21.12.2021 - Last week, the NCSC again received a significant number of reports. The number of dodgy online shops is on the rise in the run-up to Christmas. In addition, emails that use old email exchanges known to the recipient are once again being sent, with the aim of spreading malware.

The number of dodgy online shops is on the rise in the run-up to Christmas
Especially in the run-up to Christmas, many people scour the internet for exclusive gifts that are also as inexpensive as possible. Unfortunately, however, some offers fail to live up to their promises. Especially in the pre-Christmas period, the NCSC has been receiving numerous reports of suspicious shops that do not deliver the products promised and already paid for. A total of 18 dubious shops were reported to the NCSC last week. While admittedly the intention is not always fraudulent – in some cases, the shops are simply unable to deliver the goods on time – in many cases, the shop turns out to be fake and the money is lost.
- Before any purchase, check out the online trader in detail.
- Use customer feedback (reviews) to build a picture of the seller. You can find this feedback by searching for the name of the webshop plus "reviews". Bear in mind that reviews can also be bogus.
- Alarm bells should ring if an offer is obviously too cheap.
- Check whether the seller has an "About" section and whether this is complete and plausible. For example, does the seller give a plausible contact address, a correct telephone number or email address, and a commercial register number?
- Further information can be found on:
«Buying and selling online»
Emails that refer to old email exchanges in circulation once again
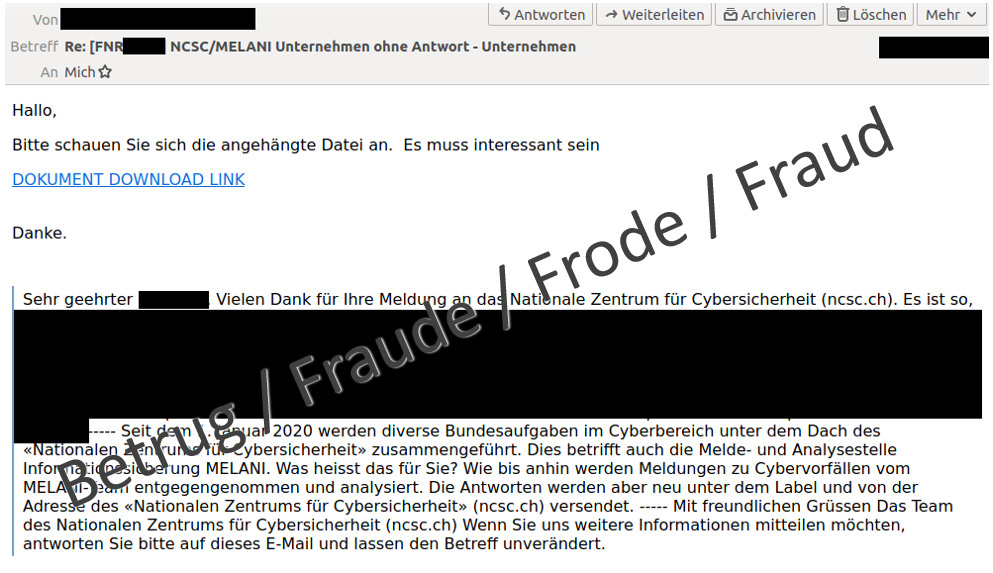
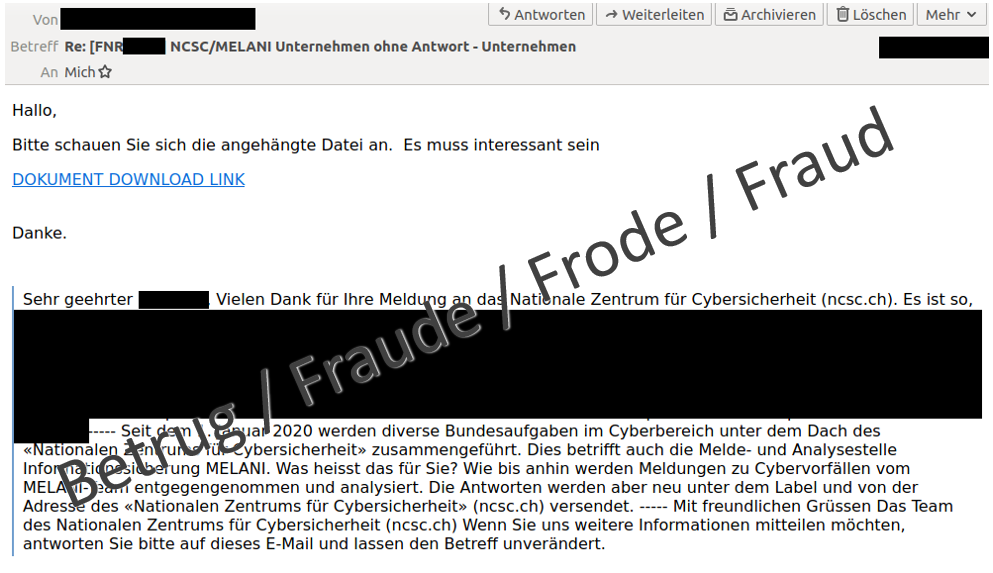
Last week, the NCSC received a strange email. It appeared that someone was replying to an incident that they had reported last year and received a reply from the NCSC. The new email stated above the response we had given at the time that we should click on a link to download a document with more information about the incident. Naturally, this approach looked familiar to us. It is a way of spreading malware. The attackers refer to familiar email texts of the recipients to lure them into clicking on the link and then on the malicious document or file. A link to the malware Quakbot, also known as Qakbot or Qbot, is hidden behind lines of text such as "Please take a look at the attached file", "Good morning, please read this as soon as possible" or "DOCUMENT DOWNLOAD LINK".
Since the fraudsters used old communications, they must have had access to the sender's email account. Therefore, the NCSC immediately warned the sender that his email account was compromised, which he confirmed a short time later. There had been a problem with his provider.
Last week, we received several reports about Quakbot and compromised Exchange servers.
- Malicious emails can also come from apparently known senders. Be careful if previous messages are suddenly used out of context, for example.
- Malware is often distributed through Office documents. In most cases, the macro function is exploited. Never give permission to activate the macro function.
Current statistics
Last week's reports by category:
Last modification 21.12.2021