09.08.2022 - The number of reports received by the NCSC remained unchanged last week. Two new phishing schemes stood out. In the first phishing variant, a link allegedly leads to a personalised online sharing service, where people have to enter the password for their webmail. In the second new variant, a fake QR code bill in the name of Sunrise is sent via email.

Webmail phishing via online sharing service
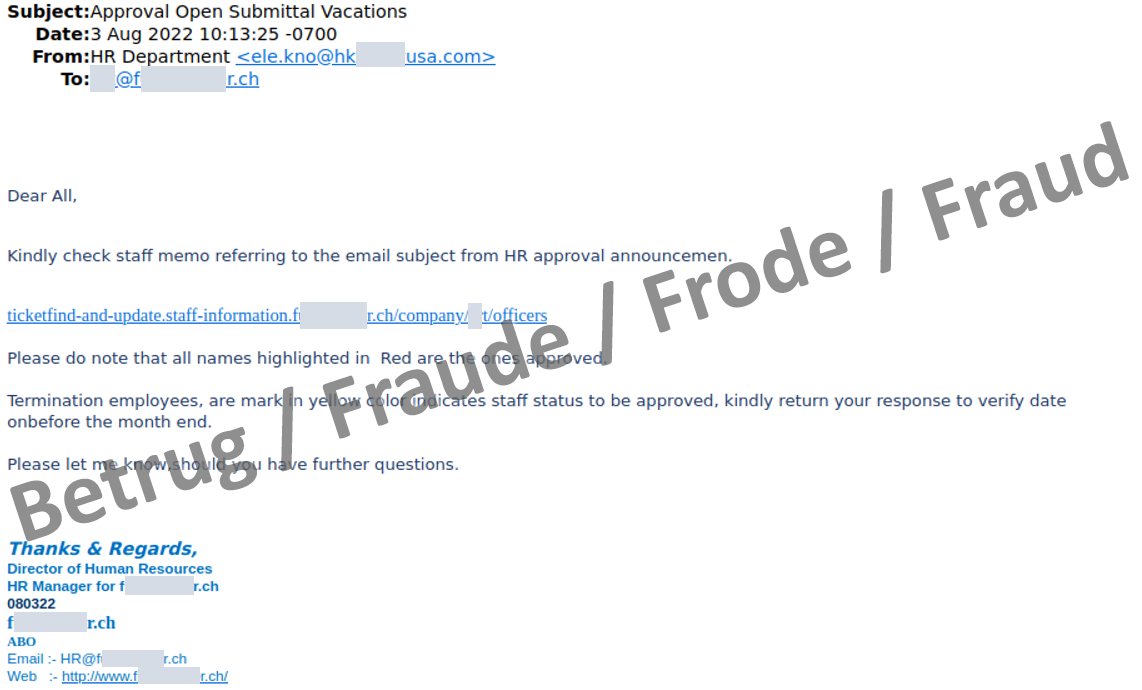
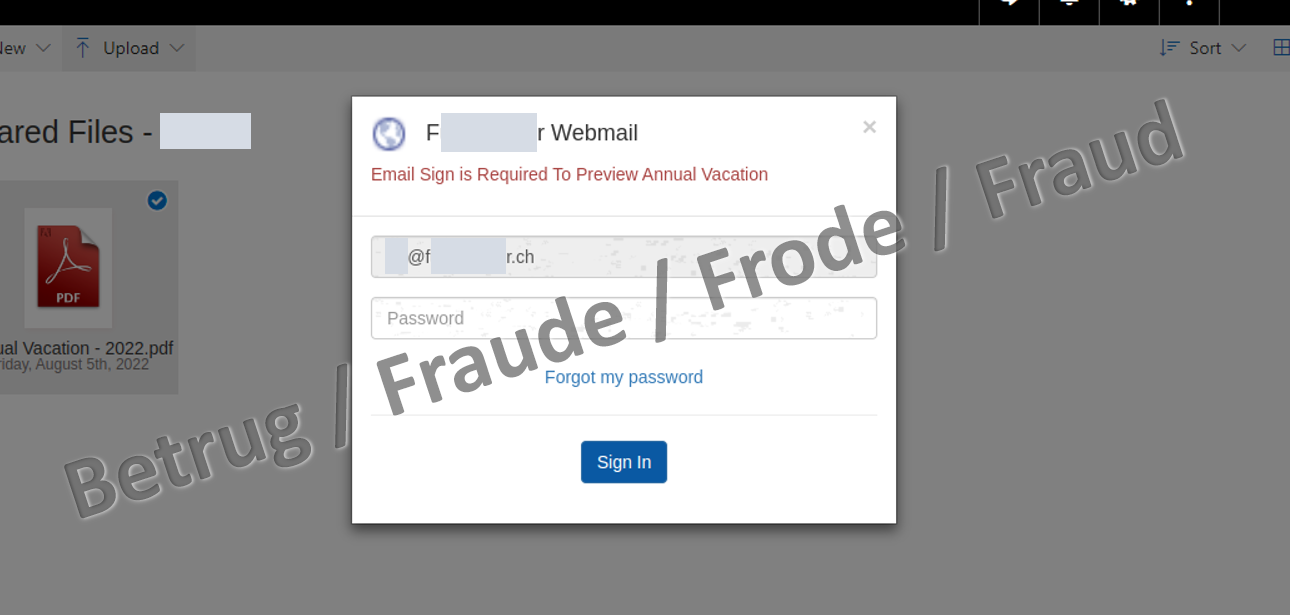
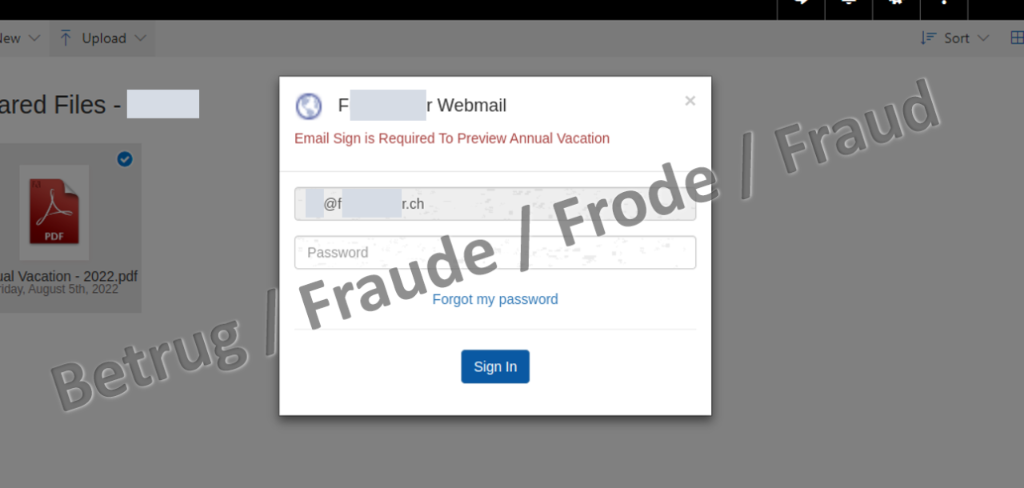
One of the attackers' aims is to use phishing emails to obtain their victims' login credentials. This also applies in the cases currently being reported to the NCSC, where the login credentials for company webmail access are of interest. In order to obtain these credentials, the phishers send an email with a link to a document that is to be approved, e.g. the holiday schedule like in the example below. The header and footer give the impression that the document is from the HR Department of the attacked company.
