19.12.2023 - Fraudulent job advertisements are all too common – most of them are designed to swindle victims out of money under false pretences. One advertisement in particular stood out because the fraudsters did not follow the usual pattern, and instead attempted to plant malware during a job interview in order to subsequently take over the victim's cryptocurrency wallet.

The advertisement
A jobseeker comes across an exciting job offer in the area of crypto investments while searching on a well-known job advertisement platform. A company based in Switzerland and active in this field appears to be behind the advertisement. The interested jobseeker decides to submit their application and CV.
The application process
The applicant is contacted by email and informed that their application has been considered favourably. They are asked to enter further information about themselves in an online form and are informed that the next step will be an initial interview via video conference.
As requested, the applicant fills out the online form with some personal details – slightly disconcerted that they are also asked for a cryptocurrency wallet, ostensibly so that any profit sharing can be paid out.
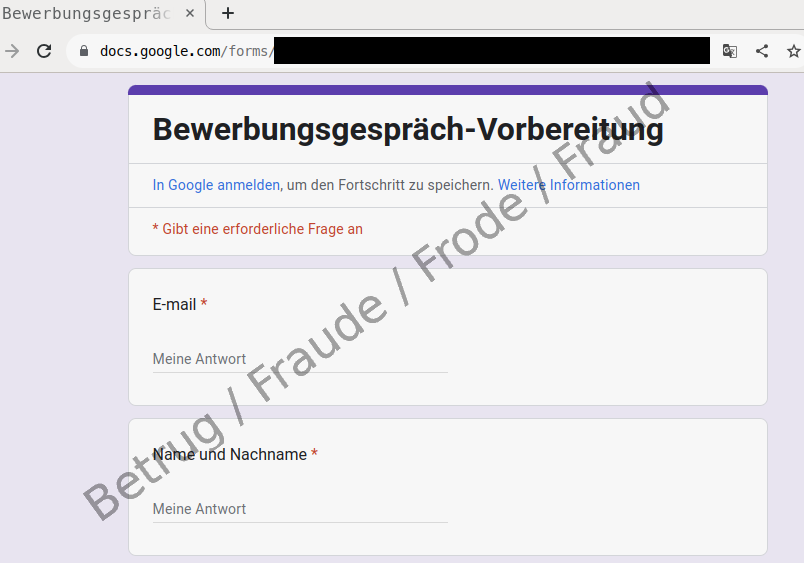
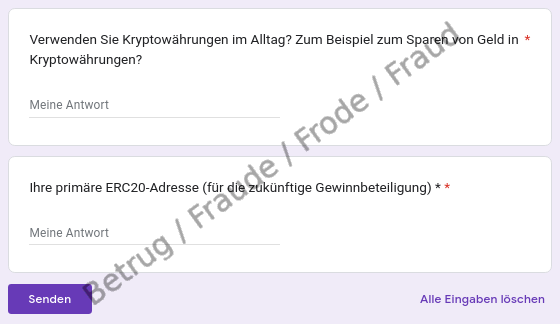
After completing the form, the applicant organises the video conference by going to the website provided and trying to download the video tool. However, the browser issues a malware warning. When asked by email, the supposed company confirms that the tool is OK and that, for confidentiality reasons, an interview is possible only with this tool. As a result, the applicant ignores the browser warning. However, the virus scanner alert on the applicant's computer is the next thing to go off, and it too issues a malware warning. Now the applicant becomes sceptical and suspects a fraud attempt, and contacts the NCSC.
The fraud attempt
The NCSC's analysis revealed that this was a very elaborate fraud attempt. It started with the job advertisement, which was placed for the sole purpose of deceiving potential applicants.
To prevent the victim from becoming suspicious, a separate domain that looks very similar to the domain of the real company was set up in advance for contacting the applicant by email.
Another domain was registered on the same day, namely the one to be used to download the tool for the video conference.
Although the tool does indeed make it possible to take part in a video conference, unfortunately it does not stop there, as it also contains a keylogger, i.e. malware with a function for recording keystrokes on the applicant's device.
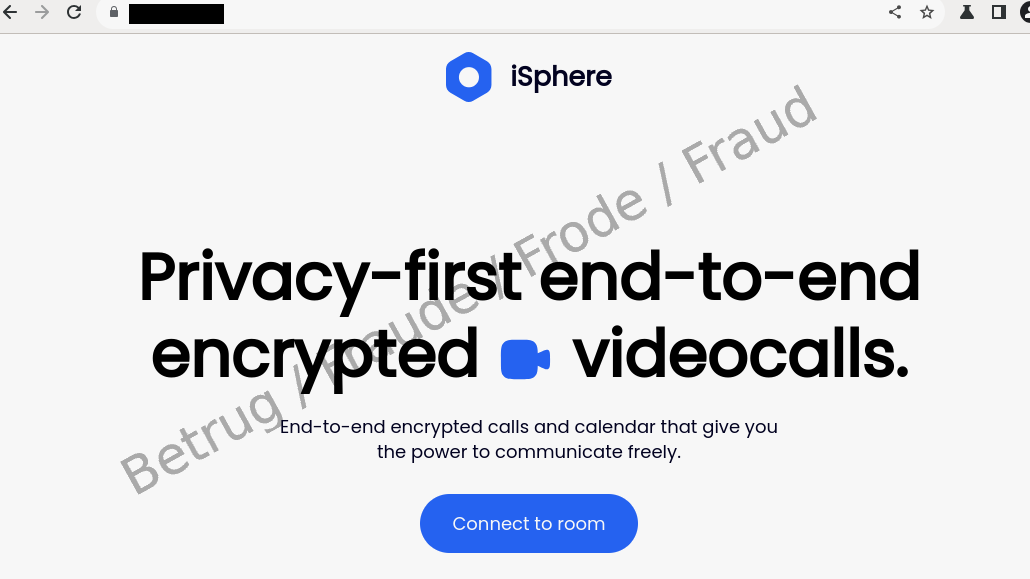
If the applicant had not become suspicious, the scam could have played out as follows:
- The applicant opens the video conference tool to take part in the interview.
- The fraudsters have already received the applicant's wallet ID via the online form, but now need the password to access its contents.
- During the video conference, they use an excuse to ask the applicant to quickly log into their wallet, e.g. to check their current account balance.
- The applicant does so and enters the relevant password. The keylogger records the input and sends it directly to the attackers.
- The fraudsters can then take over the wallet and transfer the cryptocurrency to their own accounts.
NCSC recommendations
To protect yourself from such scams, the NCSC recommends the following:
- When contacted, check whether the language and style of the messages are appropriate.
- In the event of inconsistencies or if you have any suspicions, clarify whether the company that supposedly advertised the position actually has vacancies. Make enquiries if necessary, e.g. by telephone, using the number indicated on the company's website.
- Abort immediately when your virus scanner detects something or a browser warning is displayed. False alarms in this area are very rare.
- Do not disclose your personal details too soon. Account details for salary payments, for example, are not relevant until a job has been confirmed.
Current statistics
Last week's reports by category:
Last modification 19.12.2023





