03.01.2024 - As is tradition, the NCSC looks back at the reports received over the past twelve months in the last weekly review of the year. Fake threatening emails and phone calls claiming to be from the police were the main features of 2023. These two phenomena alone accounted for over a third of the reports received. You can find out which other cyberthreats made an impact over the past twelve months in the last weekly review of the year. We would like to take this opportunity to thank you for all of your input and reports, which help the NCSC to better assess the situation in cyberspace and warn potential new victims at an early stage.
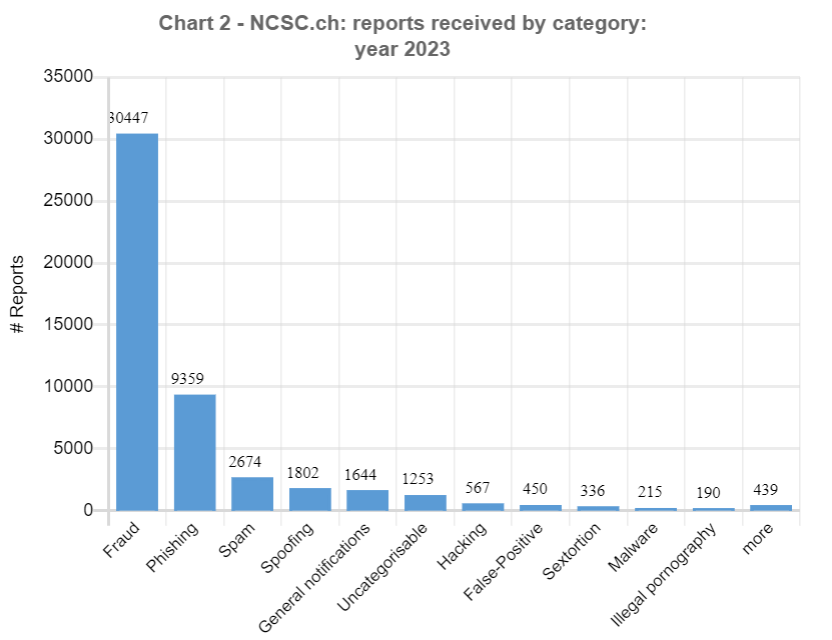
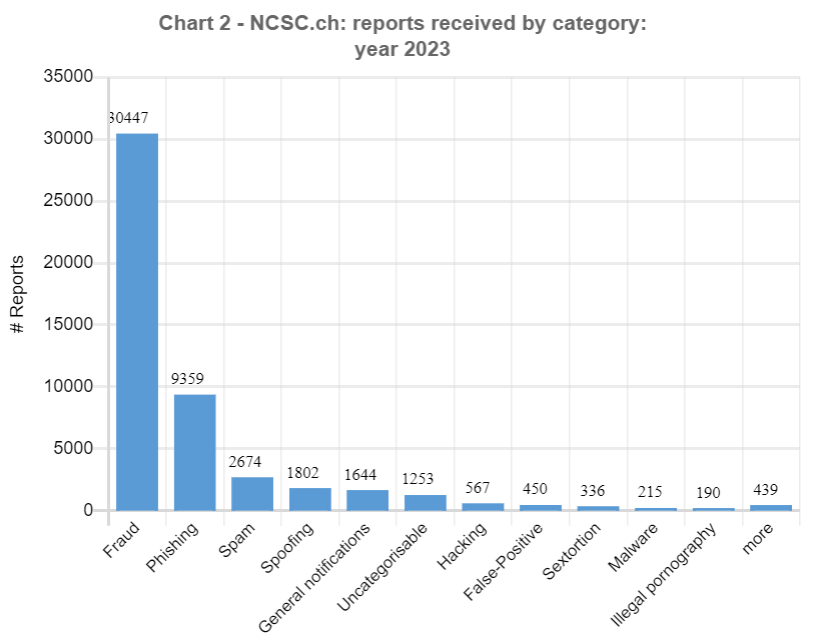
The total number of reports received by the NCSC grew once again in 2023. With almost 50,000 reports, the number rose by 30% year on year (34,527 reports). The increase in absolute figures was slightly higher than in the previous year at 15,000 reports (rise 2021/2022: +12,813). The further increase was due primarily to the rise in phenomena such as fraudulent job offers and bogus phone calls claiming to be from the police.
