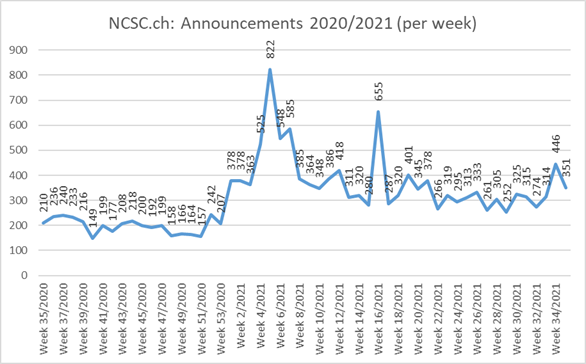
13.07.2021 - The number of reports received by the NCSC fell slightly last week. In two cases, different approaches were used to try to persuade victims to download malware. In order to prevent the software from being analysed, these files can often be downloaded only once.
Alleged copyright infringement leads to malware infection
An association was informed about a purported copyright infringement via the contact form on its website. Copyright-protected images were allegedly being used on the website. A major lawsuit for USD 150,000 was threatened. The images involved could be seen by clicking on the attached link.
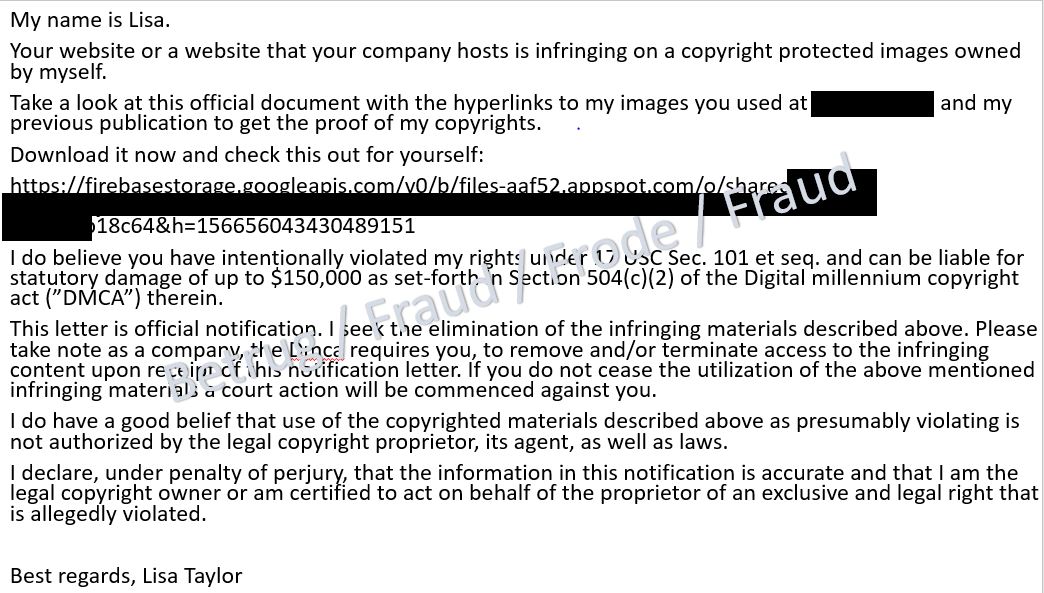
The link in question, however, led to a download in Google Drive. Unfortunately, the file could no longer be downloaded as it was already deactivated. The NCSC assumes that the file contained malware.
The NCSC regularly analyses such malware files as this often reveals a lot about the attackers. The attackers defend themselves against these analyses by delivering the files only to certain web browsers or operating systems, by deactivating the link after the initial access or by limiting access time. The reasons why the file could no longer be accessed in this case were not clear.
• Never click on links which you receive in unsolicited emails.
• Do not download any unknown files from the internet.
• If you have clicked on such a file, you should have your computer checked by a specialist.
