28.11.2023 - Cybercriminals are trying new ways to trick hotels and their guests. In the emails currently being sent to hotels, they claim to have been bitten by bedbugs or that they were filmed in the hotel room and are now being blackmailed, among other things. The aim is to trick hotel employees into installing malware.

At the beginning of the year, the NCSC warned in its weekly review of incidents in which fake receptionists contacted hotel guests in order to obtain credit card details. People who had booked a hotel were contacted via WhatsApp and drawn into a chat. The attackers knew all the booking details and used this information to convince the guests that the request really was from the hotel. At the time, it was suspected that the attackers were able to gain access to the hotel's booking.com account. Recent cases have now shown how attackers attempt to infect hotels with malware in order to steal access data to online booking platforms.
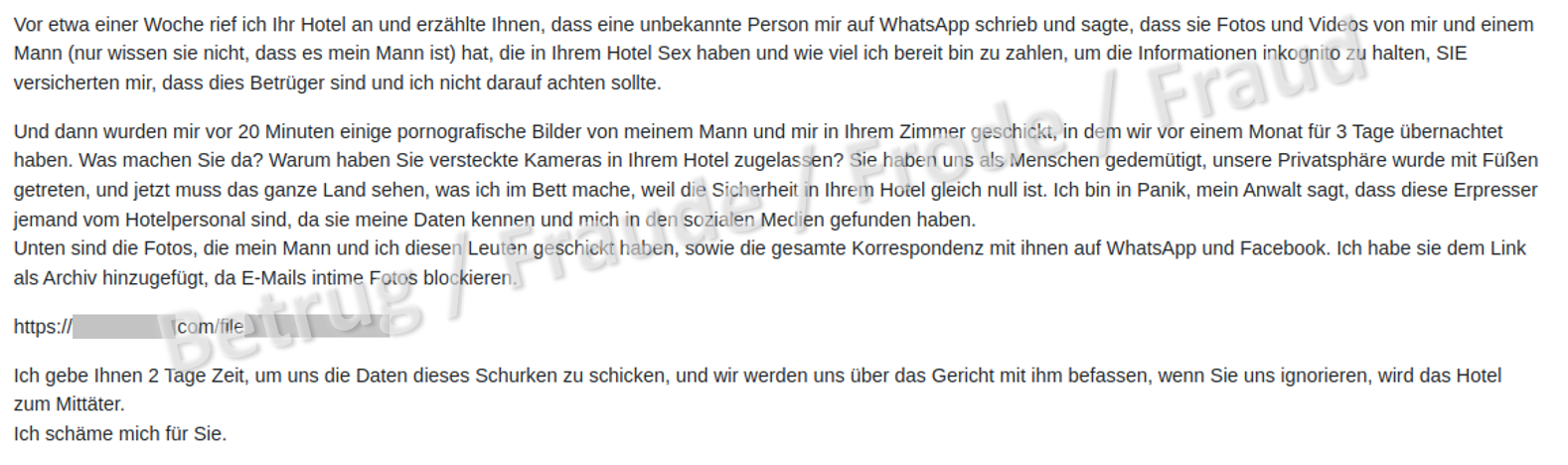
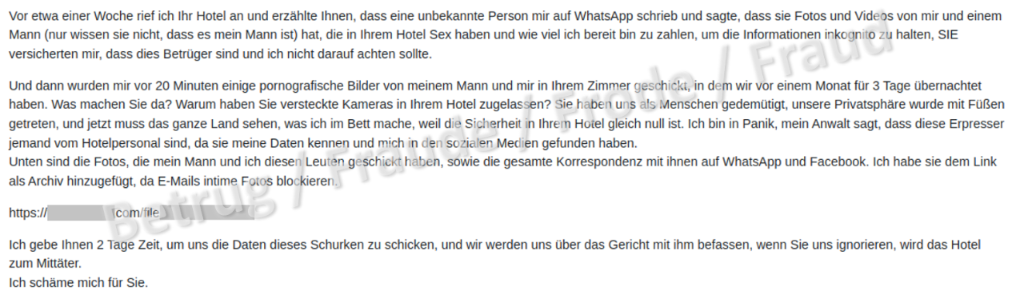
Blackmail using purported hotel room photos and videos
Reports received by the NCSC in the past week show that there is currently a wave of malware infections targeting hotels. Various social engineering methods are being used to trick hotel staff into clicking on a link and installing malware.
