16.11.2021 - The number of reports received by the NCSC increased last week. Attacks on Microsoft Exchange Servers continue to be reported. In addition, the NCSC received reports of various variants of advance fee fraud that differ from the usual modus operandi. A type of fraud was also reported in which the Facebook Mentions function is misused to carry out targeted phishing attacks.

Different "modern" and "customised" variants of advance fee fraud
A large number of advance fee fraud emails are reported to the NCSC. In such cases, the victim is promised a large lottery prize or a significant inheritance. If the recipient responds to such a message, various reasons are given to request an advance payment, e.g. fees, legal costs or profit tax. Recently, however, variations that deviate from this traditional approach have become more frequent. These attempts are relatively easy to detect.
The customised variant – advance fee fraud in connection with real estate advertisements
In one variant, which has been reported several times in recent months, the fraudsters respond to a real estate advertisement. In this case, a supposed soldier who had been stationed in Afghanistan and is now looking for a new home in Switzerland expresses interest in a property. After sending numerous confidence-building emails in connection with the future sale, the purported soldier steers the discussion towards assets he supposedly possesses and which he wants to invest in Switzerland. The real estate owner is promised a large sum if he helps him with the investment. As with other variants, the victim will sooner or later be expected to pay fees. As the story is fictitious, neither the soldier nor the money exists.
The modern variant – a chance to receive a large amount of bitcoin
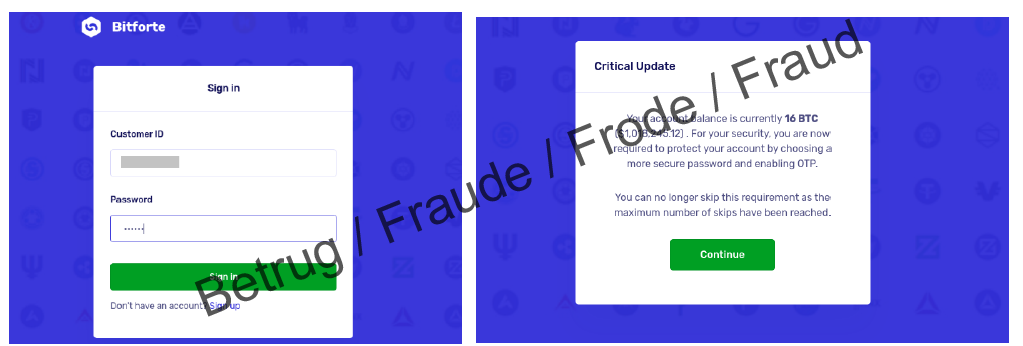
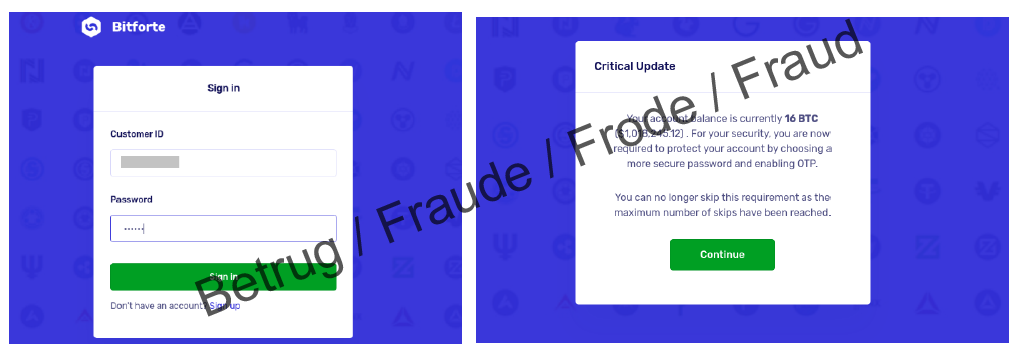
Advance fee fraudsters adapt to current trends. In a recent variant, which was reported to the NCSC several times last week, an email is sent that looks as if it has been sent to the recipient by mistake. The email talks about a large sum in bitcoin that the sender has invested on a platform for the recipient. The total amount is over CHF 1 million and the email contains a username and password. The attackers hope that the recipient of this "misdirected" email will be greedy and attempt to withdraw the money.