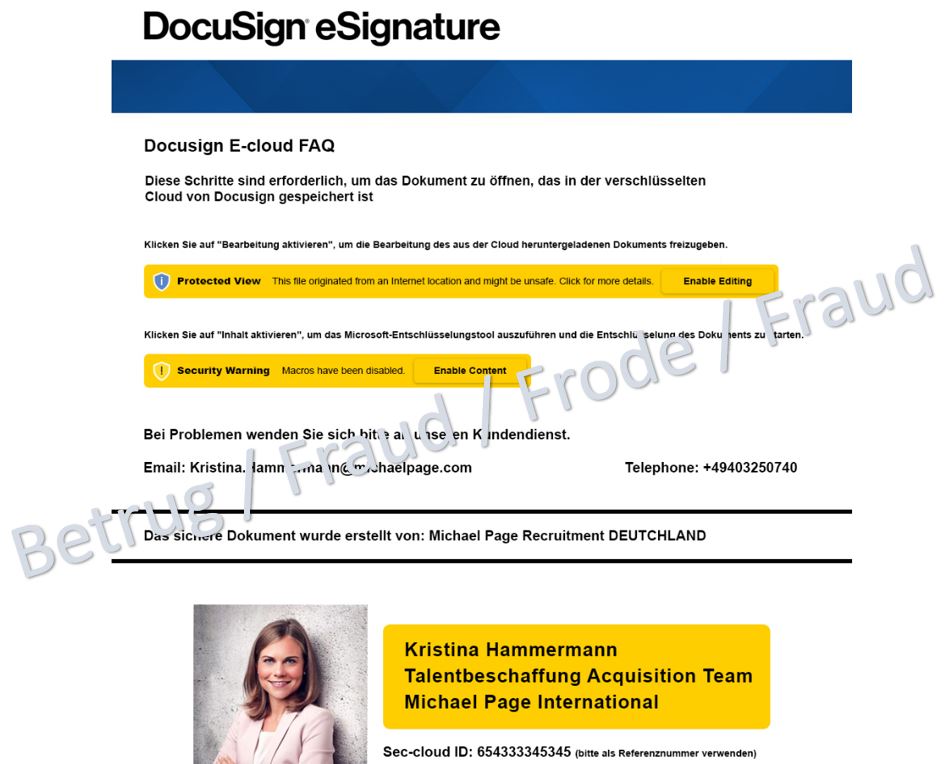
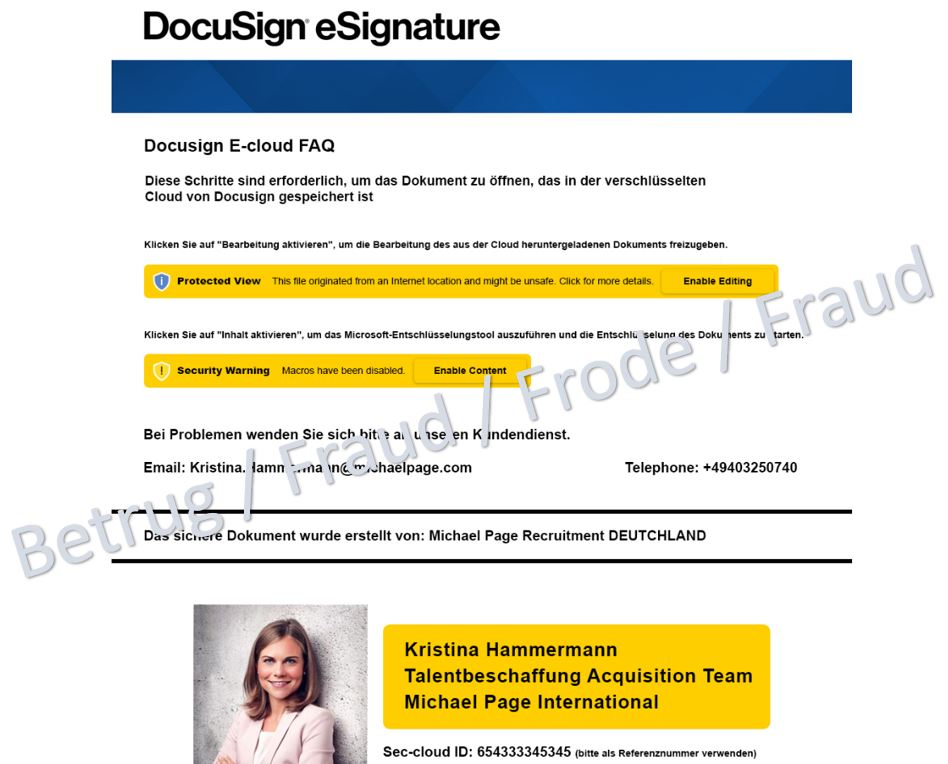
A banking Trojan lurking behind an attractive job offer
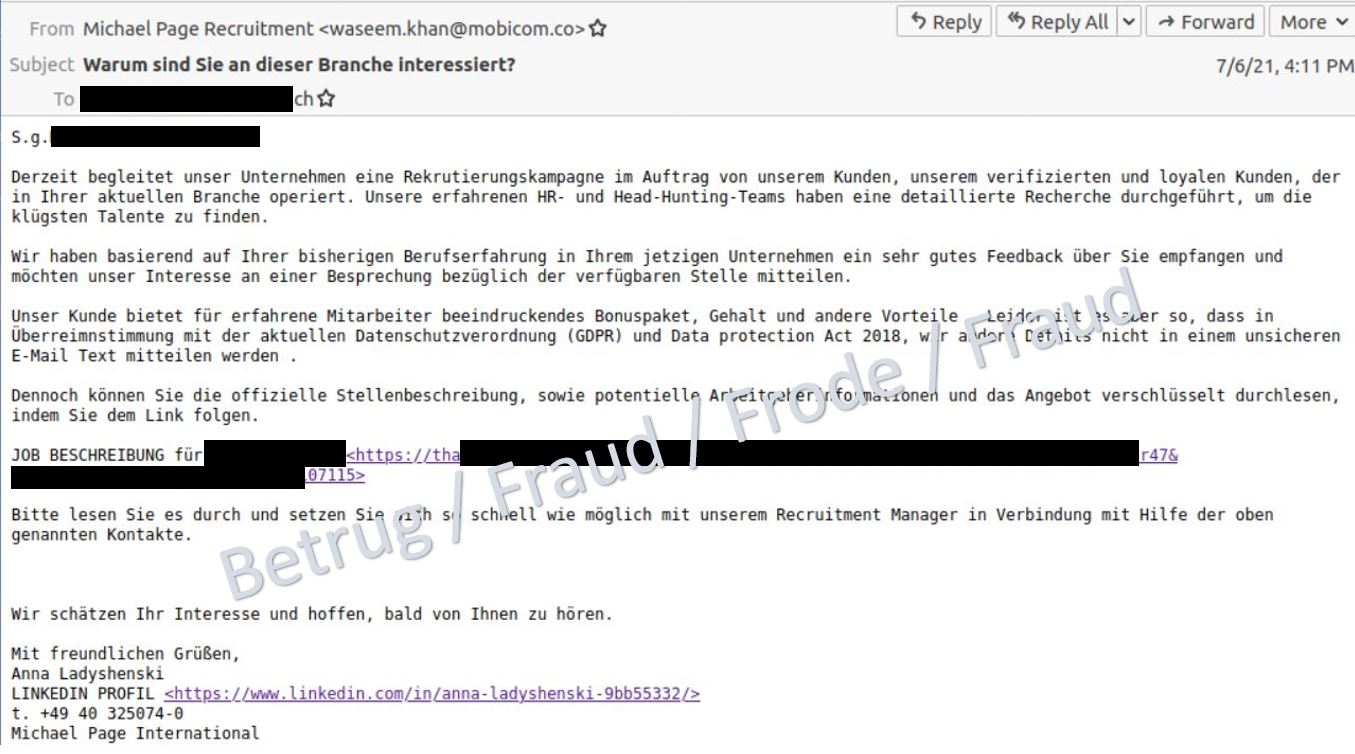
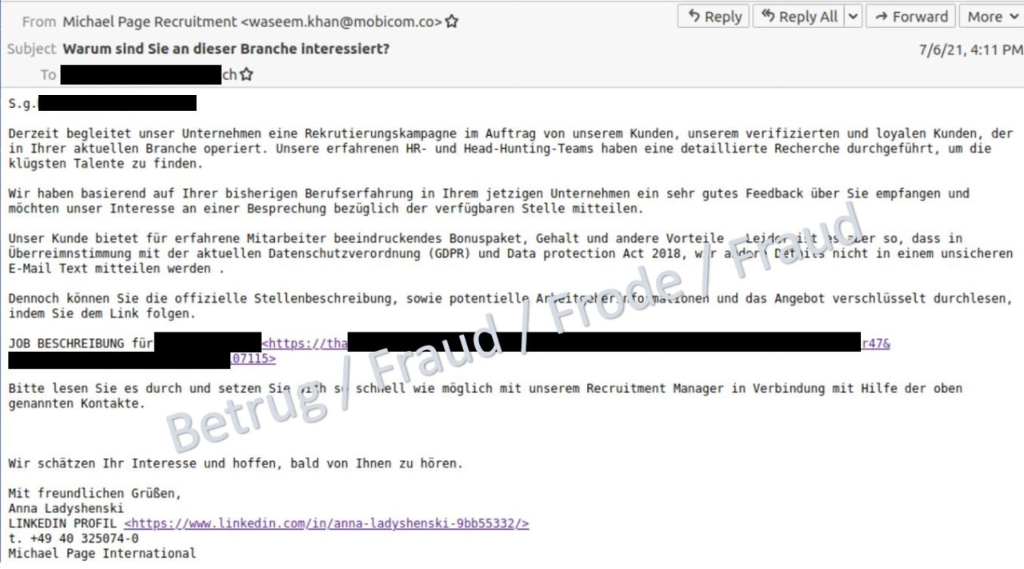
In another case, the victim was lured with an unsolicited email containing a tempting job offer from well-known headhunter Michael Page. However, the headhunter's sender address was bogus, and the contact details provided were also incorrect.
