17.01.2023 - In the second week of 2023, the number of reports received by the NCSC was up significantly on the first week of the new year, with a total of 836 reports. The already familiar CEO fraud scam is currently experiencing a revival, with the scammers not only sending emails, but also calling the victims to stress their fraudulent demands.
Week 2: CEO fraud targeting companies in French-speaking Switzerland – the scammers also contact their victims by phone

Last week, there was an increase in reports concerning CEO fraud attacks targeting companies. This type of attack combines two techniques that are used in one way or another in almost all cyberattacks, i.e. open source intelligence (OSINT) and social engineering.
The term open source intelligence means that the attackers obtain as much information as possible about their intended target from publicly accessible sources beforehand. Social engineering refers to direct interaction with the victims in order to manipulate them and ultimately persuade them to do what the attacker wants. In the case of CEO fraud, the attackers typically use OSINT to determine the name of the CEO – hence the term for this type of fraud – and the financial officer. In the case of associations, they look for the chairperson and treasurer. A fake email ostensibly from the CEO is sent to the financial officer, instructing him or her to make a payment with respect to an allegedly urgent and confidential matter.
In the cases currently reported, the attackers have come up with an additional trick: they call the financial officer directly and pose as a certain Maître Muller, an alleged employee of a well-known audit firm. During the conversation, they claim to know the company's CEO, who has apparently referred them directly to the financial officer, and explain that the CEO will subsequently send an email with the payment details.
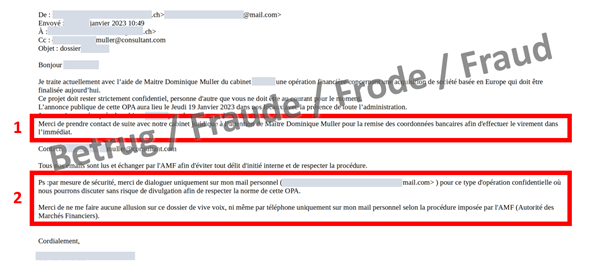
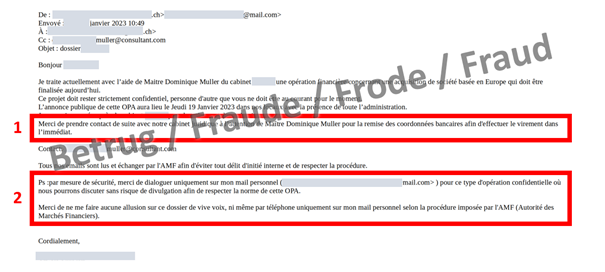
The email ostensibly from the CEO instructs the financial officer to contact the fraudster directly. Because of the confidentiality of the matter, only the private email of the boss is to be used (box 2 in the screenshot). Of course, everything is also "very urgent" (box 1 in the screenshot).
It is interesting that the email addresses used for the fraud are the already familiar consultant.com, dr.com, etc. (see weekly review 11 of 2022). The scam involving phone calls is currently being reported only from French-speaking Switzerland, which indicates that the attackers are from a French-speaking area. However, it cannot be ruled out that this scam will subsequently be used in the German- and Italian-speaking parts of Switzerland.
Recommendations:
- Raise all employees' awareness of CEO fraud! Especially employees in finance divisions and in key positions must be informed about these possible methods of attack. In the case of associations, all presiding members and treasurers must receive training.
- Do not divulge any internal information and be careful with payment requests. Do not respond to unusual payment requests.
- All processes which concern payment transactions should be clearly defined internally and complied with by employees in all cases (e.g. dual control principle, joint signature by two people).
Current statistics
Last week's reports by category:
Last modification 17.01.2023