15.11.2022 - The number of reports received by the NCSC rose sharply compared to the previous week. Once again, threatening emails in the name of the police were the reason. An email sent to the NCSC in Cyrillic script also attempted to distribute the Xloader/Formbook malware.

Malicious product request and undelivered email notifications – the daily attack attempts against the NCSC
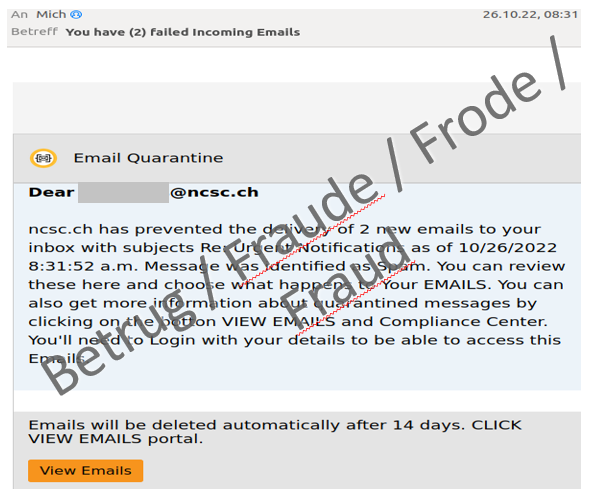
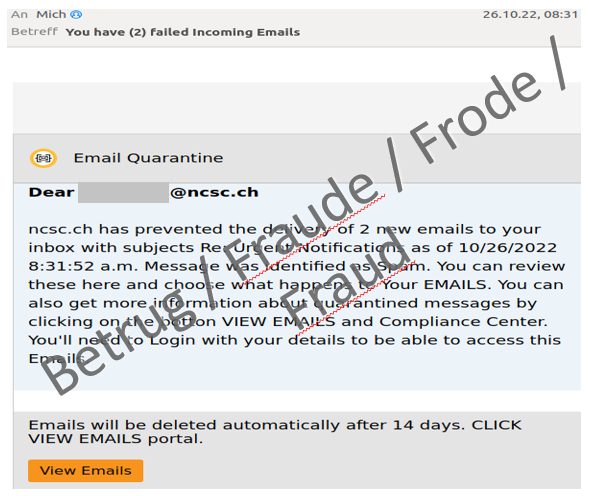
Even the NCSC is not spared from phishing emails and emails containing malware. Especially popular are phishing attempts claiming that urgent messages could not be delivered and that people should provide the respective email password.
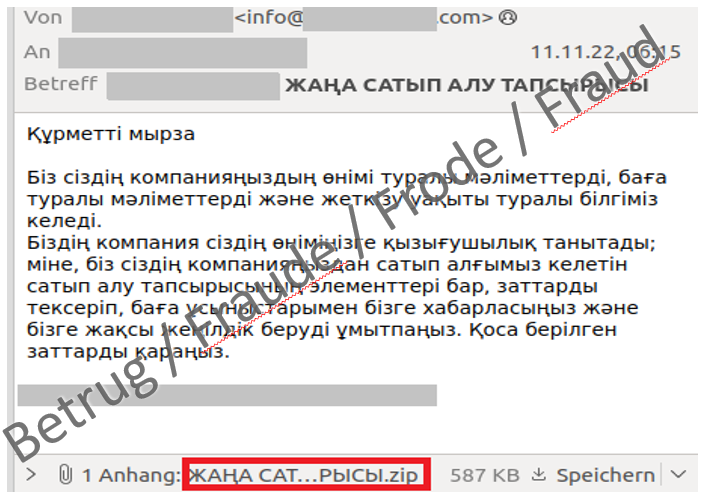
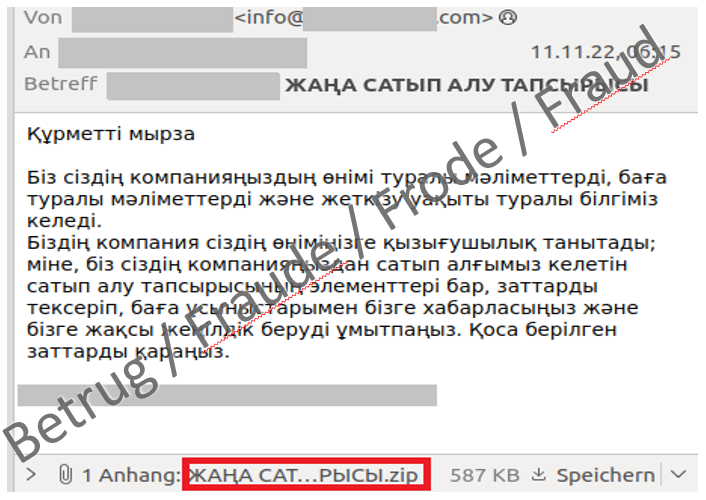
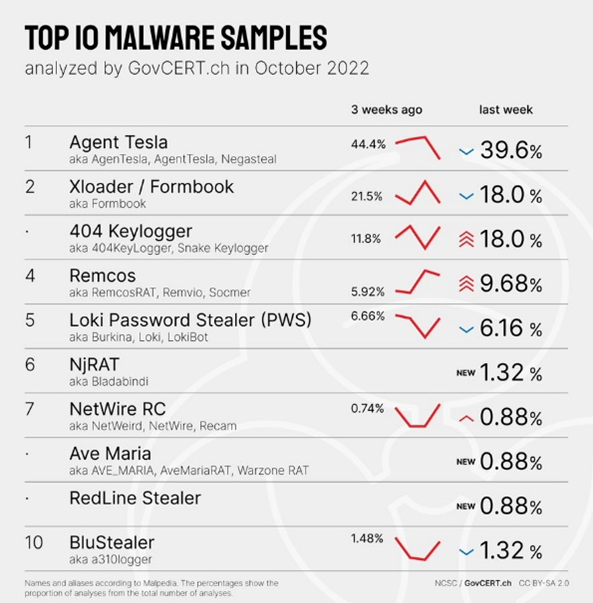
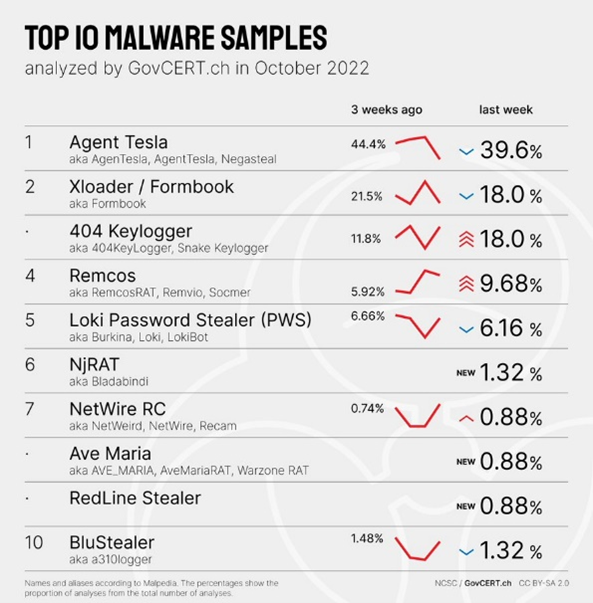
The NCSC received an unusual email last week: in Cyrillic script and with the subject "New order", it pretended to be interested in the NCSC's "products". The message explained that more details about the desired articles were listed in the attachment. A relevant ZIP file was attached to the email, but those who looked for documents in it did so in vain. The attachment contained the widespread and well-known malware Formbook alias Xloader.
This malware also regularly features among the leaders in the monthly NCSC/GovCERT.ch malware rankings.
FormBook and its newer successor Xloader are so-called "info stealers" that are distributed as malware-as-a-service (MaaS). Attackers can thus "order" the attack on the darknet without needing to have IT knowledge. Xloader's repertoire includes "stealing login data from web browsers and banking apps" and capturing keystrokes and screenshots. In addition, data can also be downloaded and executed. As with most attacks, the current one was not targeted: the mere fact that the NCSC does not sell any "products" and is not a conventional company shows this. The attackers did not do any research beforehand, instead they sent the request on the off-chance; the email probably also went to a large number of other recipients at the same time.
- Beware of emails that require action on your part and be careful if you are urged to perform an action. This may involve clicking on a link or opening an attachment, for example.
- Never enter personal data on a form that you have opened via a link in an email.
- Wherever possible, install two-factor authentication. This offers an additional layer of protection to prevent your account from being hacked.
- Bear in mind that email sender IDs can easily be spoofed.
Current statistics
Last week's reports by category:
Last modification 15.11.2022