04.05.2021 - The NCSC received a moderate number of reports last week. Aside from phishing attempts in the name of financial service providers and Swiss providers, ransomware attacks on QNAP devices remained a key issue. In the case of classified ads, there have been frequent reports of the scam variant in which the seller is first supposed to pay the buyer a fee. In a new variant of this type, the fraudsters even managed to hack into the seller's e-banking account.
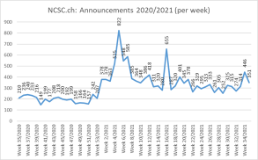
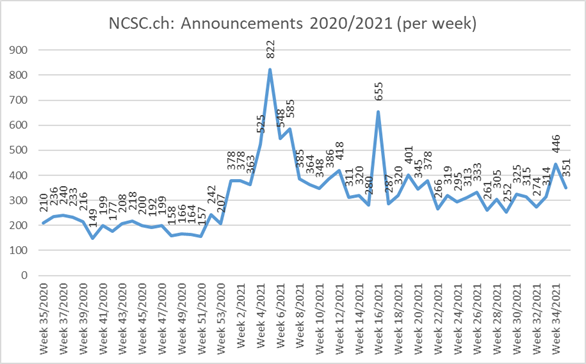
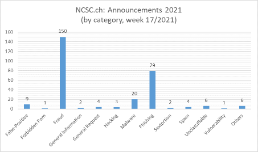
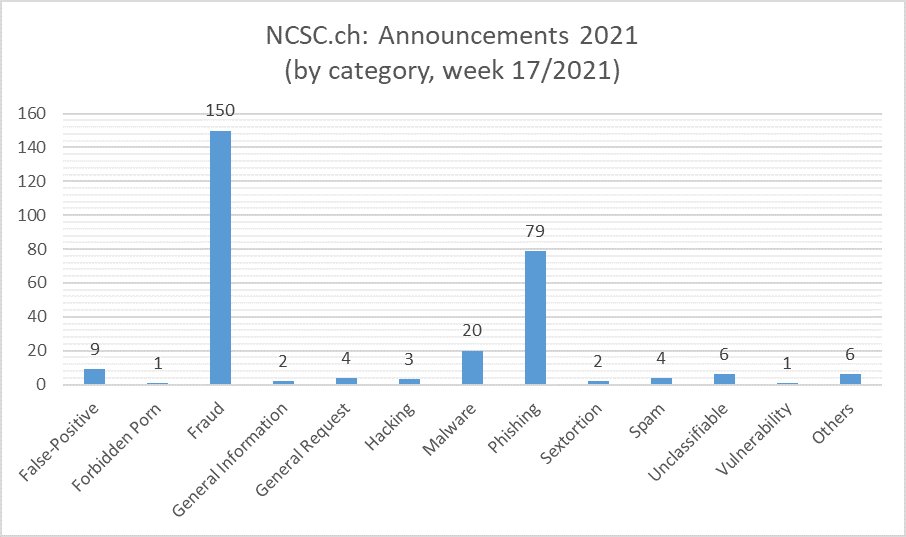
Current statistics
Still numerous reports of ransomware on QNAP NAS (network-attached storage) devices
Over the last two weeks, a total of 25 cases of encrypted QNAP NAS (network-attached storage) devices were reported to the NCSC. These attacks were described in detail in last week's review. If this has not already been done, the NCSC recommends updating Multimedia Console, the Media Streaming add-on and Hybrid Backup Sync as a matter of urgency, and generally keeping all device systems up to date. It is also advisable to install the latest version of Malware Remover and run a malware scan as a precautionary measure.
If such network-attached storage is directly accessible from the internet and the NAS is not up to date, it will merely be a matter of time before it is encrypted.
You can find further information on the QNAP website:
https://www.qnap.com/en/security-news/2021/response-to-qlocker-ransomware-attacks-take-actions-to-secure-qnap-nas
Classified ads – When you have to pay as a seller
Unfortunately, fraud attempts are commonplace on classified ad platforms. Aside from the classical variants, where non-existent goods are sold or goods are not delivered after payment, yet another approach exists: based on some sort of pretext, the seller is supposed to transfer money to the buyer, or to alleged third-party companies, even before the buyer has paid for the goods. In the latest variant, the fraudsters even managed to hack into the seller's e-banking account. How could this have happened?
The supposed buyer pretended that he wanted to save on transfer fees and would therefore use a free postal money transfer service. To this end, the victim received an ostensible email from the post office confirming that a transfer had been made. In order to transfer the money deposited there to the seller's bank account, the seller had to open the enclosed link to the fake website and enter his bank details, as well as the user name and password for the e-banking account. At the same time, the fraudster used this information to log on to the e-banking platform in question, thereby triggering two-factor authentication, with the sending of a text message code to the accountholder. The fraudster then contacted the victim and asked him to forward the code he had just received in order to confirm the bank transfer. Once the victim forwards this code, the fraudster has access to the account and can then make payments.
Be careful with demands from buyers!
Insist on shipping and transaction fees being paid by the buyer. Also write this explicitly in the advertisement. Never enter the login credentials and password for an e-banking account on a third-party website. Never pass on a code that you received via text message, for example, to a third party.
Last modification 04.05.2021