04.01.2022 - In the last weekly review of 2021, the NCSC looks back at the 21,000 reports received over the last 12 months. We would like to take this opportunity to thank you for all your reports. They help us to better assess the situation in cyberspace and warn potential new victims more effectively.
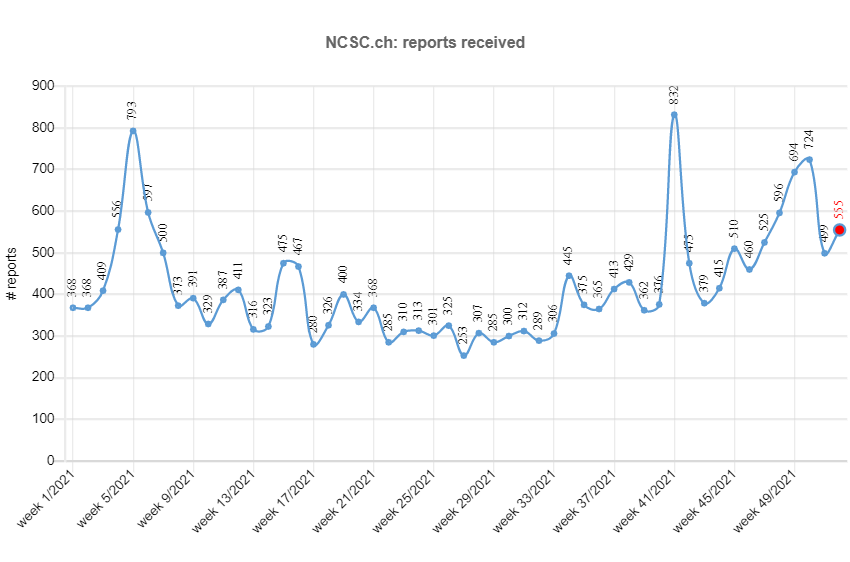
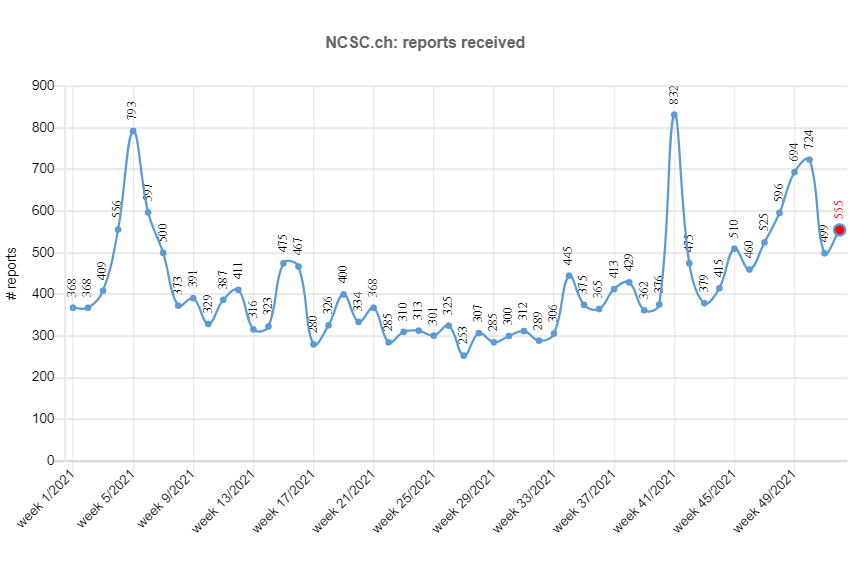
The NCSC received an impressive 21,000 reports this year, roughly double last year's number. One reason for this sharp increase is likely to be the fact that the NCSC's reporting form was updated and simplified at the end of 2020, and that it was more prominently placed on the NCSC homepage.