The ratio of reports from the general public (88%) to those from companies, associations and authorities (12%) remained stable. The fraud offences most frequently reported by companies saw a surge in the phenomena of CEO fraud (2023: 484; 2022: 116) and invoice manipulation fraud (2023: 118; 2022: 36). Reports concerning DDoS attacks (2023: 40; 2022: 24) were also higher. The number of reports regarding ransomware attacks on companies remained stable.
Fake threatening emails supposedly from the police at the previous year's level – but an increase in threats also made over the phone from June onwards
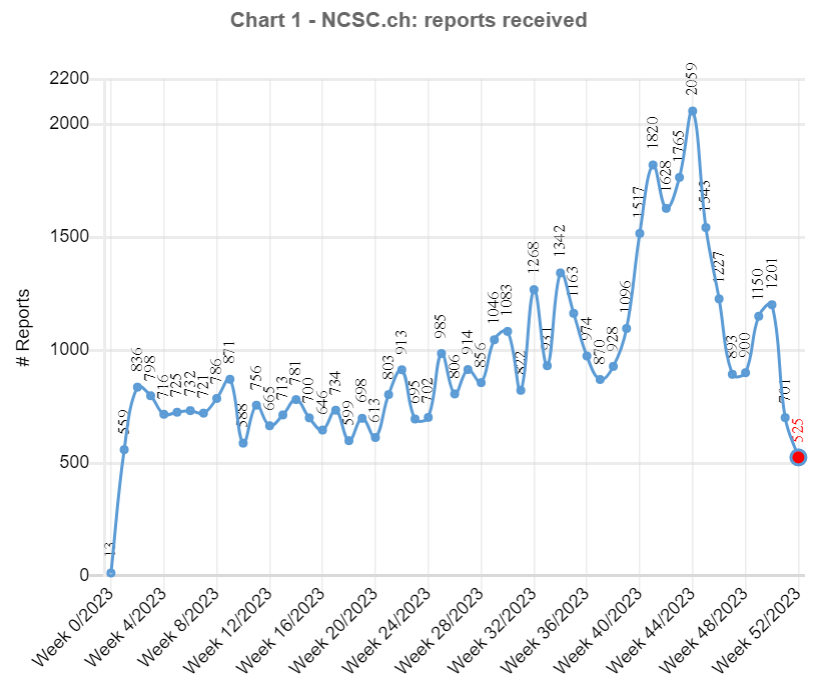
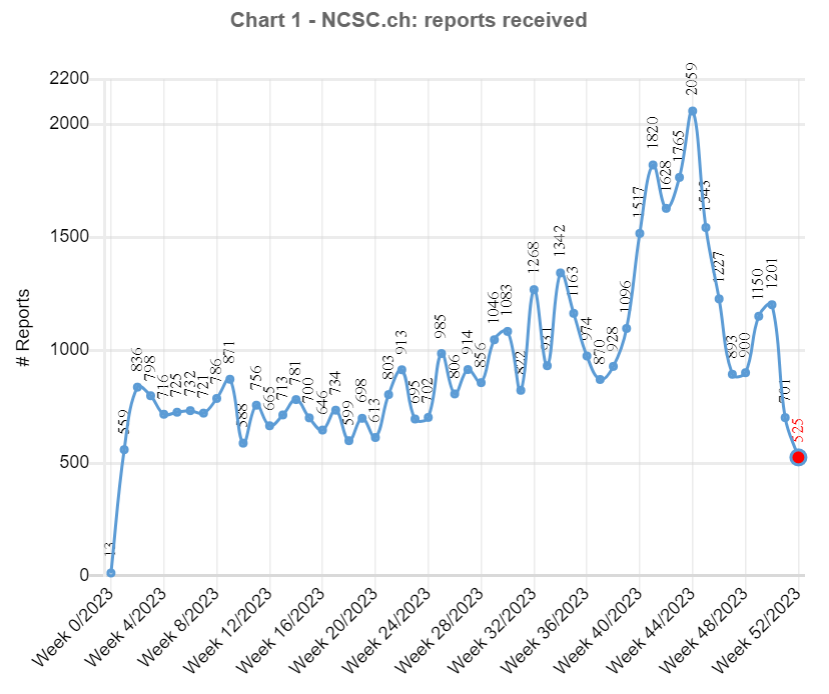
Threatening emails supposedly from law enforcement authorities were one of the phenomena most frequently reported to the NCSC already in 2022, and 2023 was no different, as almost 10,000 reports were received on this topic. These threatening emails claim that the people contacted have been found guilty of significant misconduct (typically in connection with child pornography) and that the charges against them can be dropped only if they transfer money. The first reports of a similar phenomenon by telephone were received at the end of June 2023. This variant starts with a phone call apparently from the police. A computer-generated voice informs the victim that their personal banking data, for example, is connected with a crime. For further information, the call recipient should press 1. If the victim presses 1, they are connected to an "employee" and told to download a remote access tool and grant the attacker access to their computer or mobile phone. The attackers attempt to gain access to the victim's e-banking account in this way and issue payments in the background via the remote access tool. Reports regarding this phenomenon skyrocketed in the second half of 2023, and peaked in calendar week 44, when the NCSC received a record 2,059 reports, around half of which (935) concerned threatening calls.