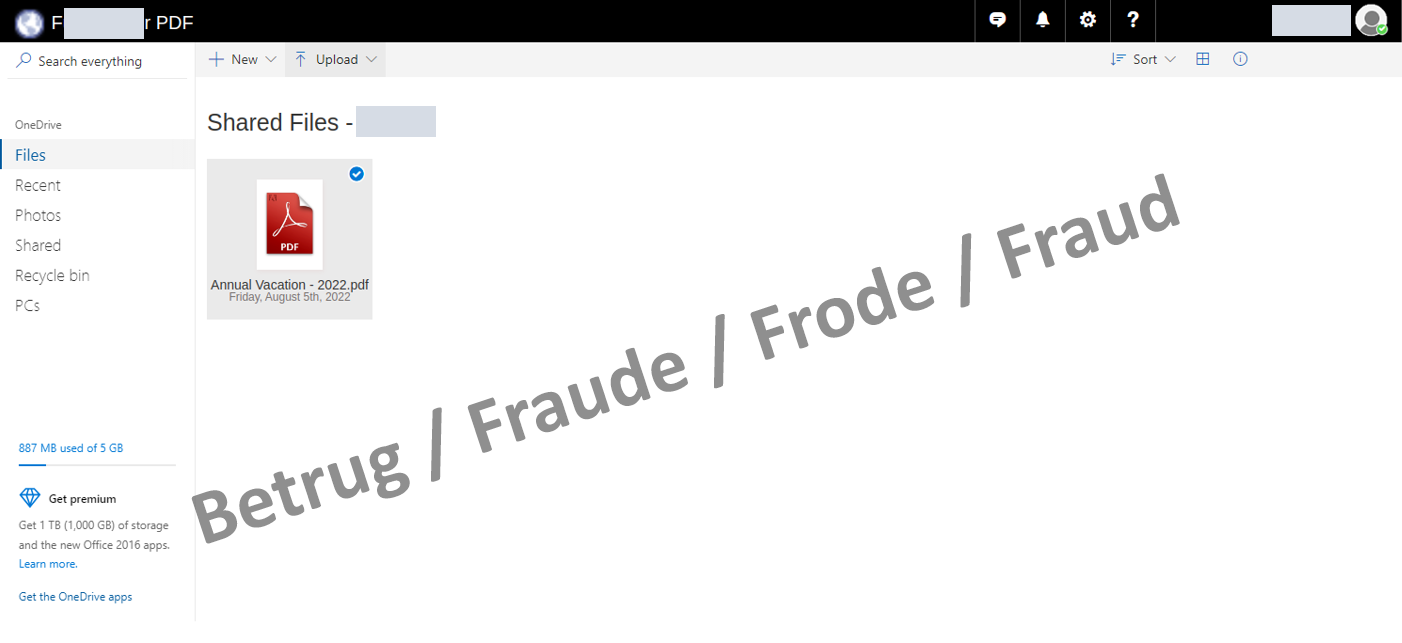
The link in the email leads to a phishing page posing as an online sharing service, rather than to a document. To make the page look trustworthy, the application automatically tries to fetch and display the logo of the targeted company in the background (this is usually stored on the company's website as favicon.ico). The design of the page itself is very simple: all that is visible is a background image and the link to the PDF document that is supposedly to be approved.
The actual phishing attempt takes place when someone tries to open the PDF. A window pops up with the attacked person's email address already displayed and a prompt to enter a password.
Closer examination of the page has revealed that the whole thing is transmitted as an error message, with the page itself masquerading as a "status code 404 – page not found" message. It is safe to assume that this is intended to deceive programs that automatically detect phishing and report the sites in order to have them blocked.
- Do not click on any links in emails if you cannot identify their origin beyond doubt.
- Do not enter login credentials via a link in an email.
- Use the reporting form to report any such attempted attacks to the NCSC.