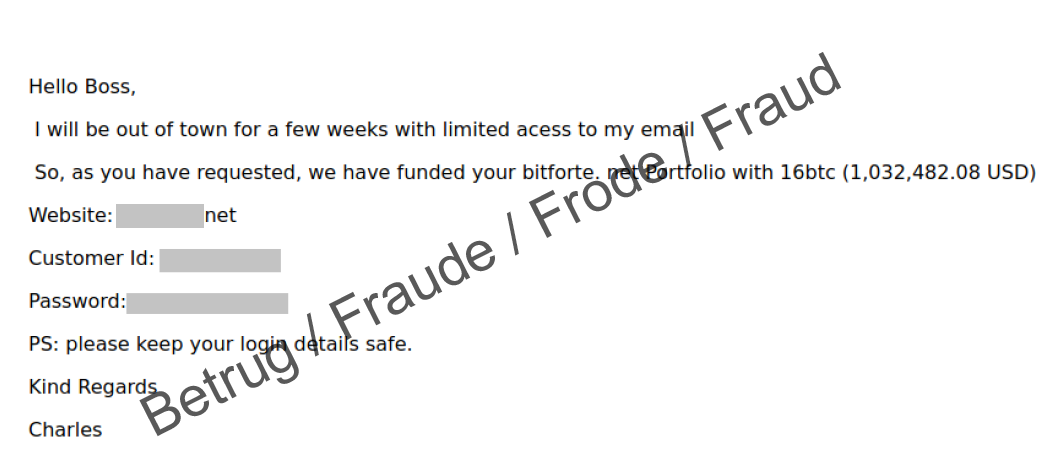
The login details actually work and the user is asked to secure the account with a second factor. After successfully logging in, the account shows the vast assets. It is even possible to withdraw a small amount of around CHF 5. However, after this, the situation then changes. In order to be able to carry out any further transactions, various fees are charged. The trap begins.
- Ignore such emails and under no circumstances pay the fees demanded.
- In general, be sceptical if you receive emails that require action on your part and that carry a threat of consequences (loss of money, criminal charges or criminal proceedings, blocking of an account or card, missed chance, misfortune) if you do not do what is required.
Facebook Mentions function misused for fraud
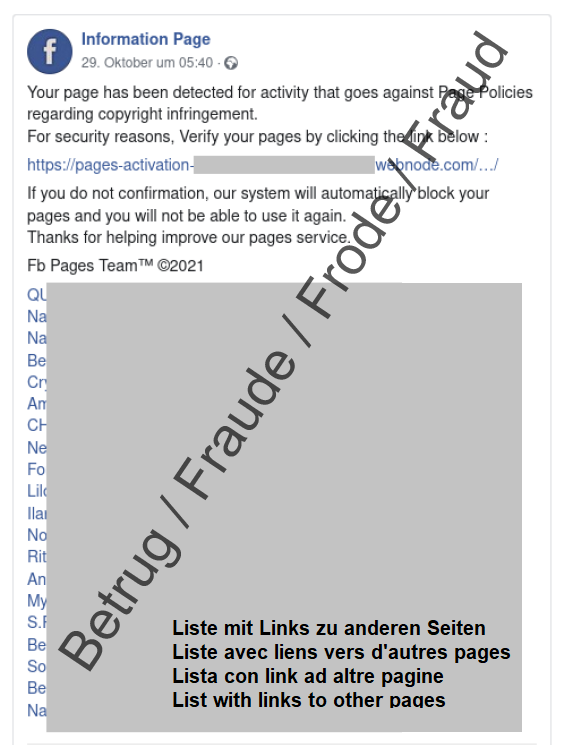
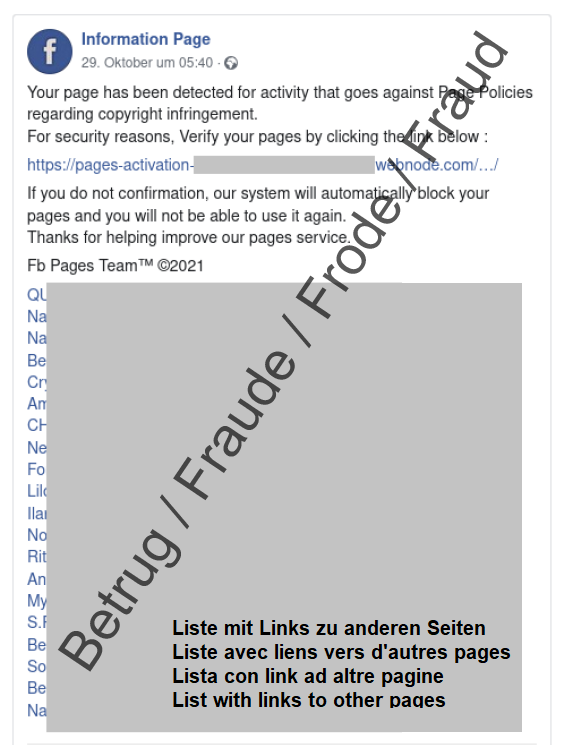
The Facebook Mentions function allows an accountholder to see which other Facebook pages have links to his or her own page. This function was very specifically exploited for phishing attacks last week, as a case reported to the NCSC shows.
On a Facebook phishing page created by the attackers, the perpetrators add various links to other Facebook pages at the bottom. All of these linked accounts appear in the account owner's "Mentions" section. If a victim now uses this function and wants to view the pages on which he or she is mentioned, he or she will inevitably end up on the fraudulent page.
In the current case, the fraudulent page claimed that there was a copyright problem. In order to solve the problem, the user had to click on the link and then enter his or her Facebook login details for verification.
- Be suspicious when you come across pages like this and take a close look at the link.
- Never enter a password on a page that you have opened via a link.
Current statistics
Last week's reports by category:
Last modification 16.11.2021