11.10.2022 - The number of reports received by the NCSC declined further. In recent weeks, the NCSC has received reports of blackmail messages sent to web administrators. These are fake extortion messages that are similar in style to the well-known fake sextortion emails with empty threats and repeatedly used cryptocurrency addresses.
Fake extortion messages targeting web administrators
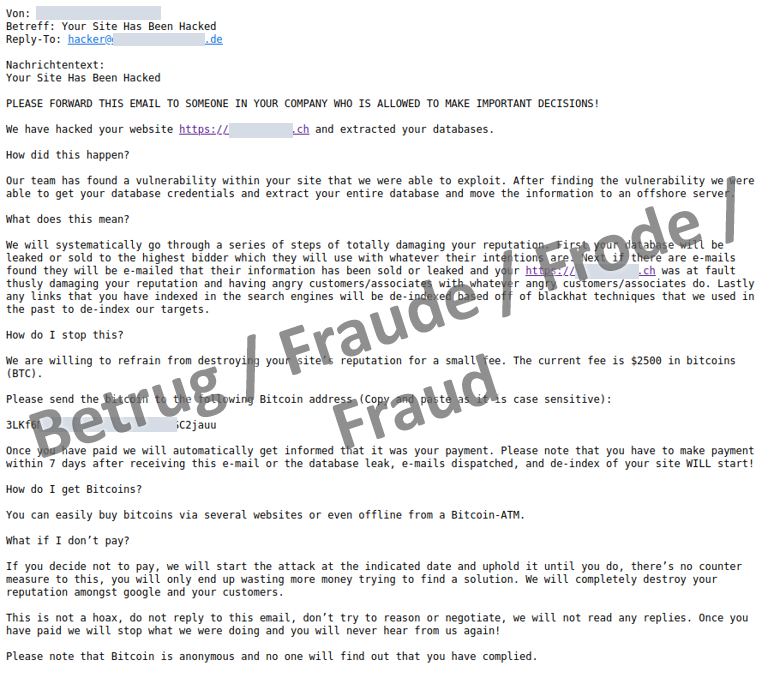
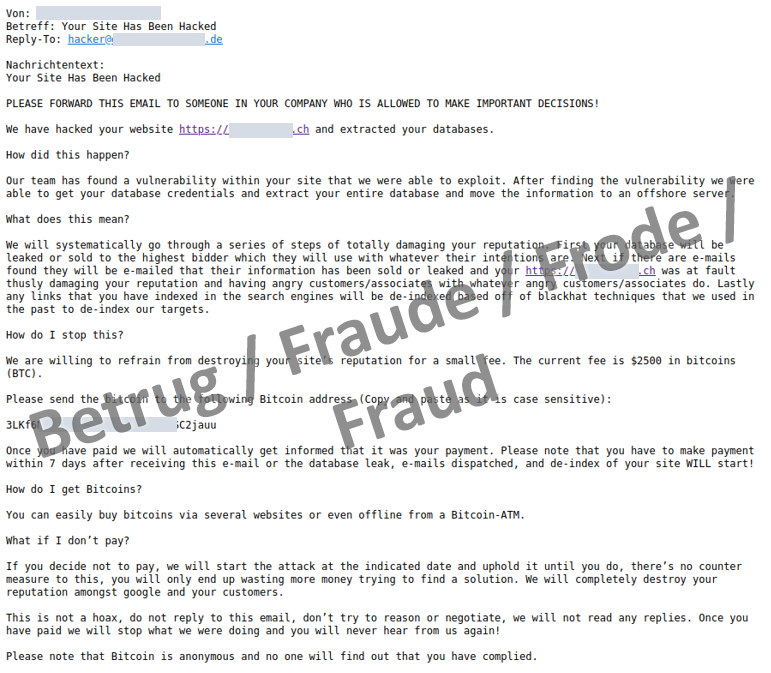
In recent weeks, web administrators have had to be careful not to become overly alarmed. In a message, usually sent via the website's own contact form, it was claimed that the website in question had been hacked and the data stolen. The data was to be sold to the highest bidder and the company's customers were to be informed about the hack in order to tarnish its reputation.
However, at second glance and on closer reading of the extortion message, it is apparent that there is absolutely no evidence of the alleged hack. The hacks mentioned in the extortion messages are fictitious and never took place.
The threat is structured in a similar way to the widespread fake sextortion emails, which claim that the blackmailers have access to the computer and filmed the email recipient consuming pornographic websites.
The many cases of data theft and ransomware attacks act as a credible backdrop for the blackmailers' fake extortion. However, the extortion texts are highly standardised and the blackmailers usually use the same cryptocurrency address, which means that they would be unable to distinguish which of the attacked web administrators paid. In the extortion messages currently being sent, however, the NCSC has so far only observed cryptocurrency addresses that have been used just once.
The NCSC has also found that the same extortion messages were already circulating during a 2020 spate of attacks. Therefore, the extortion scam and the associated tools are actually old news. Nevertheless, it is of course worthwhile to double-check that the web environment is fully patched and protected against standard attacks.
Recommendations:
- Ignore such emails and do not allow yourself to be intimidated.
- You can visit the following website to check whether other people have already had negative experiences with the bitcoin address provided:
https://www.bitcoinabuse.com/
- Protect your network and CMS:
Measures to secure content management systems (CMS)
Current statistics
Last week's reports by category:
Last modification 11.10.2022