12.03.2024 - Most of the phishing-related complaints received by the NCSC relate to emails or text messages designed to look like they originate from Swiss Post, the SBB/SwissPass or banks. In this edition of the week in review, we look at a variation on this theme targeting users of booking.com.

Hotels can also be the target of phishing attacks and malware. For those using the booking.com platform, a successful attack on their business accounts could also pose a risk for guests and hotel staff – an issue we’ve examined in more detail in a previous edition of the week in review:
In recent weeks, the reports of booking.com-related phishing attempts have been coming in not just from the hotels themselves, but also from guests.
Typical scenarios generally follow the same pattern. After a guest makes a hotel booking, they receive an email claiming that their credit card has to be checked again, or that their booking can only be confirmed once they have re-entered their credit card information. The email does in fact originate from booking.com and is sent from the account of the hotel that the guest has made a booking with – because the fraudsters have taken over the hotel’s account and are using it to send fraudulent messages. Recipients accept the messages as trustworthy because of their apparent (and verifiable) origin and because they contain the correct booking information.
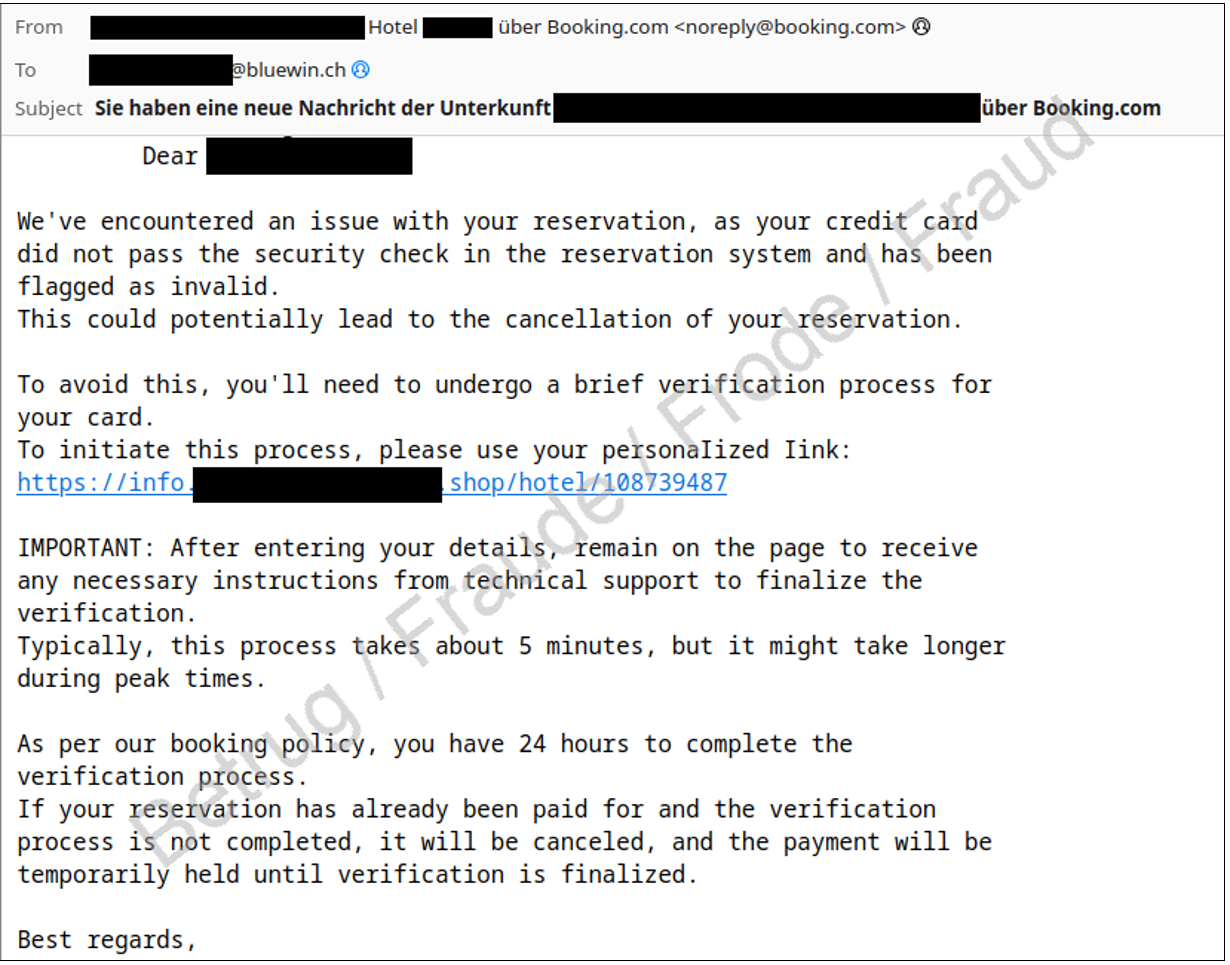
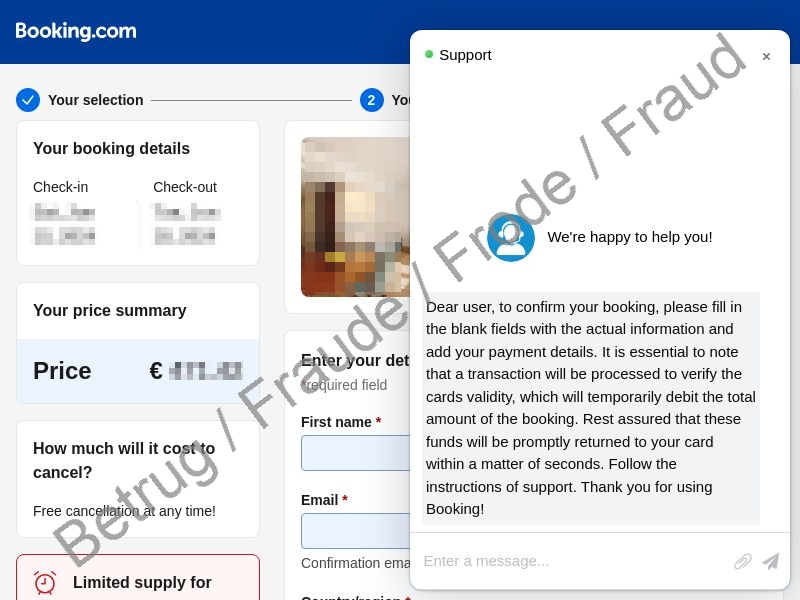
If a source email looks legitimate, many recipients will click on links without looking at them carefully. Furthermore, the links sent in these emails contain correct personalised information about the guest and their booking. The links do not lead to booking.com, however – instead, the user is taken to a phishing web page that is a professional-looking copy. The fake web page also shows correct information about the booking, and its design looks like that of the authentic booking.com site.
Once the guest enters their credit card details on the web form, the unexpected charges quickly begin.
Recommendations
- Always think carefully about suspicious requests, and never enter information on a web page that you have accessed using a link sent by unknown parties.
- If you realise you have entered your password on a phishing website, change the password immediately everywhere that you use it.
- If the password in question is an email password, reset your password for every service connected with this email address. This will prevent the fraudsters from using your email account to reset those other passwords.
- If you realise you have entered your credit card data on a phishing website, contact your credit card provider immediately so that they can block the card . If fraudulent charges have already been made on the card, the NCSC recommends making a report of a criminal offence with the local police.
- Activate two-factor authentication, which provides your online accounts with an additional layer of protection. This makes it more difficult for unauthorised parties to access them, even if they have managed to find out your password. Many online services offer this protection, including booking.com.
Current statistics
Last week's reports by category:
Last modification 12.03.2024





