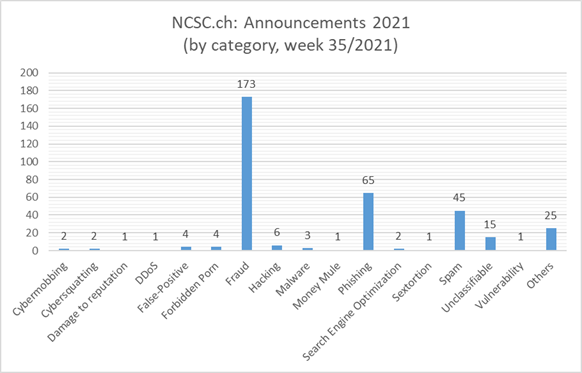
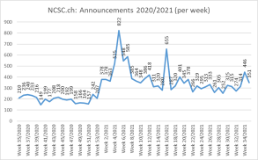
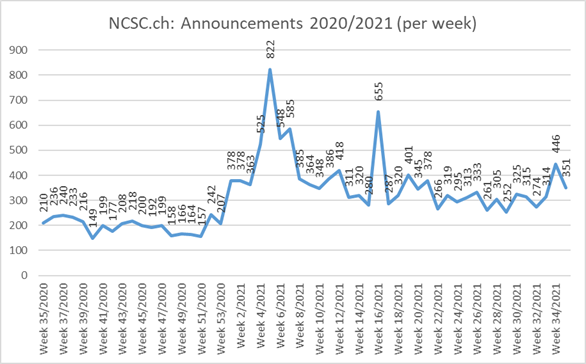
Current statistics
Last modification 07.09.2021