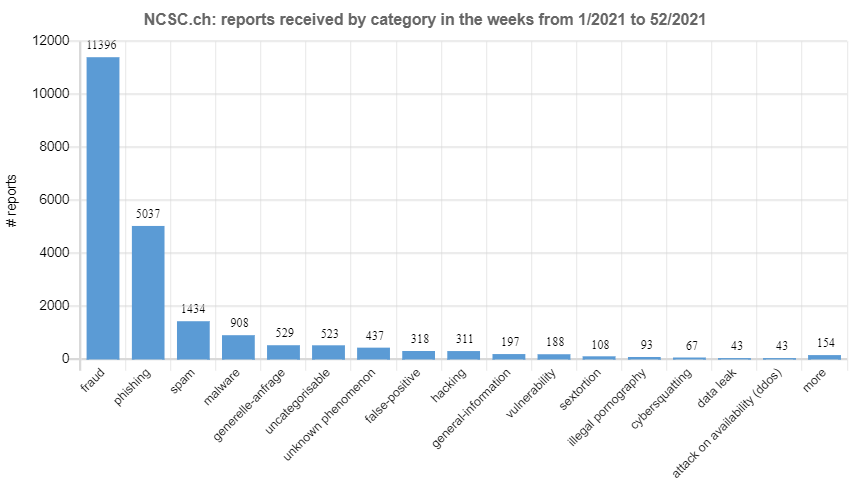
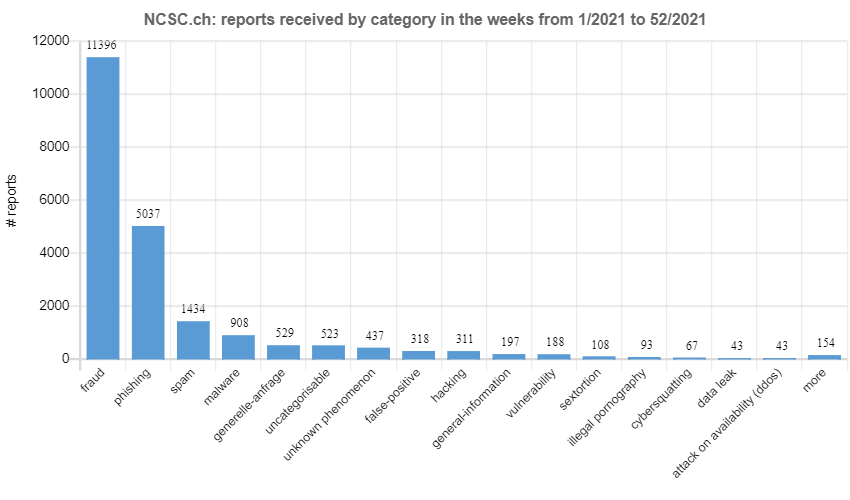
Most frequently reported: fraud
Another reason for the high number is the multiple large-scale fraud attempts using fake sextortion or phishing. Besides these two phenomena, the NCSC received the most reports about advance fee fraud and emails advertising dubious investment offers.
Greatest number of reports: 832 in one week
As regards malware, almost half of the reports concerned FluBot. This was due to a wave of fake text messages in weeks 41 and 42, which tried to fool recipients into installing a malicious Android mobile app containing FluBot malware. This led to the highest number of reports in 2021, with 832 reports per week.
Greatest potential for damage: ransomware and investment fraud
Phenomena with huge potential for financial damage are investment fraud and ransomware. This year, the NCSC received 161 reports on ransomware, as opposed to 67 last year. In spring, for example, the NCSC received numerous reports of the Qlocker ransomware being used in attacks on network attached storage (NAS), which is predominantly used by private individuals. A total of 44 reported cases were attributable to Qlocker in the past year.
In the vulnerability category, in addition to the current Log4j vulnerability, reports last year mainly concerned exchange servers. These vulnerabilities were used to distribute malware, for example. Links to malware are added to intercepted emails, which are then sent once again to the recipient. By using a trusted sender, the fraudsters hope to fool the recipient into opening a document.
Attacks used a combination of different phenomena
A noteworthy development this year is that fact that attackers have tried to combine different phenomena. For instance, people advertising on classified ad platforms were diverted to phishing sites. Adverts on property websites were suddenly answered by someone claiming to be a soldier posted to Afghanistan, who wanted to invest his assets in Switzerland. And more and more fraudsters in classic romance scams try to convince their victims to invest their money on dubious platforms. What all these variants have in common is the fact that the fraudsters initially use subliminal contact to try and gain the victim's confidence.
These are just a few examples of the numerous reports we received. We would like to take this opportunity to thank everyone who sent us reports. They help us to better assess the situation and to accompany our warnings with concrete examples.
We thank you for your trust and support, and wish you a virus-free new year, in both the digital and the physical world!
Current statistics
Last week's reports by category:
Last modification 04.01.2022