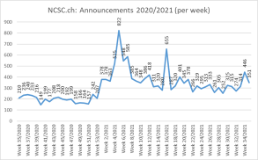
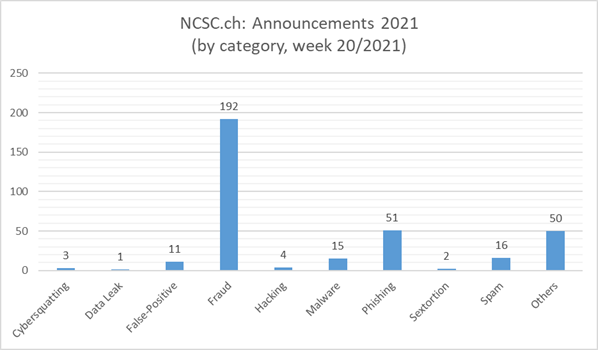
26.05.2021 - Last week, the NCSC received an average number of reports. Notable reports included those on CEO fraud, a new approach to classified ad scams and a well-known method of spreading malware.
Current statistics
CEO fraud – how certain websites help attackers
"Can we make a payment today?" or "What is our limit for urgent payments?" are common questions asked in emails from the supposed boss to a company's finance department in cases of CEO fraud. A credible story is used to persuade the person being contacted to make an allegedly urgent payment. The attackers obtain information about the company structure as well as the names and roles of the employees in advance. Information on company websites, where the team is presented and details, including email addresses, are listed, is particularly helpful for fraudsters.
Some company websites, however, provide even more information which is of interest to fraudsters. In two cases reported to the NCSC last week, for example, fraudsters took advantage of the fact that companies published a list of worldwide distribution partners on their website – again with the corresponding contact email addresses. Under the pretext that the import quota from China had already been used up, the companies were asked to order and also pay for a packaging machine in their name. Needless to say, the alleged Chinese company did not exist and the money would therefore go directly into the fraudsters' account.
Exercise caution when publishing data about team members and partners. In particular, do not publish contact details such as email addresses.
If you publish such data on your website, make your employees aware of such fraud attempts.
When sellers are asked to pay
In week 17, the NCSC discussed fraud attempts on classified ad platforms in which sellers are asked to transfer money to the buyers or to supposed third-party companies based on some pretext or other, before the buyer pays for the goods. These are usually purported shipping fees that are to be prepaid by the seller. In a new variant, victims are told to pay these fees by making a telephone call. They are asked to call a premium rate number for 20 minutes: at CHF 4.90 per minute, the final cost of the call is CHF 98.
Be careful with demands from buyers. Insist on shipping and transaction fees being paid by the buyer. Also write this explicitly in your advertisement.
Spreading malware – the trick using old emails
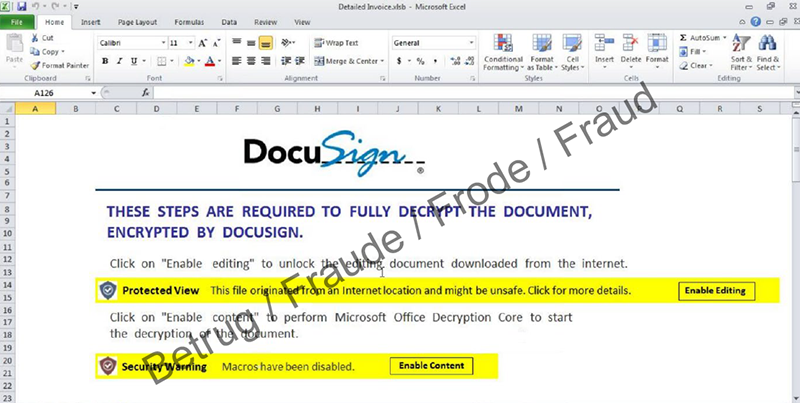
Emotet malware already tricked victims into opening a document by putting the document or a link to it in an email that contained parts of previous emails known to the victim. The Emotet network was disabled by law enforcement authorities at the beginning of this year. However, this was by no means the end of this practice, which is also being used to spread other malware families. Last week, the NCSC received several reports of QakBot malware, which also uses old emails known to the recipient and then sends them to the recipient again, with the addition of a link to a malicious Microsoft Office document. Since the emails look familiar to the recipients, the victims are more likely to click on the link. QakBot has a so-called "email collector module" that uses stolen access data to extract emails from the victim's Microsoft Outlook client, uploads them to a remote server and then uses them for further attacks.
A typical feature of QakBot is that the opened malicious document displays instructions on how to activate the macro function. The malware uses this to install itself on the computer. For this reason, this function should always be deactivated.
Malicious emails can also come from known senders. Be careful if previous messages are suddenly used out of context, for example. Malware is often distributed through Office documents. In most cases, the macro function is exploited. Never give permission to activate the macro function.
Last modification 25.05.2021