NCSC reporting form
Sunrise bill with QR code turns out to be phishing attempt
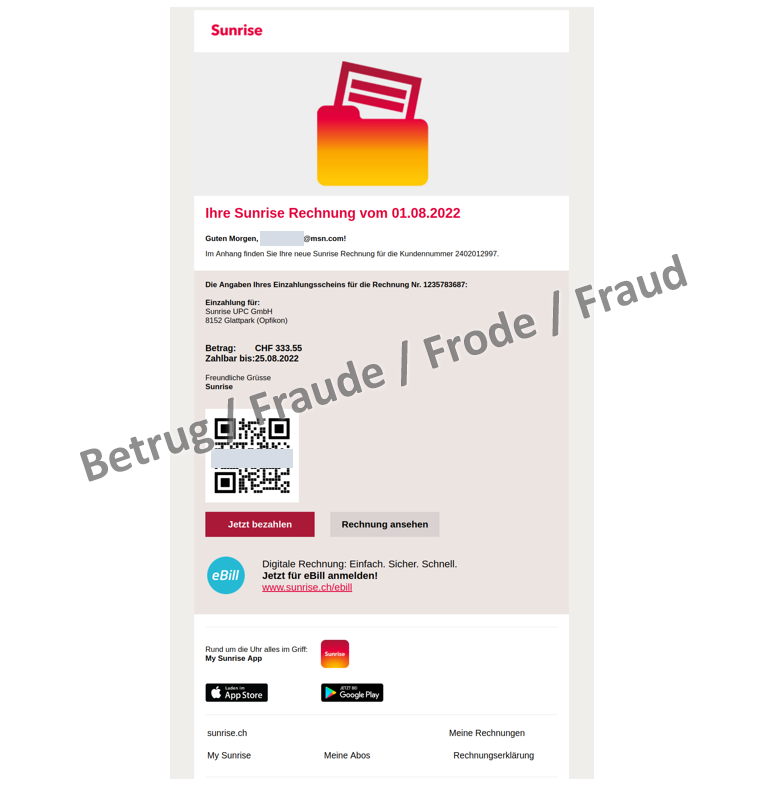
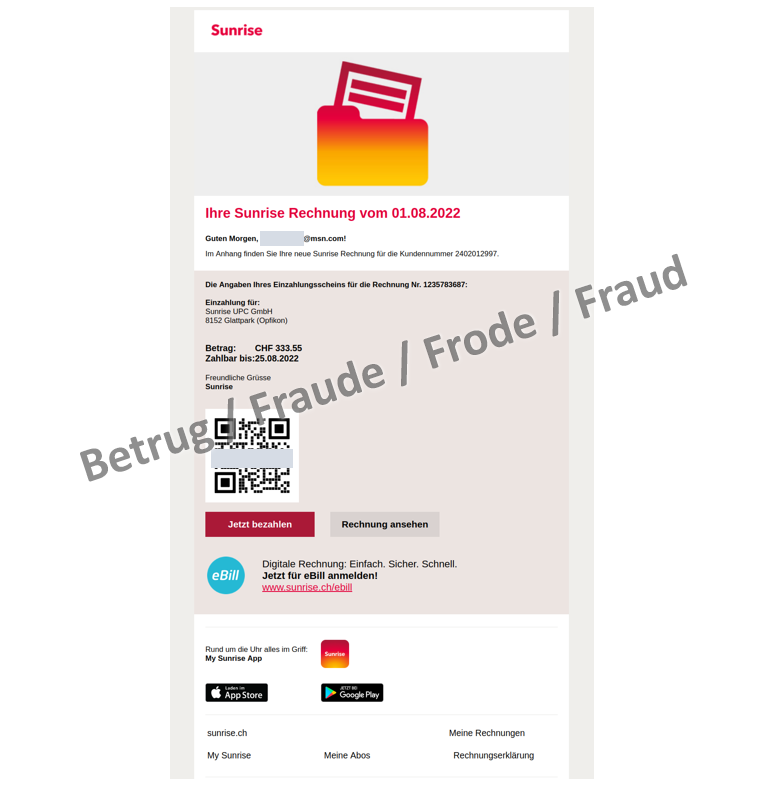
New opportunities are opening up for attackers, too, with the widespread use of QR codes for paying bills and executing transactions directly from mobile phones. This is evidenced by the phishing attempts currently being reported to the NCSC. The phishing email in this case has a sophisticated design and is not recognisable as phishing at first glance. However, the attackers still have the old Sunrise logo and address victims with their email address rather than by name. The usual "Pay now" and "View bill" are inserted as clickable buttons.
Additionally, there is a QR code, which leads to the phishing page via a link shortener "qrco.de/xxx". The website "qrco.de" offers the possibility of creating individual QR codes. Therefore, the phishers have to create a new code manually for each new link, which is very time-consuming for the large number of phishing pages. It is also interesting that the link behind the QR code is different from the link behind the "Pay now" button (but both lead to the same phishing page). Therefore, the phishers may still be testing and evaluating the success of QR codes.
- Use a reliable app that is recognised as secure to scan QR codes.
- After scanning and before execution, most scanners will display the action to be performed or the page to be accessed. Check this information.
- Never enter login credentials on a website that you accessed via a QR code.
- You can find more background information on QR codes here:
QR codes – uses and risks
Current statistics
Last week's reports by category:
Last modification 09.08.2022