18.08.2021 - The NCSC has observed several successful cyberattacks on Swiss companies in recent months. In these attacks, cybercriminals encrypted corporate networks using an encryption Trojan (so-called "ransomware") and successfully demanded a ransom.

In recent years, the NCSC has often issued urgent warnings about cyberattacks involving ransomware. While such attacks are usually complex, the majority of them are relatively easy to prevent. The most common gateway for successful ransomware attacks involves unpatched systems and remote access connections such as VPN (virtual private network) and RDP (remote desktop protocol) that are not secured by two-factor authentication (2FA). Unfortunately, alerts from installed security software such as antivirus programs are also repeatedly ignored on critical systems such as Windows domain controllers.
The NCSC highlighted this issue back in February 2020.
Despite ongoing efforts by authorities and business associations over the years to raise awareness among companies in Switzerland of the potential danger posed by ransomware, recommended measures and best practices are not being implemented across the board. This leads to high risk exposure, which is why Swiss companies unfortunately fall victim to such cyberattacks time and again. Unfortunately, it is not uncommon for six- or seven-figure ransoms to be paid. This allows cybercriminals to finance the infrastructure necessary for such attacks and those involved, such as money launderers, and thereby prepare attacks on other companies.
Measures against ransomware:
The NCSC again highlights the measures recommended by the authorities and urges companies in Switzerland to implement them consistently:
- Patch and lifecycle management:
All systems must promptly and consistently receive security updates. Software or systems that are no longer supported by the manufacturer (end of life, EOL) must be switched off or moved to a separate, isolated network zone.
- Securing remote access connections:
Remote access connections such as VPN, RDP, etc. as well as all other ways of accessing internal resources (e.g. webmail, SharePoint, etc.) must be secured with two-factor authentication (2FA).
- Blocking dangerous email attachments:
Block the receipt of dangerous email attachments on your email gateway, including Office documents containing macros. A recommendation on file attachment types to be blocked can be found here:
https://www.ncsc.admin.ch/govcert#1737483390
- Offline backups:
Make regular backups of your data. Use the generation principle (daily, weekly, monthly – at least 2 generations).
Always make sure that you physically separate the medium on which you create the backup copy from the computer or network after the backup process, and store it safely.
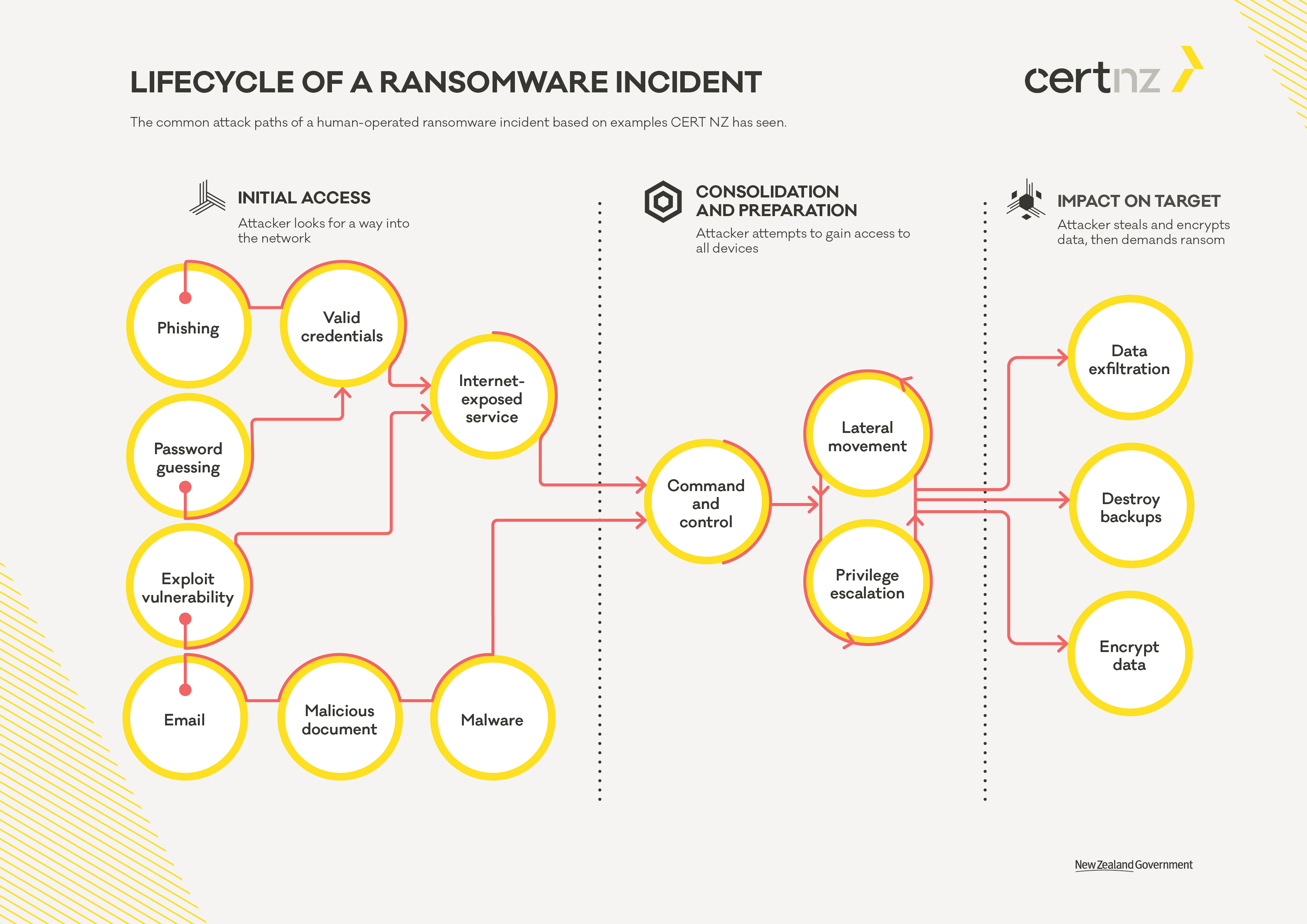
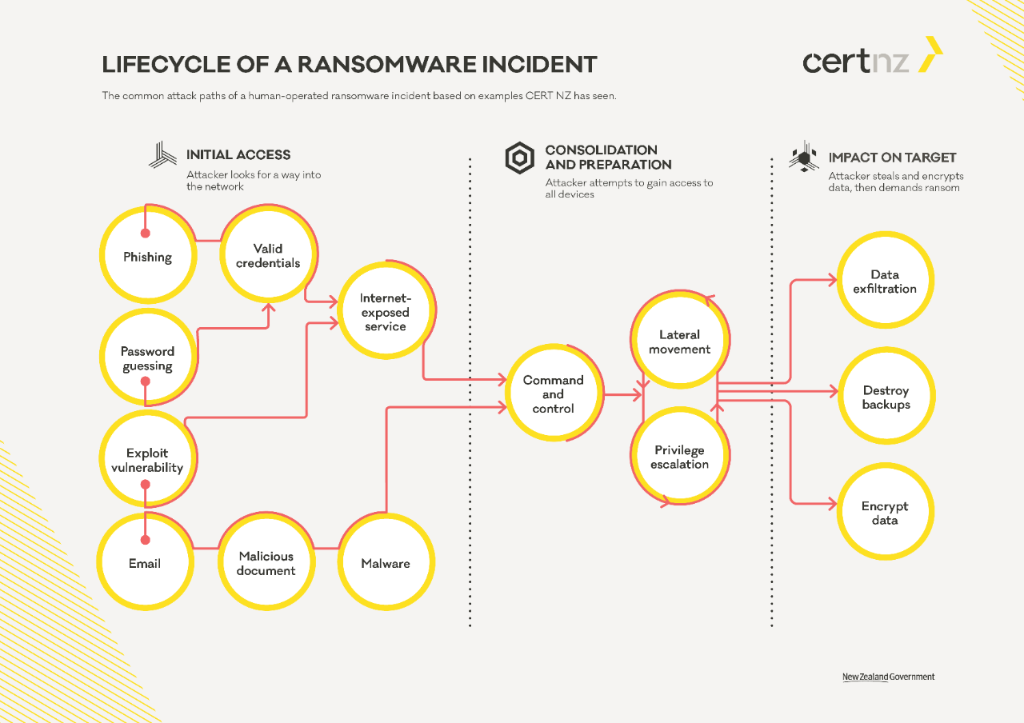
In the following report, CERT NZ provides an easy-to-understand illustration of the process of a ransomware attack:
How ransomware happens and how to stop it:
https://www.cert.govt.nz/it-specialists/guides/how-ransomware-happens-and-how-to-stop-it/
More information on ransomware and current attacks:
News:
Last modification 18.08.2021