29.11.2022 - Last week, the NCSC received 647 reports, fewer than in the previous week. A Microsoft Office 365 phishing scam drew particular interest. In the targeted attempt, the phishers not only chose an internet address that looked very similar to the company's actual address, but also used a trick to try to obtain other valuable information in addition to the password.

Microsoft Office 365 phishing with additional function
Intercepting Office 365 login credentials remains very popular among fraudsters. This is because such credentials can be used to access not only data stored in the Microsoft cloud, but also the email account. Access to an email account is valuable for the fraudsters because it allows them to reset login credentials with other providers, for example online retailers. Therefore, it is not surprising that attackers are refining methods to phish Office 365 credentials, as the following case demonstrates.
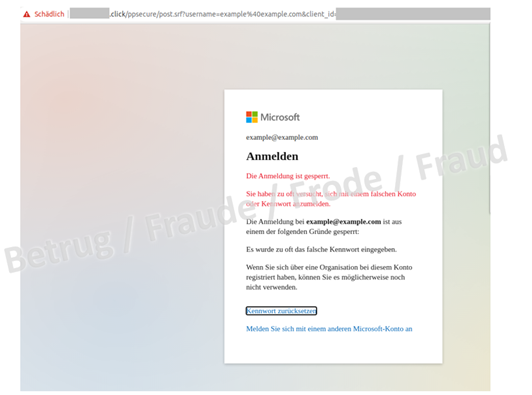
A company reported a phishing email to the NCSC, which uses the company's name (referred to in the following fictitious example as ACME) with the extension "-ch" and in the top level domain ".click" as the phishing link. Such a domain looks relatively unsuspicious, as it is very close to the original: www.acme-ch.click. An Office 365 login window is displayed on the spoofed website.
In previously reported Office 365 phishing variants, the login window appears again after the login data is entered on the spoofed website, which leads most people to spot the phishing attempt as such. This is not the case with the newly reported scam: Once the credentials have been entered, the site announces that the account has been blocked and prompts the phished person to reset the password.
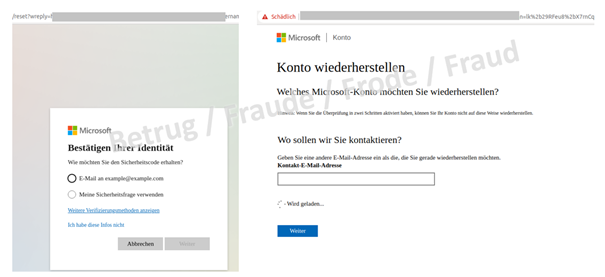
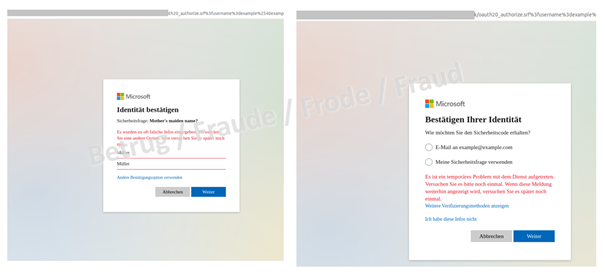
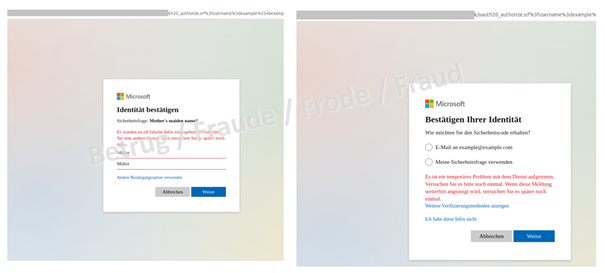
Two choices appear for resetting the password. The first option claims that the password can be reset by clicking the "reset password" link and entering a different contact email address. Of course, since it is a spoofed website, no email is sent to the phished individual so that he or she can reset the password. On the contrary, this means that the phishers obtain knowledge of other email accounts owned by the victim.
The second option to supposedly reset the password also only serves to provide the attackers with additional information, in this case the mother's maiden name. Since "confirm" does not work either, the phishers encourage you to try again.
By using the familiar functionality of the Microsoft Office 365 login framework, the phished individuals become less suspicious and the attackers obtain additional email addresses and information. In combination with any other publicly viewable information, for example from social media, further attacks can be carried out on the individual's online accounts or even in the individual's name.
Recommendations:
- Always check the open internet address (URL) before entering a password;
- Beware of emails that require action on your part. Be careful if you are urged to perform an action. This may involve clicking on a link or opening an attachment, for example.
- Never enter personal data in a form that you opened via a link in an email.
- Wherever possible, install two-factor authentication. This offers an additional layer of protection to prevent your account from being hacked.
- Bear in mind that email sender IDs can easily be spoofed.
Current statistics
Last week's reports by category:
Last modification 29.11.2022