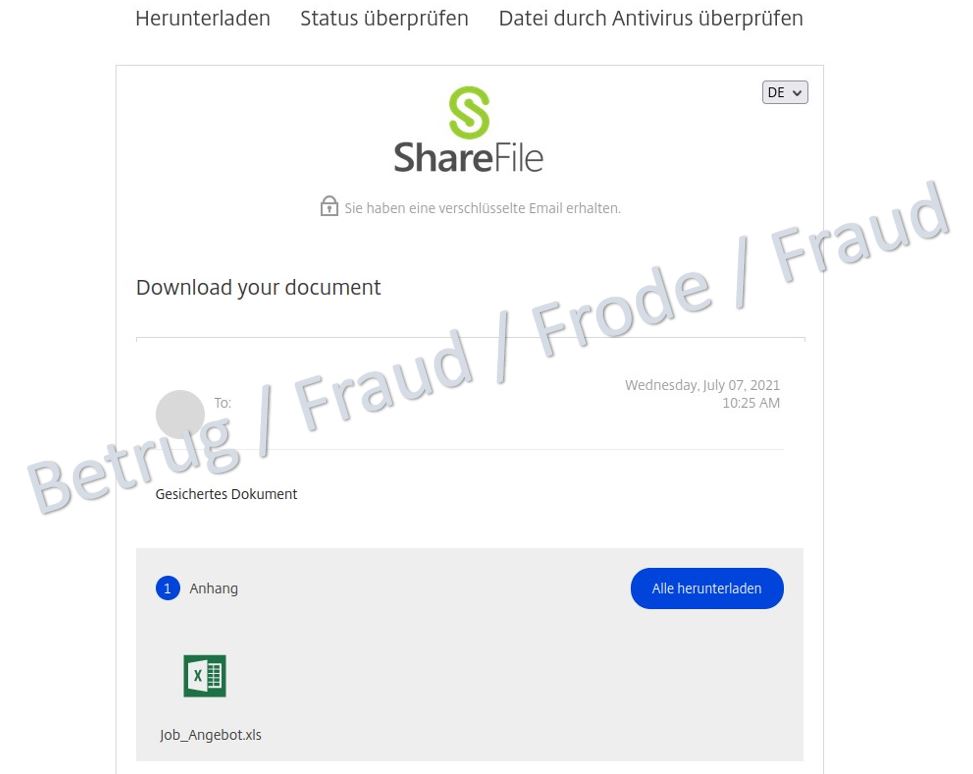
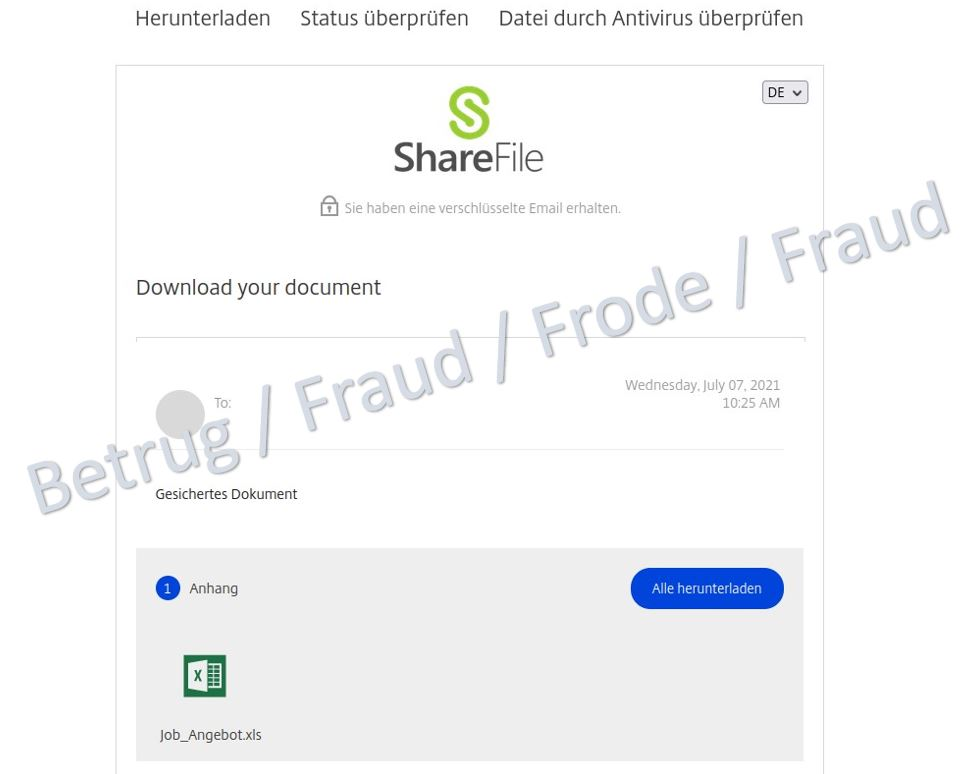
Apparently, due to European data protection laws, the details of the alleged job offer could not be included directly in the email. The victim was therefore supposed to download the information via a link. The link leads to a file share service where an Excel document with the name "Job_Angebot.xls" appears to be available.