In one variant, the hotel receives an email from a supposed guest. The email claims that the guest is currently being blackmailed with pornographic images that were allegedly taken in the hotel room where the guest was staying. The guest gives the hotel two days to clarify the facts and name the perpetrator, otherwise the hotel will make itself an accomplice. All of the documentation relating to the case has been archived as evidence and the relevant file can be downloaded from the link provided.
Clicking on the link downloads a 50MB ZIP file, which expands to a 637MB executable file when unzipped. The size of the file is probably intended to give the impression that it contains a large amount of data, such as videos or photos, and to bypass anti-virus software – large files are often skipped during scanning. The file in question is malware.
The perpetrators' intention is clear: the attackers are trying to shock the hotel staff and tempt them to briefly act without thinking. When they click on the executable file, the system asks whether the victim really wants to install the file. This means that there is still an opportunity to prevent the infection. The attackers use this shocking story to try to prevent the victim from reading the warnings and instead simply click "OK" throughout.
The malware then records all the access data entered by the victim and sends it to the attackers. This allows the perpetrators to access the hotel's current bookings via online platforms such as booking.com.
Even bedbugs and health problems...
There are other variants in circulation in addition to the one mentioned above. For example, the NCSC received another report of an email in which a guest claimed that he had been bitten by bedbugs and now had serious health problems and needed medical attention. Again, a link to Google Drive supposedly containing evidence was attached. In this case, the zip file was password-protected and the password was included in the email.
