28.12.2021 - Last week, the NCSC again received a significant number of reports. Some of the most frequent reports to the NCSC this year concerned bogus parcel notifications. Malware was likewise distributed using this method last week. For the first time, the NCSC also received a report about a scam on a carpooling portal.

Bogus parcel notifications – malware is also distributed
Some of the most frequent reports to the NCSC this year concerned bogus parcel notifications demanding fees of some sort. After clicking on the link, victims are either taken to a phishing site where they are asked to enter their credit card details or to a subscription scam where they can win an iPhone, for example, and thus unwittingly sign up for a multi-year subscription. As people have been ordering more online since the beginning of the pandemic, there is a higher probability that the recipient is actually waiting for a parcel and falls for the scam (weekly review 23).
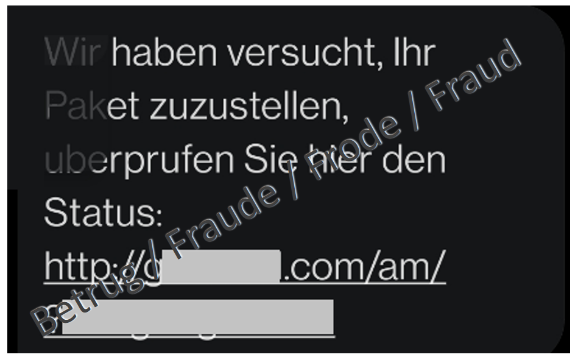
Attackers who distribute malware also use this method and send fake text messages stating that a parcel is on its way or has been lost. Among other things, they use the following texts plus a link. The sample texts are in German, as the attacks in the case at hand were mainly aimed at victims in German-speaking countries.
- «Hallo, es tut uns leid, Ihnen mitzuteilen, dass wir Ihr Paket verloren haben»;
- «Wir haben versucht, Ihr Paket zuzustellen, uberprufen Sie hier den Status»;
- «Ihre Lieferung ist auf dem Weg, verfolgen Sie sie»;
- «Hallo, wir warten auf eine Aktion von Ihnen, um Ihr Paket zuzustellen».
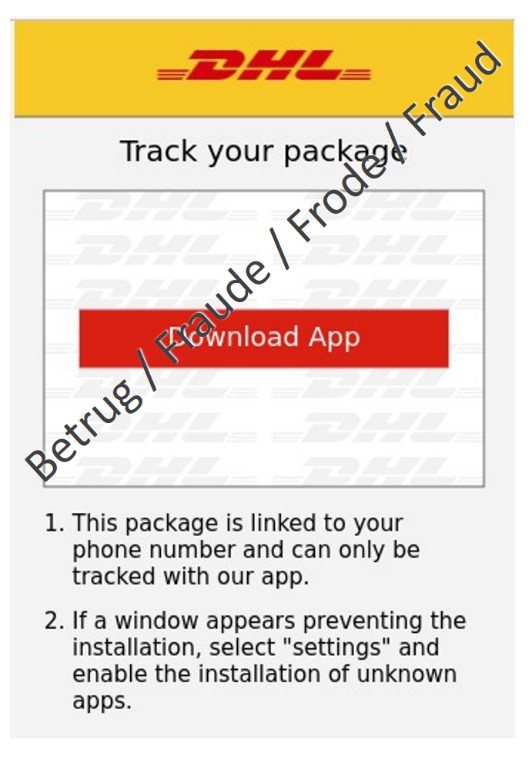
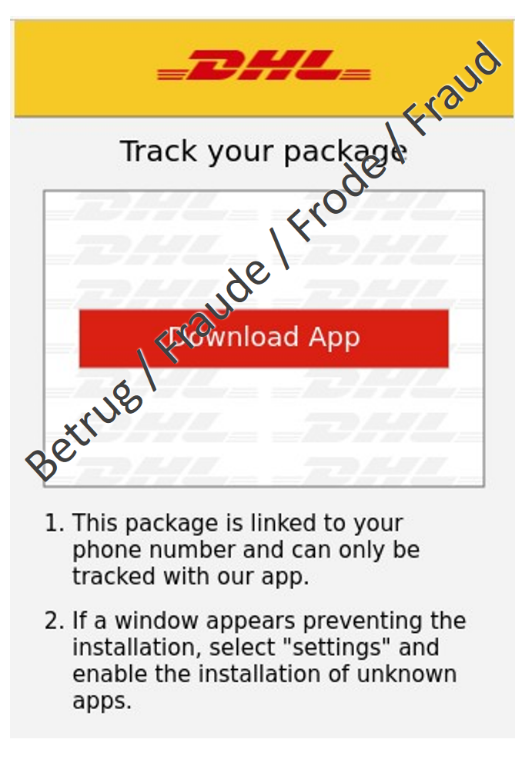
Anyone who clicks on the link in the text message is taken to a fake website, where the victim is prompted to download a DHL app. In reality, however, it is a malicious APK (Android Package Kit) file. The page explicitly asks the victim to enable the installation of apps from unknown sources in the settings.
Among other things, the malware can read incoming text messages on the mobile phone, send text messages, read out contacts and even make phone calls. Such malware aims to intercept one-time passwords sent by text message and send them to the attacker. Similarly, infected devices can be used to send further fake text messages with a link to the malicious app, thereby spreading the malware with a snowball effect.
- Do not install any software that is offered outside the operating systems' official stores.
- In particular, you should not install any software received via a link in a text message or other messenger service (WhatsApp, Telegram, etc.).
- If you nevertheless installed such software, you should have the device checked by a specialist and should not carry out any banking transactions or online shopping. Do not enter any passwords either.
- Restoring the factory settings on the infected device is almost the only way to remove such malware.
Looking for a low-cost ride – paid a lot of money
There are various portals on which car drivers can look for passengers in order to better utilise the car and thus save CO2 and certainly also to earn a small fee. However, this good idea also seems to attract fraudsters, as demonstrated by a case reported to the NCSC last week. The person who reported the case was looking to carpool and also found a suitable driver. After having made contact, mobile phone numbers were exchanged as usual and an amount of EUR 17 was agreed on for the ride.
However, the victim then received a supposed reservation confirmation, which appeared to have come from the portal operator. It confirmed the journey and also the agreed amount of EUR 17. However, closer analysis of the link revealed that it did not lead to the pages of the portal, but rather to a website that the fraudster had set up specially. After entering the details, almost CHF 500, instead of the agreed EUR 17, was debited to the victim's account. Thanks to a quick reaction, however, it was still possible for the payment to be stopped.
- Never enter personal data in a form that you opened via a link in an email.
- As soon as you realise that you have entered your password on a phishing site, change this password for all services where you use it.
- If you provided credit card details, contact your credit card company immediately to have the card blocked.
Current statistics
Last week's reports by category:
Last modification 28.12.2021