10.08.2021 - The NCSC once again received an average number of reports last week. A report on a cloned website revealed a new modus operandi in which the customer behaviour of Swiss companies is analysed. Moreover, further attempts were made to convince victims to install malware by phoning about alleged parcel deliveries. To do this, the attackers pretended to be from Swiss Post and did not use fictitious company names like in the past.

Unknown people are collecting data on the customer behaviour of Swiss companies
A special case was brought to the attention of the NCSC last week. Anyone who searched on Google for a certain flower shop in Bern was first shown an advertisement that, rather than indicating the domain of the shop in question, showed an identical address with a "1" appended at the end. Instead of the correct website "www.blumenmaarsen.ch", an ad for www.blumenmaarsen1.ch was displayed. Clicking on this website opened an identical copy. Not only were all the web pages present, it was also possible to order and pay for flowers. But anyone who thinks that the site was created for the purpose of stealing credit card details is wrong. The payment process was also an identical copy. Any payment was actually made to the correct payment service provider and if someone had gone through the entire process, the flowers ordered would actually have been delivered at the end and the florist would have been paid for them.
An investigation of the website revealed that additional code that originated from the US company "builtwith.com" was integrated on the cloned site. Among other things, this company specialises in analysing the visitor behaviour of e-commerce sites. The NCSC did not examine in detail which data was collected in each case. It is still unclear who ultimately cloned the websites and has an interest in the customer behaviour of various Swiss companies. Further investigations by the NCSC additionally revealed that this was not an isolated case. Websites of companies in other sectors were likewise cloned – in each case with the addition of a number to the address – and here too the scripts of "builtwith.com" were inserted.
Following the complaint made by the shop concerned and the intervention of the NCSC, the Swiss registry Switch was then able to deactivate the site.
- In the case of many Google searches, advertisements are first displayed before the actual hits. These hits are marked accordingly as "ads" and the originators pay to have them listed as the first hits. As the above case shows, Google ads can be misused.
- Therefore, be vigilant when conducting a Google search, especially in the case of ads.
- As a website owner, you should check from time to time whether the site is found and rendered correctly by search engines – reputable websites are sometimes misused to give dubious offers a better position in the search list.
An old scam in a new guise: calls now announce a delivery in the name of Swiss Post
Back in week twelve of this year, the NCSC reported on a variant in which attackers pose as a parcel transport company. They call victims and pressure them to sign supposed shipping documents that were previously transmitted via email, in an attempt to get the victim to open a PDF document. However, malware is hidden behind the link for the PDF document. Different kinds of malware can be sent. In most cases, it is an e-banking Trojan. Until now, the attackers used the names of fictitious companies such as "Swiss Express Service" (or similar) and also created the corresponding domains via which the communication took place and the malicious documents were delivered. However, it seems that these fictitious companies are increasingly being met with scepticism by the victims, which reduces the attackers' chances of success. This is likely to have been one of the reasons why the attackers changed tactics last week and now contact the victims in the name of Swiss Post.

The emails also have the Swiss Post look, which makes it more difficult for the victim to recognise the attack. However, the Google Docs link provided should then set off alarm bells. Swiss Post would never store documents on Google Docs; it would use its own infrastructure for this purpose. Reputable companies always make documents available in their customer area and not on internet platforms.
- Be wary of unsolicited emails.
- First clarify with senders whether they actually sent you the email with an attachment. It is best to do this by telephone, but do not use the telephone number in the email; look for the number on the company's official website instead.
- Never let yourself be pressured into clicking on a link, opening a document in an email or revealing personal data.
- Block all email attachments that could contain macros, e.g. Word, Excel or PowerPoint attachments with macros.
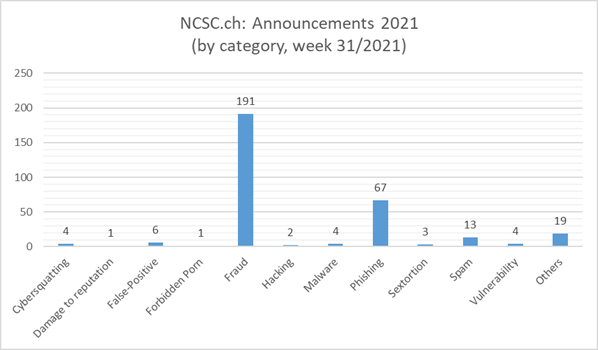
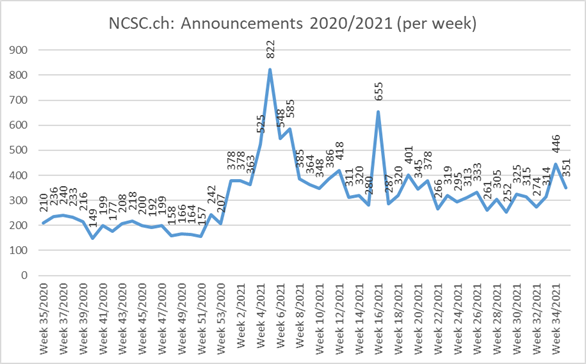
Current statistics
Last modification 10.08.2021