20.01.2022 - The use of emails with malicious Microsoft Office documents to spread malware is on the rise again. Once a computer has been infected, fraudsters have undetected access to the entire network. Help fight such cyberattacks and report suspicious emails to the NCSC at antiphishing.ch.

The quiet new year period is definitively over in cyberspace as well: since 10 January 2022, the NCSC has again recorded a huge increase in reports of malicious Microsoft Office documents being sent via email to numerous recipients in Switzerland. In some cases, emails previously sent by the recipients are reused. This is done in order to gain the trust of the recipients and to persuade them to act without due caution (social engineering). If this proves successful, the victim opens the attachment in the email and the malware can infiltrate the computer unnoticed. Cybercriminals are not only targeting private users; companies are a particularly lucrative target for such attacks. Once a company network has been infiltrated, the acquired access to this network can be resold on the dark web for significant amounts of money. Organised hacker gangs buy such access in order to encrypt data of the affected companies using an encryption Trojan (ransomware), for example. High ransoms are usually demanded for decryption.
How malware is infiltrated into a network
In order to spread malware and penetrate corporate networks, many attackers use Word and Excel attachments in particular. Since people frequently work with such documents, receiving an email with these Office documents attached is nothing unusual and the recipients do not suspect anything sinister. However, many people do not know that Office documents pose a great danger. By means of macros – specific program code that can be easily embedded in a document – malware can be spread by email and the code can be executed. If victims allow macro program code to be executed, the device is infected with malware without their knowledge. The fraudsters thus gain undetected access to the infected computer and can move laterally in the company's network, e.g. to infect further computers or the entire network.
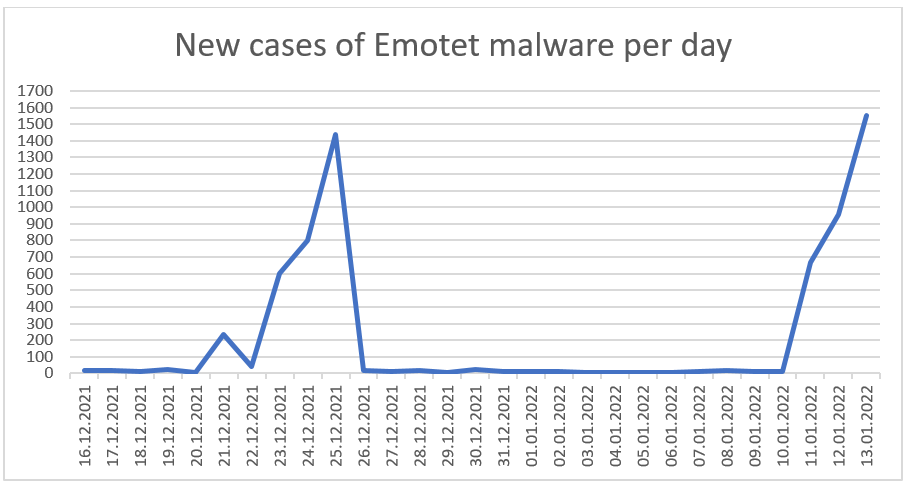
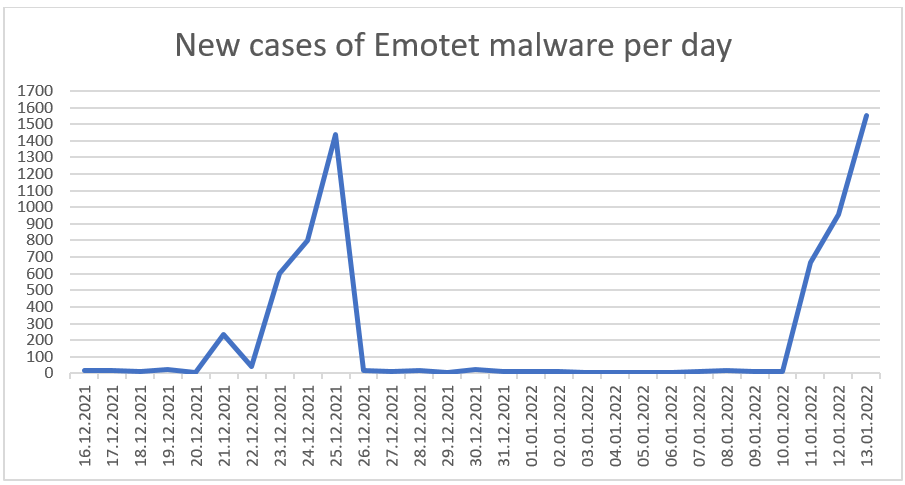
Office documents are therefore the gateway for a large number of dangerous malware families, including malware such as Qakbot (also known as Qbot), Dridex, TrickBot and Emotet. The following chart shows the number of malware samples that the NCSC has been able to identify as belonging to the Emotet malware family since mid-December. The two large spam waves shortly before Christmas 2021 and in week 2 of this year, which distributed Emotet on a large scale, are clearly visible.