It is standard practice to protect the malicious file with a password. In this way, the attackers try to make it more difficult for the detection mechanisms to recognise and deactivate the malware directly on Google Drive.
...and at the same time, reports from hotel guests
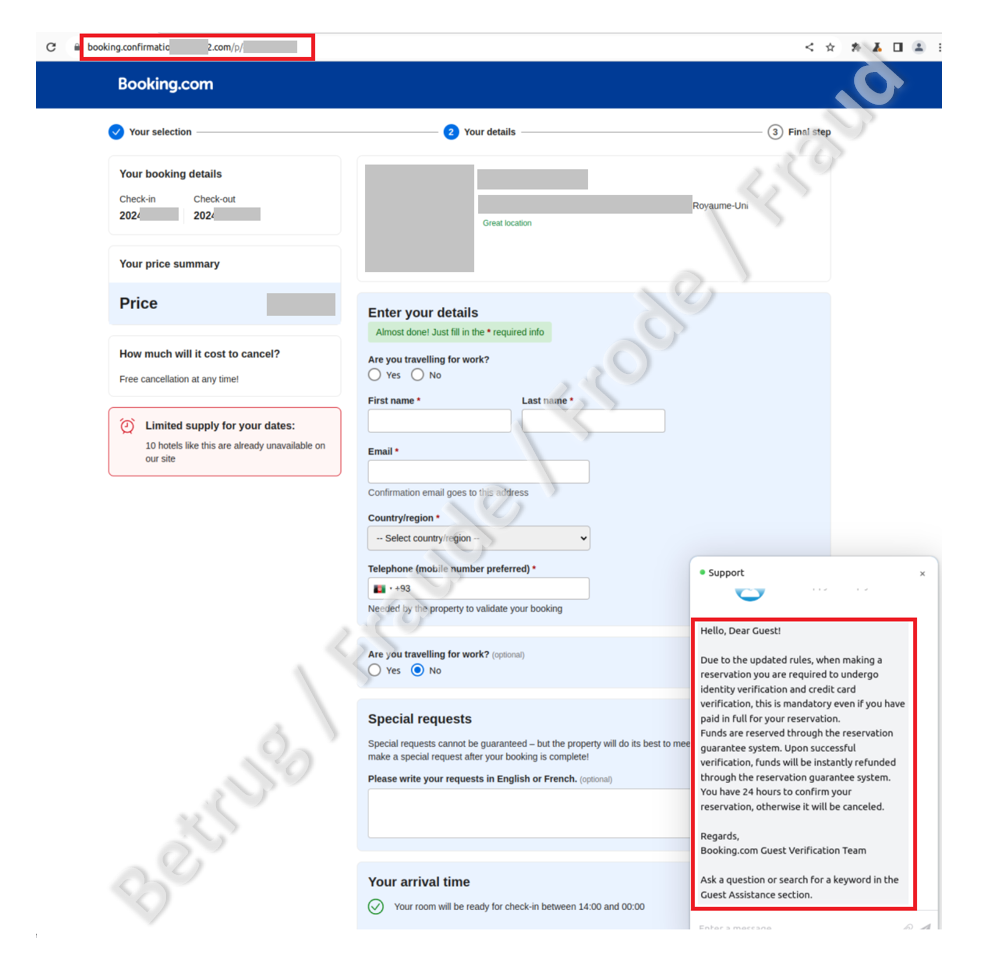
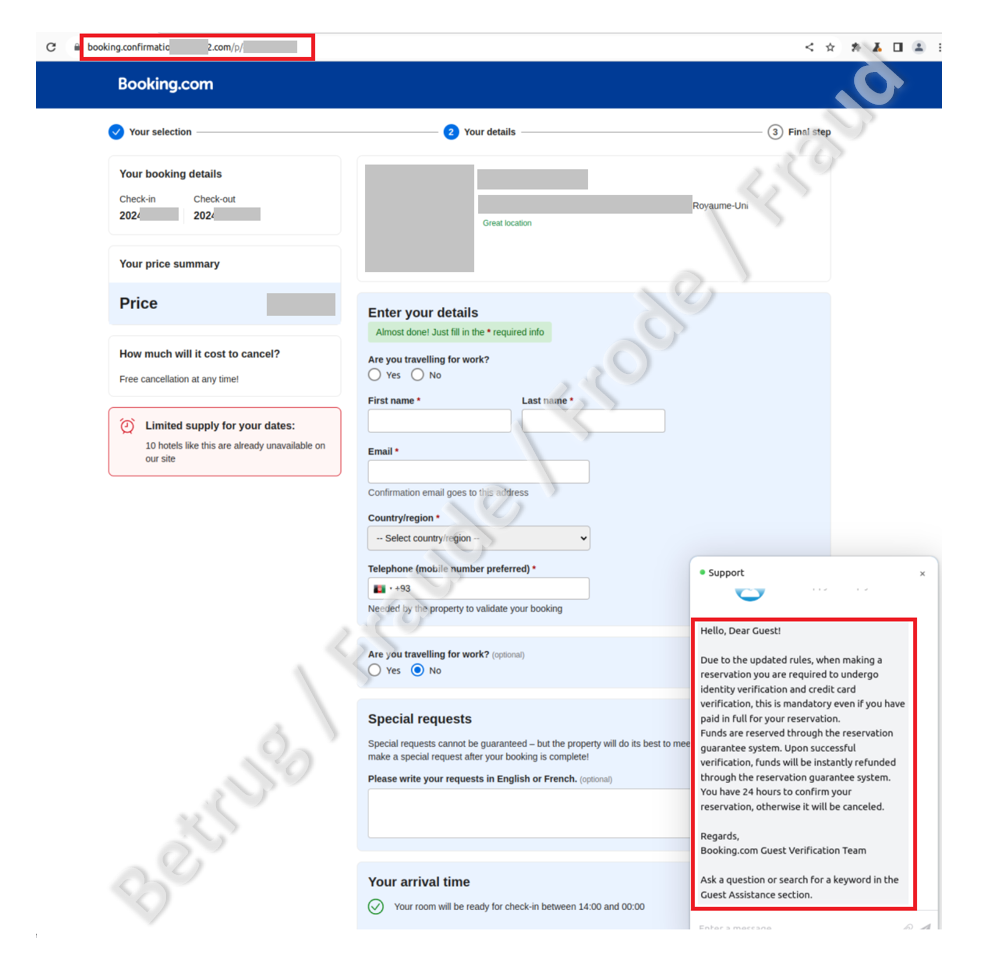
Reports about the use of the stolen data did not take long to arrive. Last week, the NCSC also received reports from people who had made a hotel reservation. Immediately after booking, they received a response from booking.com asking them to verify their credit card details via the link provided within 24 hours, otherwise the booking would be cancelled. The link led to a personalised phishing page with the correct reservation details. The data must have previously been obtained via the hotel's booking.com account.
Measures for hotels:
- If you suspect an infection, immediately take the computer offline and change your passwords for all online accounts from another, unaffected computer.
- Many malicious programs make significant changes to the system that cannot easily be reversed. Therefore, the entire system should be reinstalled if an infection is confirmed. Regular backups make it easier to restore your data.
- Hotels in particular have to open many documents sent by guests. However, executable files must not be opened under any circumstances.
- Always keep systems up to date.
- Consider a strategy in which computers for guest-related communications are separated from the rest of the network.
Measures for hotel guests:
- The usual rules on phishing apply, as explained in the last weekly review.
- Inform the hotel and the booking platform immediately if you receive such a phishing email.
Current statistics
Last week's reports by category:
Last modification 28.11.2023