Spoofing remained an issue
The NCSC received nearly 2,000 reports in connection with spoofing, which involves fraudsters calling their victims and falsifying the telephone number displayed. This means that the already high number of 1,100 reports submitted in 2022 almost doubled. The problem became even worse with the emergence of fake phone calls claiming to be from the police. This phenomenon also involves fraudsters using fake caller display numbers. This approach is seemingly innocuous at first glance, but it has far-reaching consequences for those to whom the numbers belong. In the event of a missed call from the fraudsters, many return the call if the number is displayed, causing the owner of the number to be inundated with calls.
OFCOM obliges telephone providers to use state-of-the-art technology to protect their customers from calls with spoofed numbers. To this end, telephone providers may filter calls completely or, as a milder measure, prevent the caller's number from being displayed (similar to what is done in Germany). However, combating spoofing is challenging, as the attackers can easily fake their numbers and telephone providers have to decide whether to filter the call without knowing what it is about.
Chain phishing at companies, parcel post phishing and twice-paid bills for individuals
In the case of companies, the pressure on access credentials for company emails and Office365 accounts in particular continued to increase. More and more phishing attempts based on the snowball principle were observed. This involves hacking into a company email account and then sending a phishing email, supposedly from the victim, to the company's customers. If a customer falls into the trap, their customers are contacted and the game starts all over again. This approach is also known as chain phishing.
In the case of individuals, the most frequently reported phishing attempts were the same as the previous year. Thousands of fake parcel notifications are still being sent. Bogus refund emails supposedly from providers, SBB or the tax authorities are also part of the standard repertoire of phishers. The attackers primarily exploit the high likelihood that someone is actually expecting a parcel or has paid a bill issued by a provider, etc. This gives the email greater credibility.
Sharp drop in reports concerning ransomware – but only in the case of attacks targeting individuals
An increase was not observed for all phenomena. Especially in the ransomware category, the figures were down significantly on 2022. With around 109 reports received, there was a drop of almost 40 reports year on year. However, the decline did not affect companies, only individuals. Only 11 reports related to individuals were received in 2023, versus 56 a year earlier. Home NAS systems (network storage), which are a particular target in the case of individuals, are now only occasionally attacked. This may be partly because there was no serious vulnerability in 2023, and partly because the attacks were unlikely to be lucrative enough. More money can be made from individuals with other types of fraud.
The downward trend in the number of reports concerning ransomware at companies is much more moderate, with the number of reports received stabilising more or less at the previous year's level, i.e. 98 versus 103 reports. It should be noted that the attacks are now almost always accompanied by a data leak, which further increases the extent of the damage.
The LockBit ransomware is still particularly active. Other reported ransomware families were Play, MedusaLocker, BlackCat, Phobos, BlackByte, Black Basta, Babuk, eCh0raix and Akira.
The NCSC will become a federal office on 1 January 2024. We look forward to continuing to receive your reports, would like to thank you for your trust and support, and wish you a fraud- and virus-free new year, both in the digital and analogue world, and a good start to 2024!
Current statistics
Last week's reports by category:
Last modification 03.01.2024