Tips to protect yourself from malware
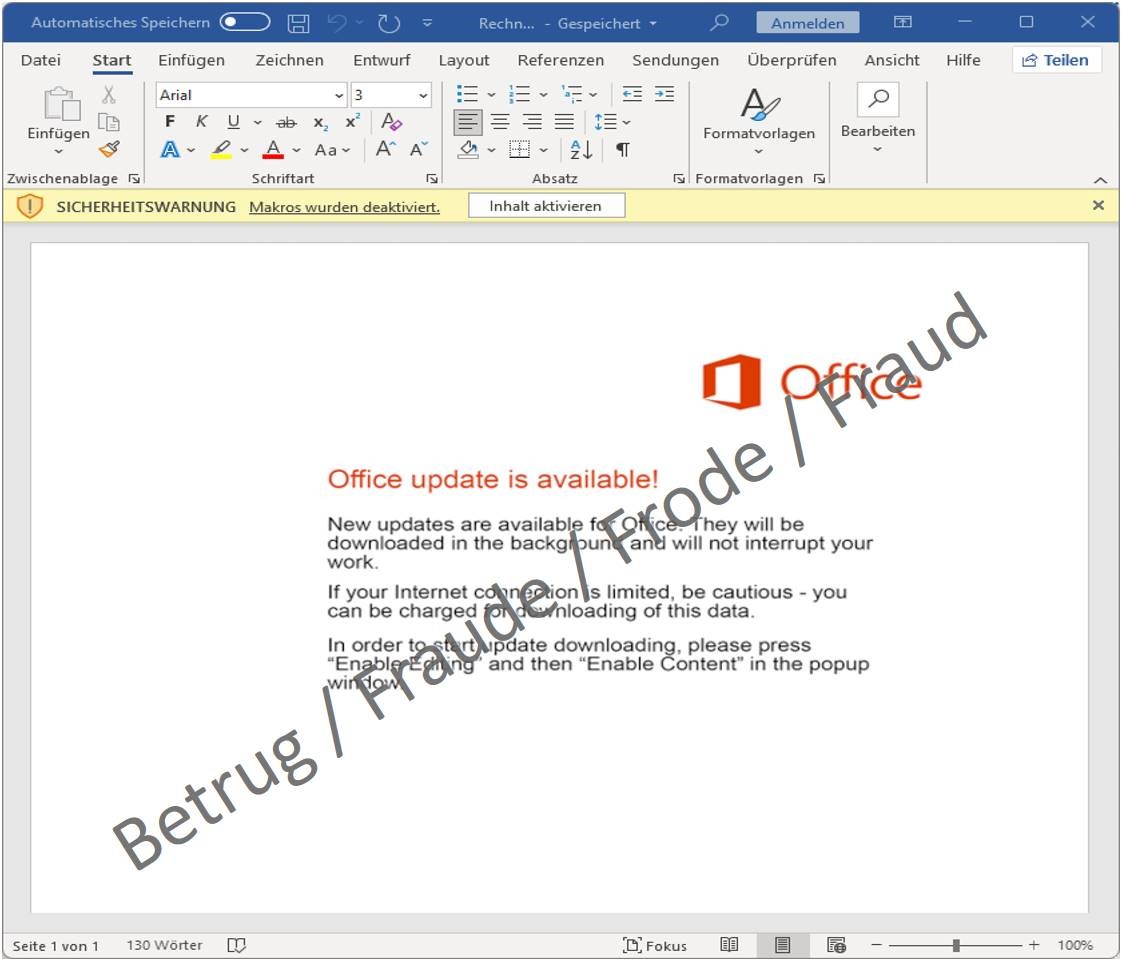
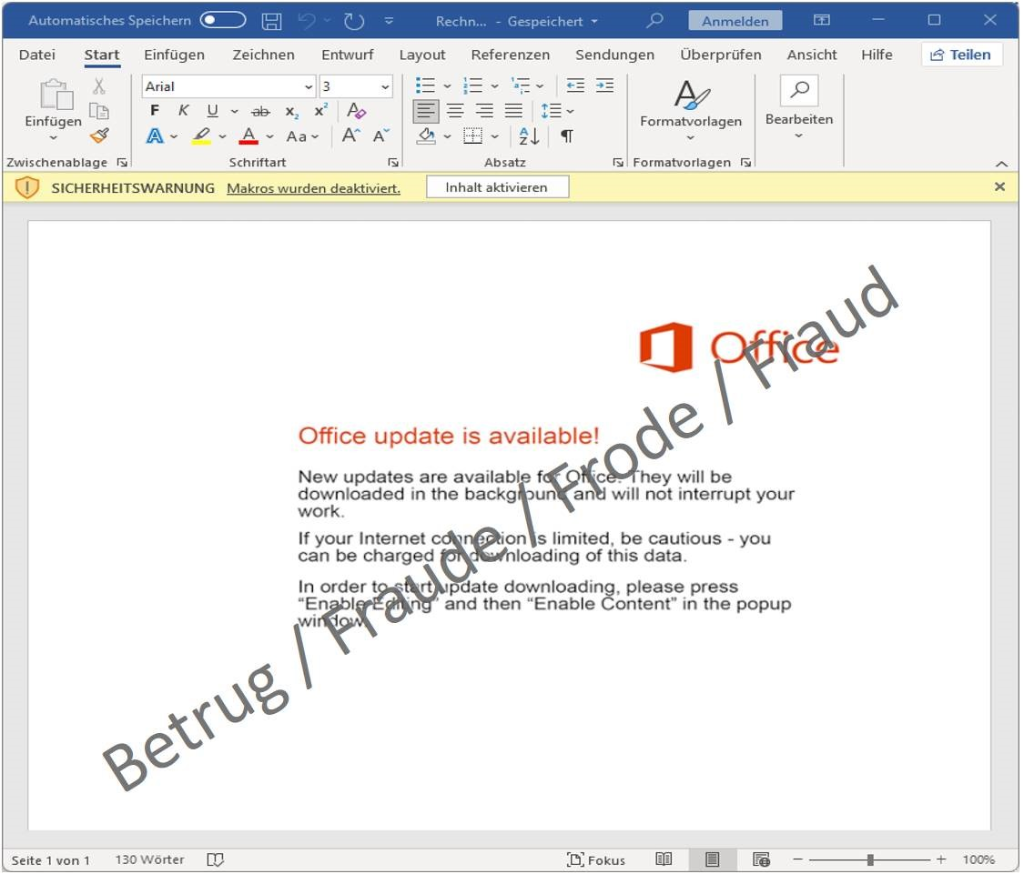
The user's consent is usually required for Office to execute macro program code. In the following example, the attackers try to do this under the pretext that an Office update is available, which is why the "content" must be activated. In reality, however, Emotet is downloaded from the internet and infects the victim's system.
The best protection against such attacks is therefore not to execute any macros, even if you are strongly and explicitly urged to do so. If in doubt, always inform the IT department first or check again with the sender of the email. In addition, the NCSC recommends that companies fully block employee execution of macros using technical means and allow this only in justified individual cases.
Report suspicious emails
Report suspicious emails (phishing or malware) to the NCSC at: antiphishing.ch.
If you are not sure about an email, or if you would like feedback, use the NCSC reporting form.
Among other things, your report will help to ensure a better picture of the cybersituation and allow the NCSC to take appropriate
defensive measures if necessary.
Previous news items:
Last modification 20.01.2022