When downloading the document, however, a ZIP file appears. Another document is packed in the ZIP file. When this document is opened, malware known as a banking Trojan ("Gozi", also known as "Ursnif") is installed in the background using macros.
The NCSC assumes that the attackers obtained the information about the victim from leaked data from the victim's LinkedIn account. LinkedIn has been the victim of hackers on several occasions.
• Do not respond to unsolicited emails.
• If you feel that the information is legitimate, you should contact them directly, for example by telephone or via the contact information published on their official website.
• If you have clicked on such a file, you should have your computer checked by a specialist.
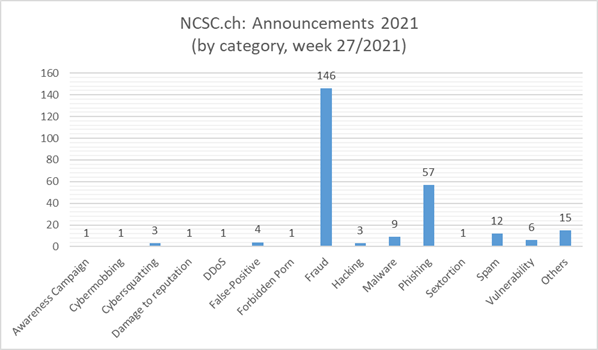
Current statistics
Last modification 13.07.2021